If you know where to look, exposed secrets are easy to find. Secrets are supposed to prevent unauthorized access, but in the wrong hands, they can be—and typically are—exploited in seconds.
To give you an idea of the scope of the problem, more than 39 million secrets were leaked across GitHub in 2024 alone.1 Every minute GitHub blocks several secrets with push protection.2 Still, secret leaks remain one of the most common—and preventable—causes of security incidents. As we develop code faster than ever previously imaginable, we’re leaking secrets faster than ever, too.
That’s why, at GitHub, we’re working to prevent breaches caused by leaked tokens, credentials, and other secrets—ensuring protection against secret exposures is built-in and accessible to every developer.
Today, we’re launching the next evolution of GitHub Advanced Security, aligning with our ongoing mission to keep your secrets…secret.
- Secret Protection and Code Security, now available as standalone products
- Advanced Security for GitHub Team organizations
- A free, organization-wide secret scan to help teams identify and reduce exposure.3
Here’s how secrets leak, what we’re doing to stop it, and what you can do to protect your code. Let’s jump in.
How do secret leaks happen?
Most software today depends on secrets—credentials, API keys, tokens—that developers handle dozens of times a day. These secrets are often accidentally exposed. Less intuitively, a large number of breaches come from well-meaning developers who purposely expose a secret. Developers also often underestimate the risk of private exposures, committing, sharing, or storing these secrets in ways that feel convenient in the moment, but which introduce risk over time.
Unfortunately, these seemingly innocuous secret exposures are small threads to pull for an attacker looking to unravel a whole system. Bad actors are extremely skilled at using a foothold provided by “low risk” secrets for lateral movement to higher-value assets. Even without the risk of insider threats, persisting any secret in git history (or elsewhere) makes us vulnerable to future mistakes. Research shows that accidental mistakes (like inadvertently making a repository public) were higher in 2024 than ever before.
If you’re interested in learning more about secret leaks and how to protect yourself, check out this great video from my colleague Chris Reddington:
What is GitHub doing about it?
We care deeply about protecting the developer community from the risk of exposed secrets. A few years ago, we formally launched our industry partnership program, which has now grown to hundreds of token issuers like AWS, Google Cloud Platform, Meta, and OpenAI—all fully committed to protecting the developer community from leaked secrets.
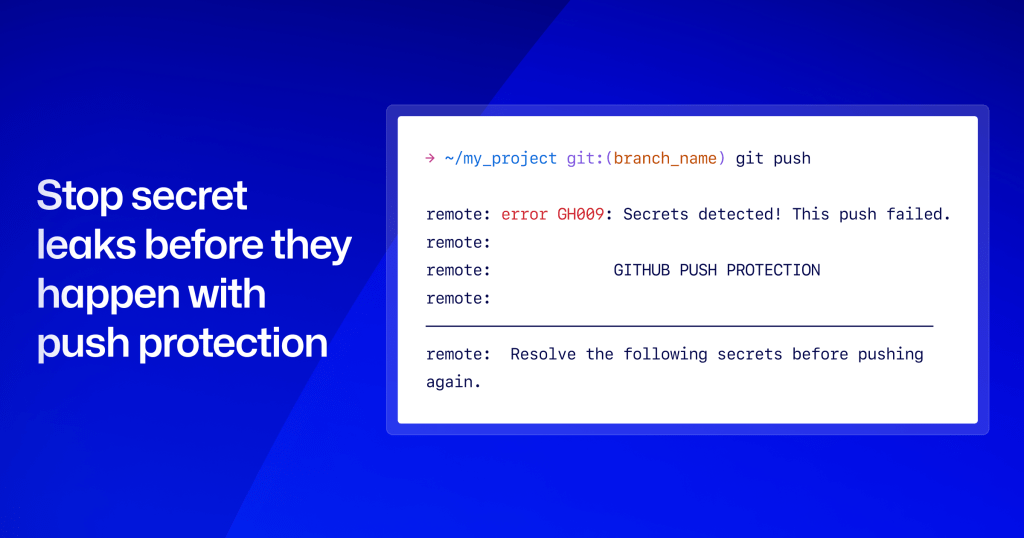
Last year, we rolled out push protection by default for public repositories, which has since blocked millions of secrets for the open source community.
And finally, as of today, we’re rolling out additional changes to our feature availability, aligning with our ongoing goal to help organizations of all sizes protect themselves from the risk of exposed secrets: a new point-in-time scan, free for organizations; a new pricing plan, to make our paid security tooling more affordable; and the release of Secret Protection and Code Security to GitHub Team plans.
What you can do to protect yourself from exposed secrets

