Microsoft has confirmed that Windows 11 System Restore points will be deleted after 60 days, so you need to be more careful and periodically create restore points. This will give you multiple snapshots, but Windows will still delete the oldest ones once they exceed the retention window (now 60 days on Windows 11 24H2 by default).
Is it more or less than before? It’s hard to tell, really. Ever since Microsoft released the June 2025 update with a new 60-day policy, I’ve been testing different builds of Windows 11 on multiple PCs from varying OEMs to find out how things were before the update.
Some of my Windows 11 installations’ System Restore would expire after 10 days, but some would stay for up to 90 days.
Microsoft’s old document on “System Restore” tells us nothing about the existing retention period. Not even a word. But when digging through the older documentation, I found a document for Windows Server titled “SystemRestoreConfig class”, dated December 2020, which appears to confirm a 90-day retention period:
The time interval for which restore points are preserved, in seconds. When a restore point becomes older than this specified interval, it is deleted. The default age limit is 90 days.
Since the documentation is from 2020, it’s fair to assume that 90 days is the official System Restore point retention period for Windows 10, Server and older, but after Windows 11’s release in 2021, the retention period has been anywhere between 10 and 90 days (mostly 10 days). Now, it’s changing again for the better.
In the release notes of the June 2025 update, Microsoft confirmed that it’s locking the Restore Point to 60 days.
“After installing the June 2025 Windows security update, Windows 11, version 24H2 will retain system restore points for up to 60 days,” Microsoft announced in a support document. “This 60-day limit will also apply to future versions of Windows 11, version 24H2.”
After installing the update, Windows Latest verified the change to 60 days using the PowerShell command:
PS C:WINDOWSsystem32> $key = 'HKLM:SOFTWAREMicrosoftWindows NTCurrentVersionSystemRestore' >> (Get-ItemProperty -Path $key -Name RPLifeInterval).RPLifeInterval 5184000
As you can see, we’re getting a value of 5184000, which translates to 60 days (5184000 ÷ 86,400 seconds).
In case of Windows 10, I’m seeing 7776000 seconds, which translates to 90 days, and it’s in line with older support documents.
A 13-year-old support document (now deleted) also notes that Windows’ Restore Point was originally designed to expire after 90 days. That was the case in Windows Vista, Windows 7, and later releases. Also, when your device was running low on storage, Windows would delete all restore points in an attempt to free up disk space. This still seems to be the case.
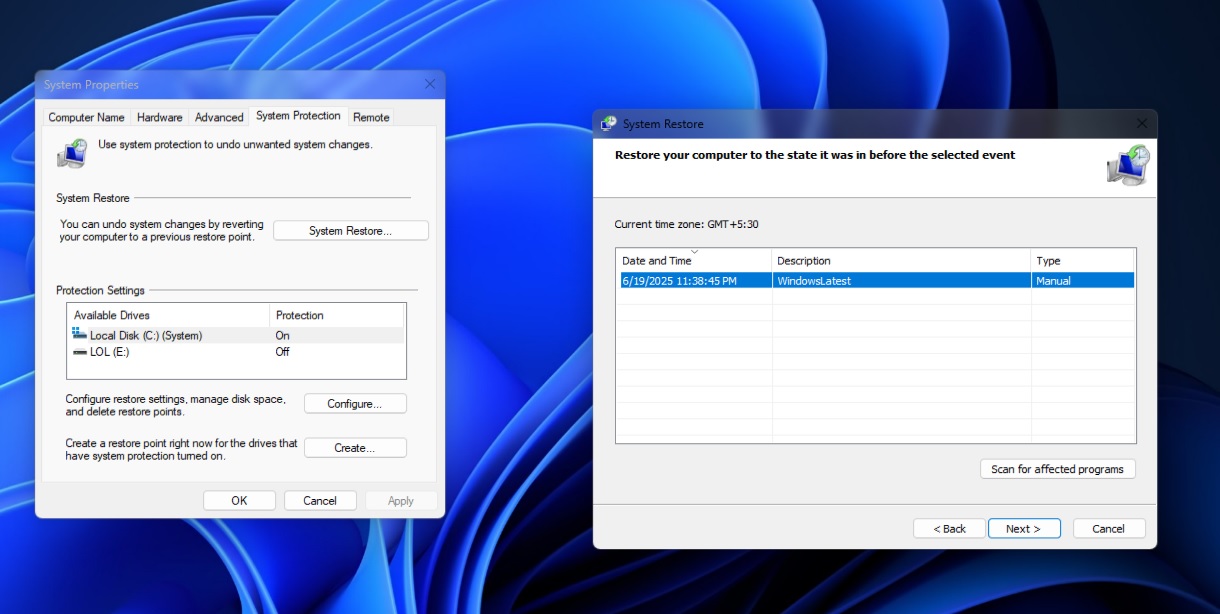
How to create a System Restore point in Windows 11
System Restore has always been the “safety net” that lets you roll Windows back after a bad driver, update or app install. To create one, follow these steps (and I recommend creating one after every few weeks):
- Open Windows Start and search for Create a restore point.
- This will open the System Protection tab in System Properties.
- Under Protection Settings, make sure one of the partitions where you intend to create the backup is “protected.”
- Select the partition and click ‘Configure’ to turn on protection.

- Once done, click Create and follow the on-screen wizard process.
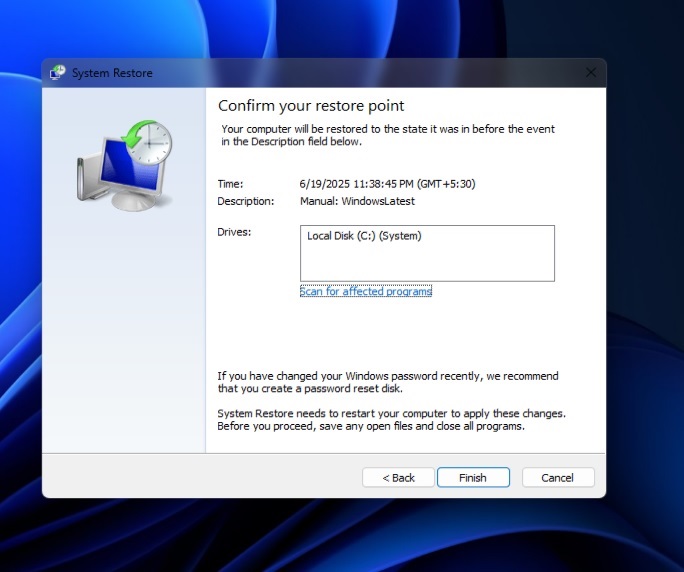
- This will create a System Restore point with an expiry of 60 days.
How often do you create a System Restore point? Let us know in the comments below.
The post Windows 11 24H2 System Restore points now expire after 60 days, Microsoft confirms appeared first on Windows Latest
Source: Read MoreÂ
