Indonesia’s civil aviation authority has alleged suffered a massive security breach where a threat actor has claimed to have accessed…
Development
A critical security flaw has been uncovered in the Vanna.AI library, exposing SQL databases to potential remote code execution (RCE)…
Security researchers have shed more light on the cryptocurrency mining operation conducted by the 8220 Gang by exploiting known security…
The modern kill chain is eluding enterprises because they aren’t protecting the infrastructure of modern business: SaaS. SaaS continues to…
As AI democratizes product development, design will be the differentiator. But what exactly does “good†look like, and what does…
Unsurprisingly, there are lots of insights in this year’s report that impact professional researchers—but what about the many folks who…
Are you seeking insights into how precise data recovery can impact business efficiency and continuity? In data management and restoration,…
Learn how to create a custom tool for printing Riso posters using Three.js. Source: Read MoreÂ
Flowcharts are an essential tool for organizing ideas and providing clear visual representations of processes and systems. In Figma, these…
To make an application idea work, you should start with a powerful wireframe that contributes to its accessibility. Therefore, when…
Post Content Source: Read MoreÂ
Jina AI has released the Jina Reranker v2 (jina-reranker-v2-base-multilingual), an advanced transformer-based model fine-tuned for text reranking tasks. This model…
Dolphin{anty} antidetect browser stands out as a robust solution designed to help users maintain anonymity, manage multiple accounts efficiently, and…
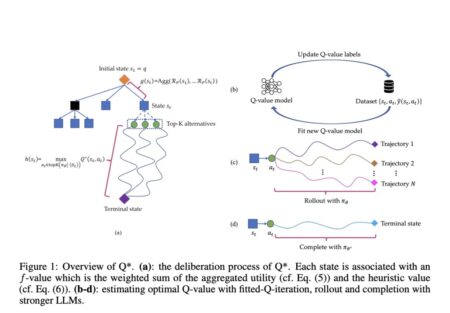
Large Language Models (LLMs) have demonstrated remarkable abilities in tackling various reasoning tasks expressed in natural language, including math word…
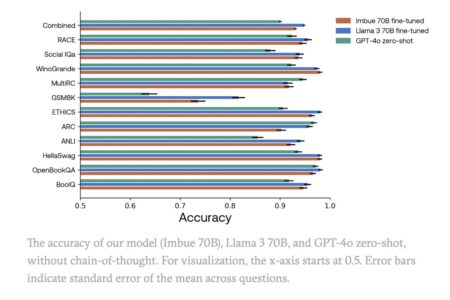
The Imbue Team recently undertook an ambitious project to train a 70-billion-parameter language model from scratch, achieving significant milestones in…
Natural Language Processing (NLP) is a critical area of artificial intelligence that focuses on the interaction between computers and human…
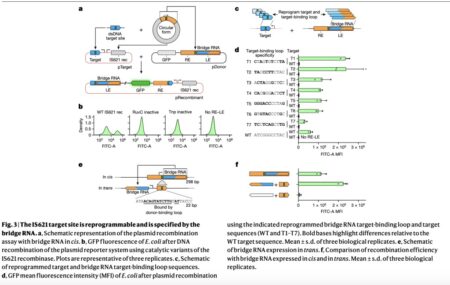
Genomic rearrangements are vital in genetic diversity, facilitated by enzymes involved in DNA repair and genetic material movement, such as…
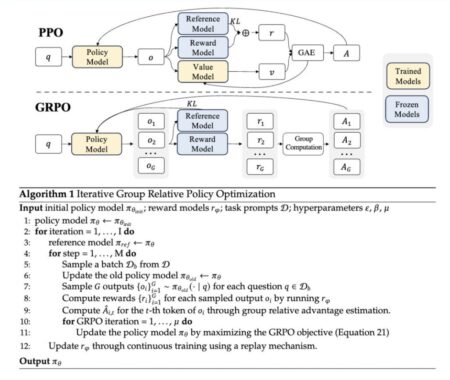
Group Relative Policy Optimization (GRPO) is a novel reinforcement learning method introduced in the DeepSeekMath paper earlier this year. GRPO…
The number of Kubernetes packages on the CNCF landscape has increased dramatically. With over 7 million developers utilizing Kubernetes, the…
The rapid evolution of artificial intelligence (AI) has given rise to a specialized branch known as AI agents. These agents…