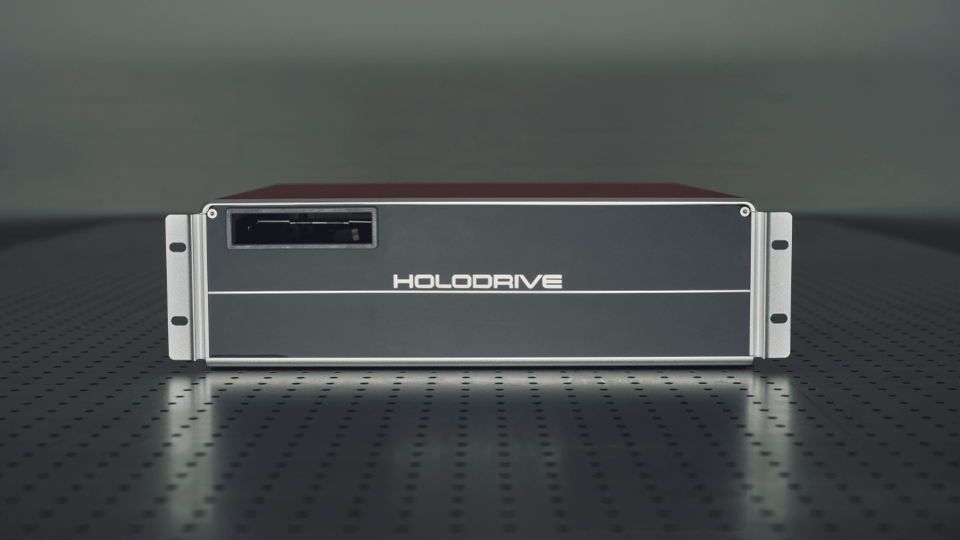
HoloMem, a cold storage data deeptech, has been awarded a £550,000 Smart Grant by Innovate UK for its HoloDrive project, in partnership with TechRe, the data centre consultants.
Global data creation is increasing exponentially, but the technological capacity to store it is not keeping pace. Magnetic tape, now a 70-year-old technology, remains the industry standard, despite being sensitive to environmental conditions and increasingly outdated.
The latest LTO version, expected this year, stores just 36TB per cartridge. It requires tightly controlled environments and suffers from data degradation over time, limiting readability.
In contrast, HoloDrive offers a next-generation solution – up to 200TB per cartridge, zero energy use for storage, no need for climate control, and infinite readability. It uses low-energy, low-cost laser diodes and recyclable HX200 photopolymer materials, delivering a high-speed, high-density storage option that reduces power consumption by 90 per cent and annual costs by around 99 per cent.
Charlie Gale, co-founder and CEO of HoloMem, said:
Current data storage technology is simply not sufficient to meet the needs of current and future global data creation; a category shift is needed. Our holographic cold data storage technology will cause huge reductions in energy usage, while allowing data to be stored at ultra-high density, with infinite readability. Our HoloDrive solution has been designed to integrate with legacy systems with minimal hardware or software disruption, and this grant from Innovate UK will help us finalise and fully validate this game-changing technology.
Source: Read MoreÂ