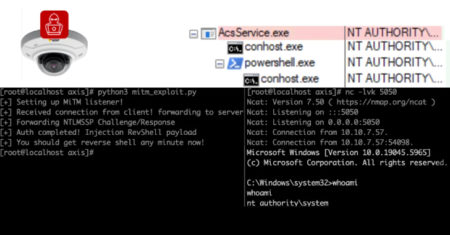
Cybersecurity researchers have disclosed multiple security flaws in video surveillance products from Axis Communications that, if successfully exploited, could expose…
Development
Microsoft has released an advisory for a high-severity security flaw affecting on-premise versions of Exchange Server that could allow an…
Now that we are well into 2025, cloud attacks are evolving faster than ever and artificial intelligence (AI) is both…
Cybersecurity researchers have discovered a set of 11 malicious Go packages that are designed to download additional payloads from remote…
Python is everywhere in modern software. From machine learning models to production microservices, chances are your code—and your business—depends on…
The threat actors behind the SocGholish malware have been observed leveraging Traffic Distribution Systems (TDSs) like Parrot TDS and Keitaro…
HTML Injection might not grab headlines like SQL Injection or Cross-Site Scripting (XSS), but don’t let its lower profile fool you. This vulnerability can quietly erode user trust, spoof content, and open the door to phishing attacks that exploit your application’s credibility. For QA engineers, incorporating security testing, integrating strong content quality validation (CQV) practices
The post HTML Injection Explained: Types, Risks, and Prevention appeared first on Codoid.
#744 — July 11, 2025 Read on the Web JavaScript Weekly Vercel Acquires NuxtLabs — Vercel has acquired the company…
CVE ID : CVE-2025-8576
Published : Aug. 7, 2025, 2:15 a.m. | 21 hours, 55 minutes ago
Description : Use after free in Extensions in Google Chrome prior to 139.0.7258.66 allowed a remote attacker to potentially exploit heap corruption via a crafted Chrome Extension. (Chromium security severity: Medium)
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-8578
Published : Aug. 7, 2025, 2:15 a.m. | 21 hours, 55 minutes ago
Description : Use after free in Cast in Google Chrome prior to 139.0.7258.66 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: Medium)
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-24000
Published : Aug. 7, 2025, 5:15 p.m. | 6 hours, 55 minutes ago
Description : Authentication Bypass Using an Alternate Path or Channel vulnerability in WPExperts Post SMTP allows Authentication Bypass.This issue affects Post SMTP: from n/a through 3.2.0.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2023-41520
Published : Aug. 7, 2025, 6:15 p.m. | 5 hours, 55 minutes ago
Description : Student Attendance Management System v1 was discovered to contain multiple SQL injection vulnerabilities in createClassArms.php via the classId and classArmName parameters.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2023-41521
Published : Aug. 7, 2025, 6:15 p.m. | 5 hours, 55 minutes ago
Description : Student Attendance Management System v1 was discovered to contain multiple SQL injection vulnerabilities in createSessionTerm.php via the id, termId, and sessionName parameters.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2023-41531
Published : Aug. 7, 2025, 6:15 p.m. | 5 hours, 55 minutes ago
Description : Hospital Management System v4 was discovered to contain multiple SQL injection vulnerabilities in func3.php via the username1 and password2 parameters.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2023-41532
Published : Aug. 7, 2025, 6:15 p.m. | 5 hours, 55 minutes ago
Description : Hospital Management System v4 was discovered to contain a SQL injection vulnerability via the doctor_contact parameter in doctorsearch.php.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-51629
Published : Aug. 7, 2025, 6:15 p.m. | 5 hours, 55 minutes ago
Description : A cross-site scripting (XSS) vulnerability in the PdfViewer component of Agenzia Impresa Eccobook 2.81.1 allows attackers to execute arbitrary web scripts or HTML via injecting a crafted payload into the Temp parameter.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-8697
Published : Aug. 7, 2025, 7:15 p.m. | 5 hours, 34 minutes ago
Description : A vulnerability was found in agentUniverse up to 0.0.18 and classified as critical. This issue affects the function StdioServerParameters of the component MCPSessionManager/MCPTool/MCPToolkit. The manipulation leads to os command injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7195
Published : Aug. 7, 2025, 7:15 p.m. | 5 hours, 34 minutes ago
Description : Early versions of Operator-SDK provided an insecure method to allow operator containers to run in environments that used a random UID. Operator-SDK before 0.15.2 provided a script, user_setup, which modifies the permissions of the /etc/passwd file to 664 during build time. Developers who used Operator-SDK before 0.15.2 to scaffold their operator may still be impacted by this if the insecure user_setup script is still being used to build new container images. In affected images, the /etc/passwd file was created during build time with group-writable permissions and a group ownership of root (gid=0). An attacker who can execute commands within an affected container, even as a non-root user, may be able to leverage their membership in the root group to modify the /etc/passwd file. This could allow the attacker to add a new user with any arbitrary UID, including UID 0, leading to full root privileges within the container.
Severity: 5.2 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47183
Published : Aug. 7, 2025, 8:15 p.m. | 4 hours, 34 minutes ago
Description : In GStreamer through 1.26.1, the isomp4 plugin’s qtdemux_parse_tree function may read past the end of a heap buffer while parsing an MP4 file, leading to information disclosure.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47219
Published : Aug. 7, 2025, 8:15 p.m. | 4 hours, 34 minutes ago
Description : In GStreamer through 1.26.1, the isomp4 plugin’s qtdemux_parse_trak function may read past the end of a heap buffer while parsing an MP4 file, possibly leading to information disclosure.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…