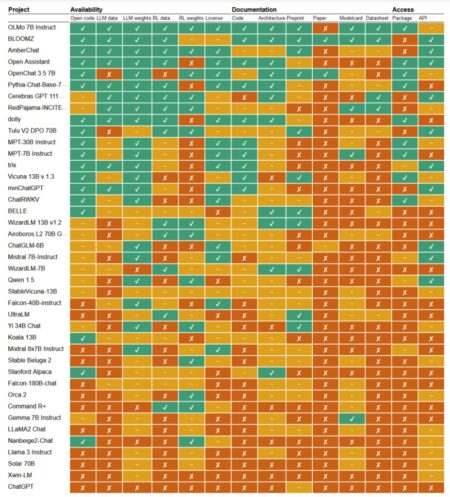
As the era of generative AI marches on, a broad range of companies have joined the fray, and the models…
Development
Are you looking for an unbiased DreamPlan review? If the answer is yes, this review is for you. To evaluate…
This quick and easy guide will show you how to know if someone has stopped sharing their location with you…
Microsoft Edge Wallet is soon getting an AI feature that lets you “autofill suggestions,” according to a new discovery on…
If you’ve encountered the Google Maps API Error: ApiNotActivatedMapError, you’re not alone. This issue typically occurs when attempting to use…
Google Chrome for Android will soon let you add custom actions in Chrome Custom Tab (CCT), according to a newly-spotted…
If you’re looking for a detailed and unbiased StoryLab AI review, my experience with the platform will surely help. StoryLab…
Microsoft has confirmed that Xbox is making its return at Gamescom 2024, but this time, its blue console rival PlayStation…
Microsoft Azure AI team has just launched Florence-2, a versatile, unified vision model, with 232M and 771M parameters variants. The…
Microsoft launched the KB5039304 update (Build 26100.994), or Windows 11 24H2, to Release Preview channel. The post KB5039304 update brings…
Microsoft confirms an annoying issue on Photos app on Windows 11 that stops you from launching it, promising a fix…
Microsoft shipped its AI theme generator for the Edge browser within the v. 126 update. The idea is nice, but…
Google Maps doesn’t support KMZ files anymore, but there’s a neat workaround I’ll share with you today. KMZ files are…
Remember the “Microsoft chat provider for Copilot in Windows†accidentally added to all editions of Windows by Microsoft Edge 123?…
Have your saved places on Google Maps suddenly disappeared? You’re certainly not alone. Luckily, I dug deep for solutions and…
Anthropic’s Claude 3.5 Sonnet, its latest, most capable model for now, has finally arrived on Amazon Bedrock. The post Claude…
Microsoft launched a new update for the Photos app on Windows 11 for Canary and Dev insiders, featuring a dynamic…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Agile is a Cliché, a widely used Phrase in today’s Industrial timeline. Evey Organisation, Group, Team wants to be Agile.…