In today’s cloud-centric world, AWS (Amazon Web Services) stands out as a leading provider of scalable and reliable cloud services. Python’s Boto3 library is a powerful tool that allows developers to interact with AWS services programmatically. However, ensuring secure interactions is crucial to protect sensitive data and maintain the integrity of your applications.
Main objective of this blog is to explain how we can interact with different AWS services in a secure way. In this blog, I explained how we can create a session object from AWS credentials (keys and secret keys) which we are fetching from OS environment variables and use session object to interact with AWS services.
Setting Up Python, Boto3 API, AWS and VS Code Editor
Python
You could ensure if Python installed in your system/server by running “python –version” command. We can run same command in any operating system either that is Windows, Linux/Unix or MacOS. if python not installed, then we need to install it first before moving forward.
You can download and install the python from its official page Download Python | Python.org
VS Code
I am using VS Code editor tool for developing the boto3 Api code, so we also need to ensure few things in code editor.
-
We need to install Python extension for Visual Studio Code which integrate and offer support for IntelliSense (Pylance), debugging (Python Debugger), formatting, linting, code navigation, refactoring, variable explorer, test explorer, and many more.
- We also need to ensure if python version showing on right bottom bar when writing in python file. this will be available once we setup the python properly in our system.
Boto3
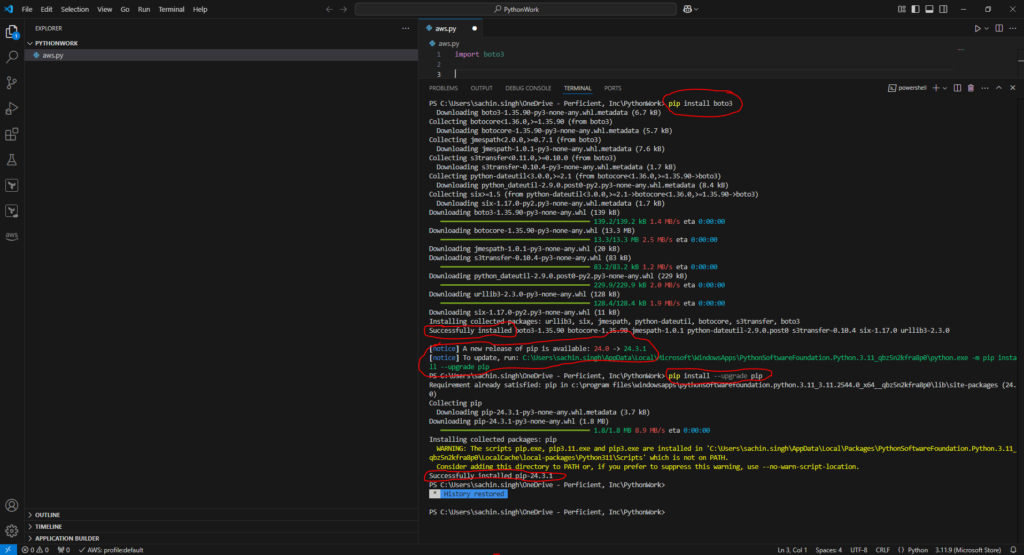
Once python and VS Code setup done then we need to install the python boto3 package from command “pip install boto3”.
- boto3 package will not be recognize and give error during execution until we install it. see in given screenshot where you can see yellow underline under boto3.
- To run this command in VS Code editor, we can open terminal from Terminal >> New Terminal and run this command there. you can see the installation in below screenshot where few other dependent packages also installed along with boto3 package. later it was also asking me to upgrade pip (python package manager), so I run that command as well.
- Now we are ready with boto3 api
AWS
Configure your AWS credentials using the AWS CLI or by setting environment variables.
- if we need to use aws cli then we need it install it first.
- You can use download and installation instructions from here
- once aws cli installed then we can use “aws configure” command to set the credentials
- more details, you can find here Configuring settings for the AWS CLI – AWS Command Line Interface
Securely Managing AWS Credentials
Managing AWS credentials securely is the first step in ensuring secure interactions with AWS services. There is two way we can use to interact with different AWS services.
- Environment Variables: Store your AWS credentials in environment variables instead of hardcoding them in your scripts.
import os
import boto3
aws_access_key = os.getenv('AWS_ACCESS_KEY_ID')
aws_secret_key = os.getenv('AWS_SECRET_ACCESS_KEY')
session = boto3.Session(
aws_access_key_id=aws_access_key,
aws_secret_access_key=aws_secret_key
)
- IAM Roles: Use IAM roles for EC2 instances to avoid storing credentials on the instance.
session = boto3.Session()
s3 = session.resource('s3')
Different AWS Services Interaction with boto3 API
Let’s explore how to interact with some common AWS services securely.
