We compare WebAssembly and JavaScript, examining their performance, portability, ease of use, security, and community support. Continue reading WebAssembly vs…
Development
Several new AI-powered photography features are expected in Google’s next generation of phones. But which Pixel models will get the…
We spend days and weeks working, sleeping, and participating in various activities while wearing a smartwatch find out which ones…
The newest Galaxy Watch is much the same outside, but comes with significant upgrades inside. Is it worth the upgrade?…
Copilot users see the difference in productivity and happiness because they don’t have to write thousands of lines for tests.…
There has been an influx of UV screen protectors on the market lately, but before you spring for a DIY…
The Shark AI Ultra Voice Control robot vacuum can empty itself to save you even more effort — and it’s…
Ahead of Amazon Prime Day, we’re already seeing tons of early deals on laptops from brands like Apple, Samsung, and…
If you’re an Android and Linux user, you’ll be glad to know there’s an easy way to integrate the two…
Digital technology is transforming the nature of therapy – and AI is its next frontier. Source: Latest newsÂ
Can you improve Google’s default security settings? You sure can! Lock down your laptop with these quick and easy tweaks.…
Our 172nd episode with a summary and discussion of last week’s big AI news! With hosts Andrey Kurenkov (https://twitter.com/andrey_kurenkov) and…
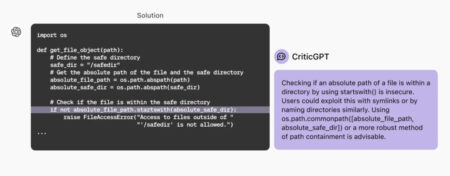
Top News OpenAI Introduces CriticGPT: A New Artificial Intelligence AI Model based on GPT-4 to Catch Errors in ChatGPT’s Code…
Google’s 2024 Environmental Report has laid bare the company’s uphill battle to achieve its ambitious goal of net-zero carbon emissions…
IT admins and users are unhappy with Windows 11’s new feature that integrates Microsoft account overview into the Start menu.…
OneDrive users have been facing a weird bug in the Shared Folders feature. This bug impacts the accessibility of the…
Navigating the complexities of cloud technology requires an exceptional partner. We are thrilled to announce that Perficient has been named…
We’ll continue building our dashboard by creating the automated chat between Dave and HAL. Source: Read MoreÂ
Managing multiple Laravel applications can be challenging, especially when it comes to modifying each app individually. For instance, if you…
We’ll finish our our game by adding the gall and determining a winner. Source: Read MoreÂ