Objective
If you are looking for a solution to securely store your secrets like DB credentials, API keys, tokens, passwords, etc., AWS Secret Manager is the service that comes to your rescue. Keeping the secrets as plain text in your code is highly risky. Hence, storing the secrets in AWS secret manager helps you with the following.
AWS Secret Manager is a fully managed service that can store and manage sensitive information. It simplifies secret handling by enabling the auto-rotation of secrets to reduce the risk of compromise, monitoring the secrets for compliance, and reducing the manual effort of updating the credentials in the application after rotation.
Essential Features of AWS Secret Manager
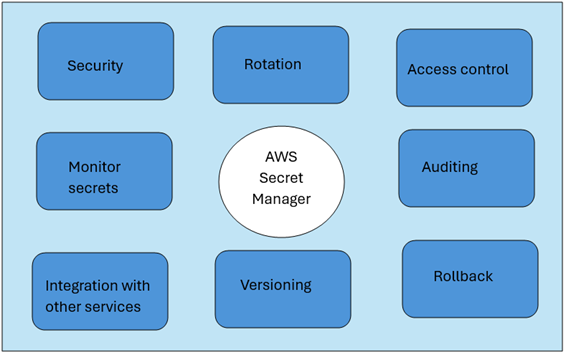
- Security: Secrets are encrypted using encryption keys we can manage through AWS KMS.
- Rotation schedule: Enable rotation of credentials through scheduling to replace long-term with short-term ones.
- Authentication and Access control: Using AWS IAM, we can control access to the secrets, control lambda rotation functions, and permissions to replicate the secrets.
- Monitor secrets for compliance: AWS Config rules can be used to check whether secrets align with internal security and compliance standards, such as HIPAA, PCI, ISO, AICPA SOC, FedRAMP, DoD, IRAP, and OSPAR.
- Audit and monitoring: We can use other AWS services, such as Cloud Trail for auditing and Cloud Watch for monitoring.
- Rollback through versioning: If needed, the secret can be reverted to the previous version by moving the labels attached to that secret.
- Pay as you go: Charged based on the number of secrets managed through the Secret manager.
- Integration with other AWS services: Integrating with other AWS services, such as EC2, Lambda, RDS, etc., eliminates the need to hard code secrets.
AWS Secret Manager Pricing
At the time of publishing this document, AWS Secret Manager pricing is below. This might be revised in the future.
| Component | Cost | Details |
|---|---|---|
| Secret storage | $0.40 per secret per month | Charges are done per month. If they are stored for less than a month, the cost is prorated. |
| API calls | $0.05 per 10,000 API calls | Charges are charged to API interactions like managing secrets / retrieving secrets. |
Creating a Secret
Let us get deeper into the process of creating secrets.
- Log in to the AWS Secret management console and select the “store a new secret” option: https://console.aws.amazon.com/secretsmanager/.
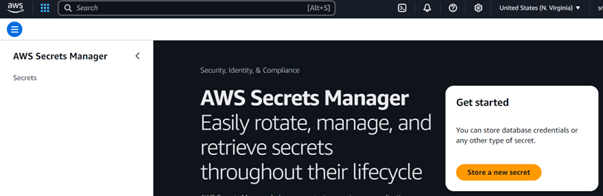
- On the Choose secret type page,
- For Secret type, select the type of database secret that you want to store:
- For Credentials, input the credentials for the database that has been hardcoded. 
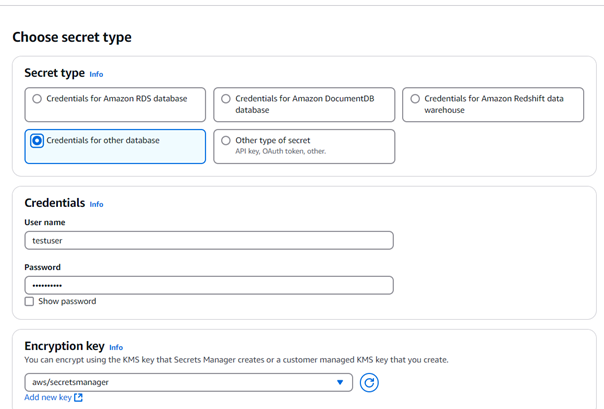
- For the Encryption key, choose AWS/Secrets Manager. This encryption key service is free to use.