Amazon S3
Amazon S3 is a widely used storage service. Here’s how to securely interact with S3 using Boto3.
- Uploading Files
import os
import boto3
aws_access_key = os.getenv('aws_access_key_id')
aws_secret_key = os.getenv('aws_secret_access_key')
session = boto3.Session( aws_access_key_id=aws_access_key, aws_secret_access_key=aws_secret_key )
s3 = session.resource('s3')
bucket_name = 'sachinsinghfirstbucket'
file_path = 'temp/first.txt'
s3.Bucket(bucket_name).upload_file(file_path, 'first.txt')
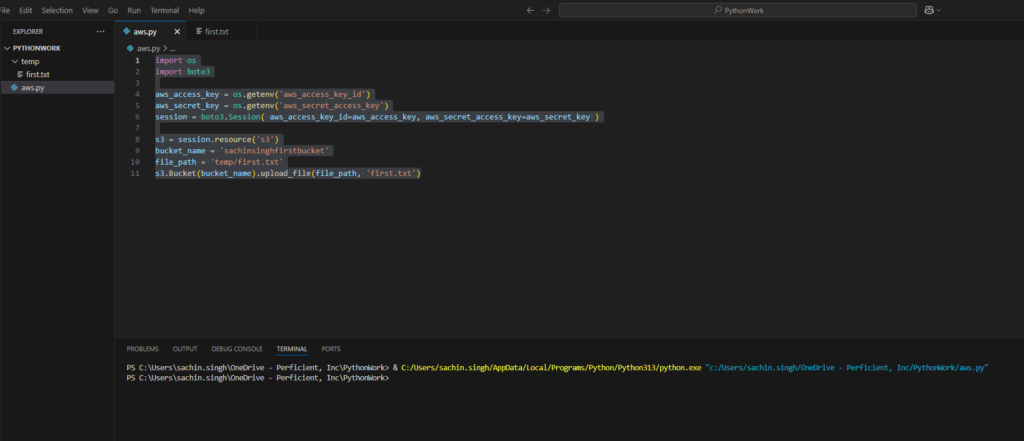
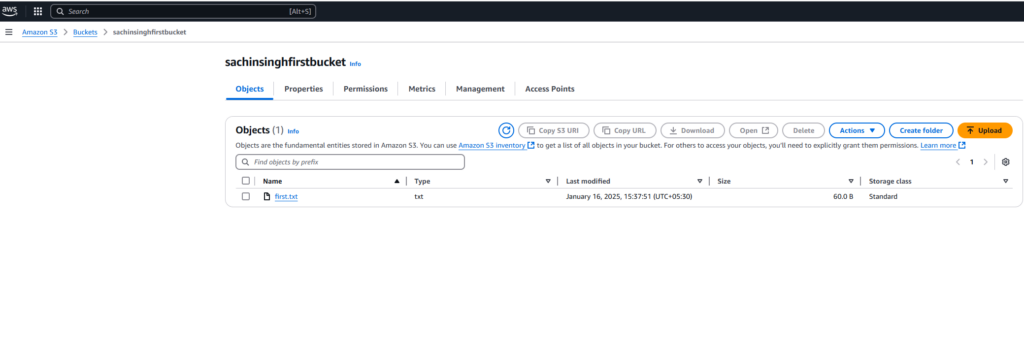
- Downloading Files
import os
import boto3
aws_access_key = os.getenv('aws_access_key_id')
aws_secret_key = os.getenv('aws_secret_access_key')
session = boto3.Session( aws_access_key_id=aws_access_key, aws_secret_access_key=aws_secret_key )
s3 = session.resource('s3')
bucket_name = 'sachinsinghfirstbucket'
file_path = 'temp/first_copy.txt'
s3.Bucket(bucket_name).download_file('first.txt', file_path)
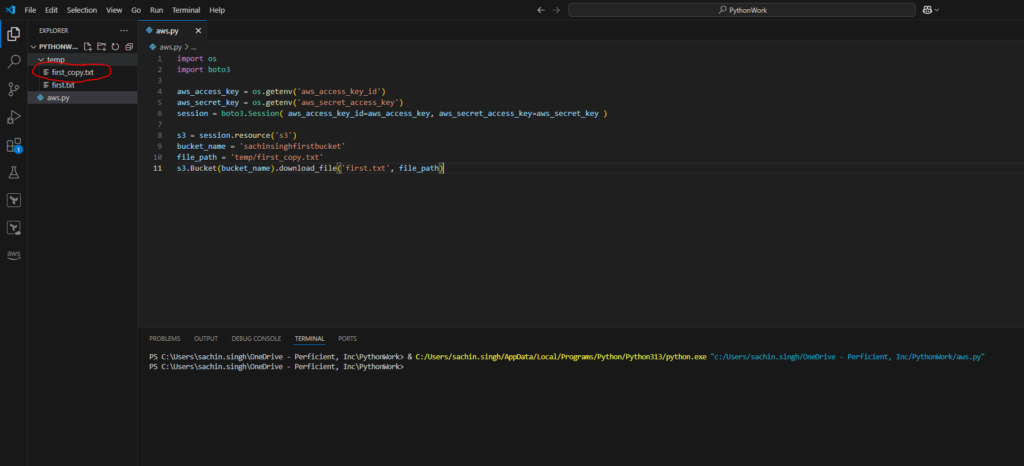
Amazon EC2
Amazon EC2 provides scalable computing capacity. Here’s how to manage EC2 instances securely.
