WordPress Freelancers and agencies often do more than design and development. A full-service company may also maintain and host its clients’ websites.
Providing web hosting has several benefits for freelancers. First, it’s a vehicle to add recurring revenue to your business via reselling or an affiliate program from an established host. That steady flow of money can improve your financial health.
You’ll also have more control over each site’s environment. That helps ensure compatibility and keeps things running smoothly. Plus, you’ll know what to expect regarding performance, security, and support.
However, hosting client sites is also a serious responsibility. It puts you on the hook for technical difficulties. In addition, managing multiple WordPress websites is challenging. One false move could mean a string of crashed or hacked sites.
With that in mind, we have some tips for hosting your client’s WordPress websites. We’ll show you how to keep a watchful eye on each site without breaking your budget.
Keep Each Client Website Separate
Web hosting costs run the gamut from insanely cheap to, well, insanely expensive. It’s tempting to go the inexpensive route with a shared hosting account.
Hosts often allow multiple WordPress installs on an account. It makes sense from a business perspective. You pay for a couple of hosting packages and run all of your client sites on them.
This strategy has a couple of serious flaws. The first is that server downtime could impact every site you host. It’s bad enough when one site is down, let alone a few dozen.
Malware is the other major concern. Malicious code can easily spread from one site to another in a shared hosting environment. Once a site is compromised, it’s only a matter of time until the others are hit.
The lesson here is to keep each website on a separate hosting account. Make sure your host isolates sites via a container or other barrier. That will help prevent a security nightmare. Again, it’s easier to deal with one hacked site than having multiple infections.
And it doesn’t have to be inconvenient. Many hosts offer a centralized dashboard to access each site, and there are also third-party services that do the same.
Lock Down Your WordPress Installs
On many hosts, the famous “5-minute WordPress install” has been replaced with a one-click process. Still, older sites may have been installed manually via SFTP. Thus, it’s important to check each install to verify its integrity.
WordPress file permissions are an area of concern. For instance, allowing public access to the site’s wp-config.php file is an invitation to hackers. The file includes your database login and other sensitive information. A lot of damage can be done if it falls into the wrong hands.
The WordPress developer documentation has a handy guide for setting the correct file permissions. Follow its advice and ensure files only have the required permissions.
You might also want to disable file editing within the WordPress dashboard. That will prevent a malicious actor (or adventurous client) from editing theme or plugin files.
Add the following line to each site’s wp-config.php file: define( 'DISALLOW_FILE_EDIT', true );
Other ways to secure the sites you host:
- Install a WordPress security plugin.
- Add an activity logging plugin to keep track of changes and user actions.
- Employ a content delivery network (CDN) with a firewall to block suspicious traffic.
- Limit access to the
/wp-admin/folder.
The goal is to enhance each site’s security, which provides peace of mind for you and your clients.

Ensure You Have Enough Server Resources
Every website you host will have different needs. For example, a brochure site’s functionality isn’t as complex as a WooCommerce shop. Plus, some will inevitably receive more traffic.
That’s why hosting is not a one-size-fits-all proposition. Hosts offer tiered services that account for storage and bandwidth. They may also limit the number of domains, dashboard users, or site visitors. Crossing these thresholds can be costly.
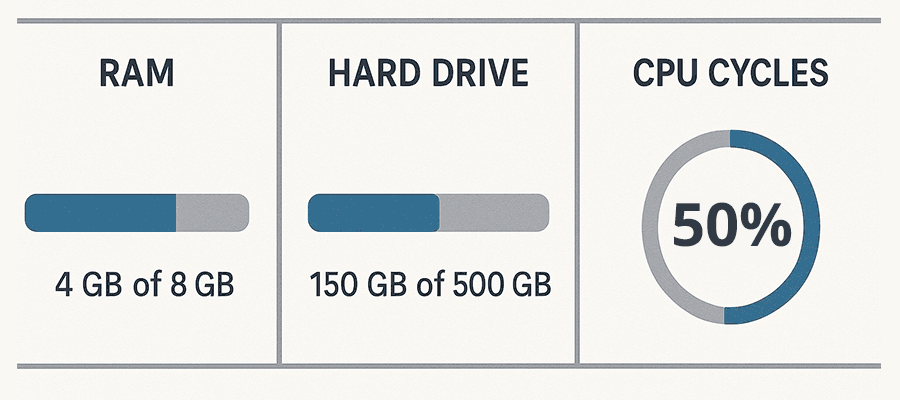
Also, pay attention to server resources like memory, CPU cycles, and PHP workers. Shared hosting environments don’t usually guarantee a minimum. More expensive accounts, such as VPS and dedicated servers, assign these resources to your account.
It pays to understand what your host offers and how it impacts your websites. A site with too few resources won’t perform well and may break. Meanwhile, hosting a small site on a higher tier could be wasteful.
You can avoid problems by assessing each site you host. Pay particular attention to the following factors:
- Monthly traffic (via Google Analytics or other apps);
- Security risks (online transactions, user accounts);
- The amount of content;
- Special functionality (shopping carts, members-only areas, resource-intensive plugins);
Site stability, performance, and security are vital to success. Using the right hosting will go a long way toward ensuring it.
Keep an Eye Out for Hosting Changes
We know that WordPress, themes, and plugins all require regular maintenance. That’s something we often manage for our clients. But hosts also maintain their infrastructure.
A host will apply new software versions and security patches to their servers. They’ll also upgrade hardware from time to time. You’ll want to know when this happens.
PHP upgrades are a prime example. An outdated theme or plugin could be incompatible with the latest version, which leads to a buggy or broken site.
Staying in the know can help prevent these types of issues. Web hosts often announce maintenance plans ahead of time. They may publish to a blog, add a dashboard alert, or send an email.
Make an effort to inform yourself of what’s happening. It can save you from a future headache or two.

Be a Good Host
Hosting your client’s WordPress websites keeps you in the loop. You’ll be able to watch over each site and ensure its health. It’s also a path to making some extra money.
When things run smoothly, the burden on your time should be minimal. Ensuring things stay that way is part of the job, though.
The first step is to choose your hosting provider wisely. Look for a host that follows best security practices and has a deep understanding of WordPress. They should also offer enough resources to run each site without issue.
From there, it’s all about being proactive with the sites in your portfolio. Keep them updated and take extra security measures. In other words: control the things you can.
Some things are beyond our control. We can’t predict downtime or a host being sold. However, we can put ourselves and our clients in a position to succeed. We hope the tips above will help you get there.
The post Tips for Hosting Your Client’s WordPress Website appeared first on Speckyboy Design Magazine.
Source: Read More