- For the Database field, choose your database.
- Then click Next.
- On the Configure secret page,
- Provide a descriptive secret name and description.
- In the Resource permissions field, choose Edit permissions. Provide the policy that allows RoleToRetrieveSecretAtRuntime and Save.
- Then, click Next.
- On the Configure rotation page,
- select the schedule for which you want this to be rotated.
- Click Next.
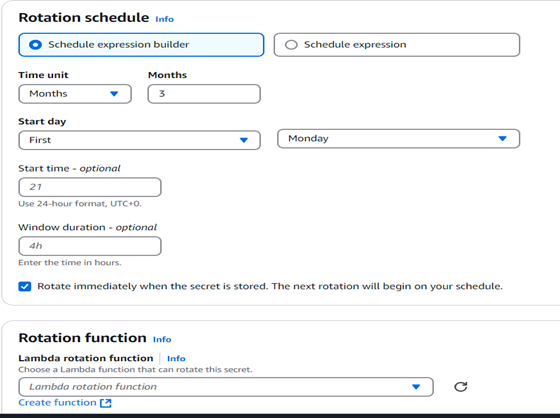
- On the Review page, review the details, and then Store.
Output
The secret is created as below.
We can update the code to fetch the secret from Secrets Manager. For this, we need to remove the hardcoded credentials from the code. Based on the code language, there is a need to add a call to the function or method to the code to call the secret manager for the secret stored here. Depending on our requirements, we can modify the rotation strategy, versioning, monitoring, etc.
Secret Rotation Strategy
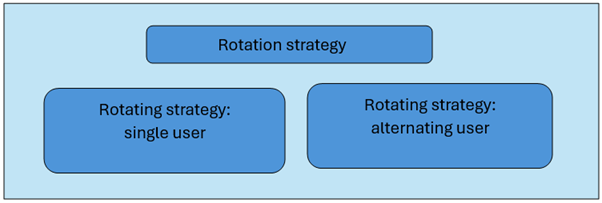
- Single user – It updates credentials for one user in one secret. During secret rotation, open connections will not be dropped. While rotating, Open connections might experience a low risk of database denial calls that use the newly rotated secrets. This can be mitigated through retry strategies. Once the rotation is completed, all new calls will use the rotated credentials.
- Use case – This strategy can be used for one-time or interactive users.
- Alternating users – This method updates secret values for two users in one secret. We create the first use. Then, we create a cloned second user using the rotation function during the first rotation. Whenever the secret rotates, the rotation function alternates between the user’s password and the one it updates. Even during rotation, the application gets a valid set of credentials.
- Uses case – This is good for systems that require high availability.
Versioning of Secrets
A secret consists of the secret value and the metadata. To store multiple values in one secret, we can use json with key-value pairs. A secret has a version that holds copies of the encrypted secret values. AWS uses three labels, like:
- AWSCURRENT – to store current secret value.
- AWSPREVIOUS – to hold the previous version.
- AWSPENDING – to hold pending value during rotation.
Custom labeling of the versions is also possible. AWS can never remove labeled versions of secrets, but unlabeled versions are considered deprecated and will be removed at any time.
Monitoring Secrets in AWS Secret Manager
Secrets stored in AWS Secret Manager can be monitored by services provided by AWS as below.
- Using cloud trail – This stores all API calls to the secret Manager as events, including secret rotation and version deletion.
- Monitoring using Cloudwatch – the number of secrets in our account can be managed, secrets that are marked for deletion, monitor metrics, etc. We can also set an alarm for metric changes.
Conclusion
AWS Secrets Manager offers a secure, automated, scalable solution for managing sensitive data and credentials. It reduces the risk of secret exposure and helps improve application security with minimal manual intervention. Adopting best practices around secret management can ensure compliance and minimize vulnerabilities in your applications.
Source: Read MoreÂ


