New Phishing Tactic: Attackers Abuse Blob URIs to Bypass Email Security
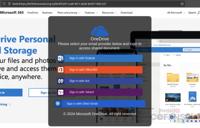
A blob URI page spoofing a OneDrive login | Image: Cofense
Cofense Intelligence has detected a new technique used by threat actors to successfully deliver credential phishing pages to users’ inboxes: …
Read more
Published Date:
May 09, 2025 (4 hours, 8 minutes ago)
Vulnerabilities has been mentioned in this article.
Source: Read More
