In today’s data driven landscape, Organizations are not just collecting the Data, they are striving to understand, trust and maximize its value. One of the critical capabilities that helps achieve the goal is data enrichment-especially when implemented through enterprise grade governance tools like Collibra.
In this blog, we will explore how Collibra enables data enrichment, why it is essential for effective data governance and how organizations can leverage it to drive better decision-making.
What is data enrichment in Collibra?
Data enrichment enhances the dataset within Collibra data governance tool by adding business context, metadata correcting inaccuracies and governance attributes that help users to understand the data’s meaning, usage, quality and lineage.
Rather than simply documenting tables/columns, data enrichment enables organizations to transform technical metadata into meaningful, actionable insights in which this enriched context empowers business and technical users alike to trust the data they are working with and use it confidently for analysis, reporting and compliance.
How does Data Enrichment work in Collibra?
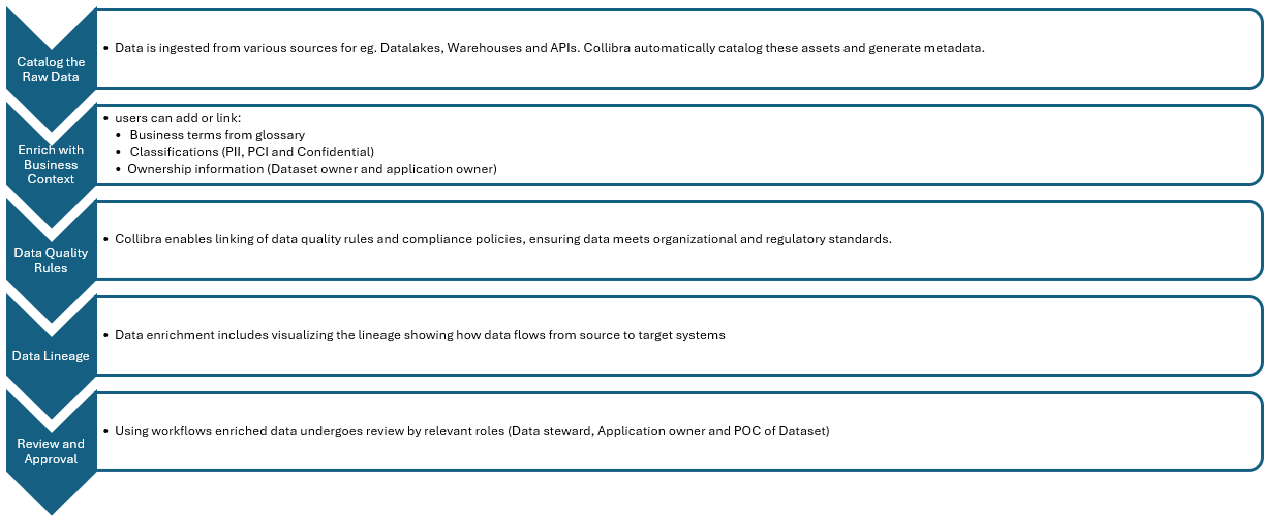
How we use Data Enrichment in the Banking Domain:
In today’s digital landscape, banks manage various data formats (such as CSV, JSON, XML, and tables) with vast volumes of data originating from internal and external sources like file systems, cloud platforms, and databases. Collibra automatically catalogs these data assets and generates metadata.
But simply cataloging data isn’t enough. The next step is data enrichment, where we link technical metadata with business-glossary terms to give metadata meaningful business context and ensure consistent description and understanding across the organization. Business terms clarify what each data element represents from a business perspective, making it accessible not just to IT teams but also to business users.
In addition, each data asset is tagged with data classification labels such as PCI (Payment Card Information), PII (Personally Identifiable Information), and confidential. This classification plays a critical role in data security, compliance, and risk management, especially in a regulated industry like banking.
To further enhance the trustworthiness of data, Collibra integrates data profiling capabilities. This process analyzes the actual content of datasets to assess their structure and quality. Based on profiling results, we link data to data‑quality rules that monitor completeness, accuracy, and conformity. These rules help enforce high-quality standards and ensure that the data aligns with both internal expectations and external regulatory requirements.
An important feature in Collibra is data lineage, which provides a visual representation of the data flow—from its source to its destination. This visibility helps stakeholders understand how data transforms and moves through various systems, which is essential for impact analysis, audits, and regulatory reporting.
Finally, the enriched metadata undergoes a structured workflow-driven review process. This involves all relevant stakeholders, including data owners, application owners, and technical managers. The workflow ensures that we not only produce accurate and complete metadata but also review and approve it before publishing or using it for decision-making.
For ex : Enriching the customer data table
Database : Vertica Datalake
Table : Customer_Details
Column : Customer_MailID
Business Term : Customer Mail Identification
Classification :PII (Personally Identifiable Information)
Quality rule : There is no null values in Customer mailID. (Completeness)
Linked Polity :GDPR policy for EU Region
Lineage : Salesforce à ETL pipeline à Vertica
Data enrichment in Collibra is a cornerstone of a mature Data Governance Framework, it helps transform raw technical metadata into a living knowledge asset-fueling trust, compliance and business value. By investing time in enriching your data assets, you are not just cataloging them, you are empowering your organization to make smarter, faster and more compliant data driven decisions.
Source: Read MoreÂ