The easiest way to protect yourself from leaked secrets is not to have any in the first place. Push protection, our built-in solution, is the simplest way to block secrets from accidental exposure. It leverages the same detectors that we created through our partnership program with cloud providers, ensuring secrets are caught quickly and accurately with the lowest rate of false positives possible.
Studies have shown that GitHub Secret Protection is the only secret scanning tool—proprietary or open source—that can claim an over one in two true positive rate across all findings4. GitHub received a precision score of 75% (compared to the next best, 46% precision). Compared to alternatives like open source scanning solutions, it’s not that GitHub is finding fewer secrets… it’s that we’re finding real ones. That way, you’re able to spend your time worrying less about false positives, and more about what matters–shipping.
Long-lived credentials are some of the most common and dangerous types of secrets to leak, as they often persist unnoticed for months–or years–and give bad actors extended access. That’s why managing secrets through their full lifecycle is critical.
Beyond push protection, you can protect yourself from leaks by following security best practices to ensure secrets are securely managed from creation to revocation:
- Creation: follow the principle of least privilege and make sure secrets are securely generated.
- Rotation: outside of user credentials, secrets should be regularly rotated.
- Revocation: restrict access when no longer needed–or when compromised.
Throughout the lifecycle of a secret, you should eliminate human interaction and automate secret management whenever possible.
In addition, you should adopt a continuous monitoring solution for detecting exposures, so you can react quickly. Like push protection, GitHub’s built-in solution for secret scanning is the simplest way to triage previously leaked secrets.
Starting today, investing in GitHub’s built-in security tooling is more affordable and in reach for many teams with the release of GitHub Secret Protection (free for public repositories), in addition to a new point-in-time scan (free for all organization repositories), which can be run periodically to check for exposed secrets.
Learn more about deploying and managing secret protection at scale:
GitHub Secret Protection and GitHub Code Security

As of today, our security products are available to purchase as standalone products for enterprises, enabling development teams to scale security quickly. Previously, investing in secret scanning and push protection required purchasing a larger suite of security tools, which made fully investing unaffordable for many organizations. This change ensures scalable security with Secret Protection and Code Security is no longer out of reach for many organizations.

In addition, as of today, our standalone security products are also available as add-ons for GitHub Team organizations. Previously, smaller development teams were unable to purchase our security features without upgrading to GitHub Enterprise. This change ensures our security products remain affordable, accessible, and easy to deploy for organizations of all sizes.
Have your secrets been exposed? Try our new public preview

Understanding whether you have existing exposed secrets is a critical step. Starting today, you can run a secret risk assessment for your organization.
The secret risk assessment is a point-in-time scan leveraging our scanning engine for organizations, covering all repositories–public, private, internal, and even archived–and can be run without purchase. The point-in-time scan provides clear insights into the exposure of your secrets across your organization, along with actionable steps to strengthen your security and protect your code. In order to lower barriers for organizations to use and benefit from the feature, no specific secrets are stored or shared.
The public preview is releasing today for organizations across GitHub Team and Enterprise plans to try. It’s still quite early, so we’d love to hear your feedback, like whether additional guidance on next steps would be helpful, or whether this is something you’d leverage outside of Team and Enterprise plans.
If you have feedback or questions, please do join the discussion in GitHub Community–we’re listening.
Learn more about GitHub Advanced Security, including Secret Protection and Code Security.
Notes
- State of the Octoverse, 2024 ↩
- Push protection helps prevent secret leaks–without compromising the developer experience–by scanning for secrets before they are pushed. Learn more about push protection. ↩
- The secret risk assessment is a free tool which will provide clear insights into secret exposure across your organization, along with actionable steps to strengthen their security and protect their code. Learn more about the secret risk assessment. ↩
- A Comparative Study of Software Secrets Reporting by Secret Detection Tools, Setu Kumar Basak et al., North Carolina State University, 2023 ↩
The post GitHub found 39M secret leaks in 2024. Here’s what we’re doing to help appeared first on The GitHub Blog.
Source: Read MoreÂ