- Launching an Instance
import os
import boto3
aws_access_key = os.getenv('aws_access_key_id')
aws_secret_key = os.getenv('aws_secret_access_key')
session = boto3.Session( aws_access_key_id=aws_access_key, aws_secret_access_key=aws_secret_key )
ec2 = session.resource('ec2')
instance = ec2.create_instances(
ImageId='ami-07b69f62c1d38b012',
MinCount=1,
MaxCount=1,
InstanceType='t2.micro'
)
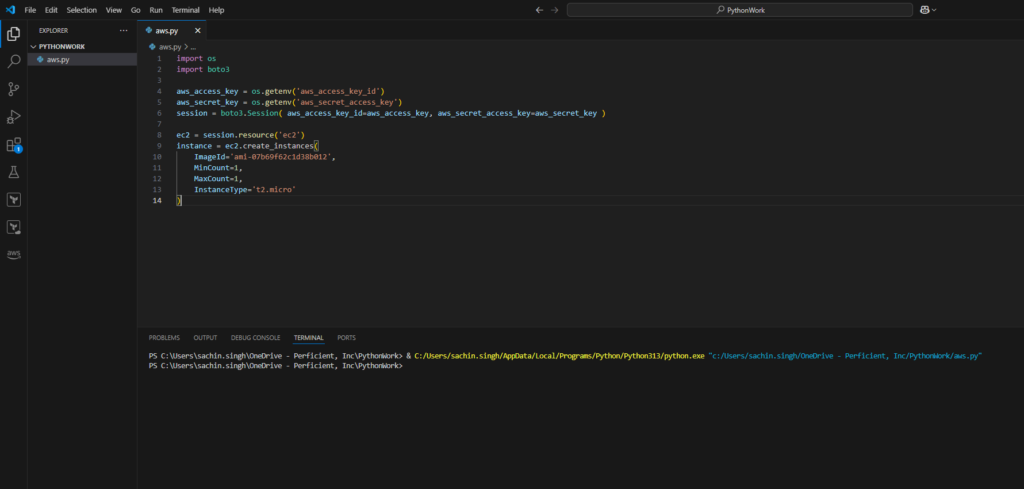
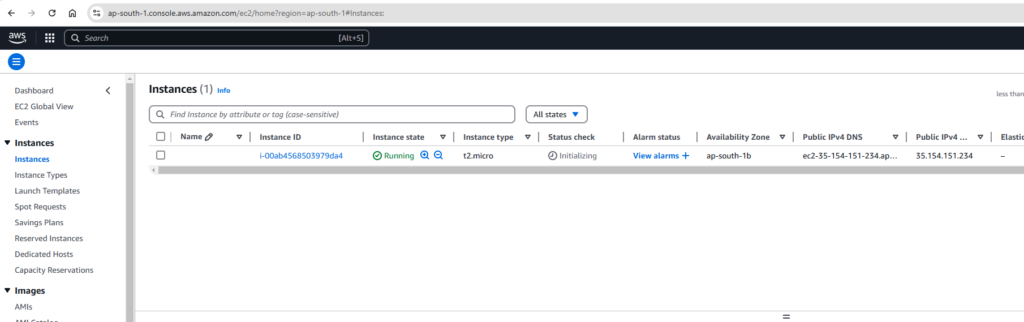
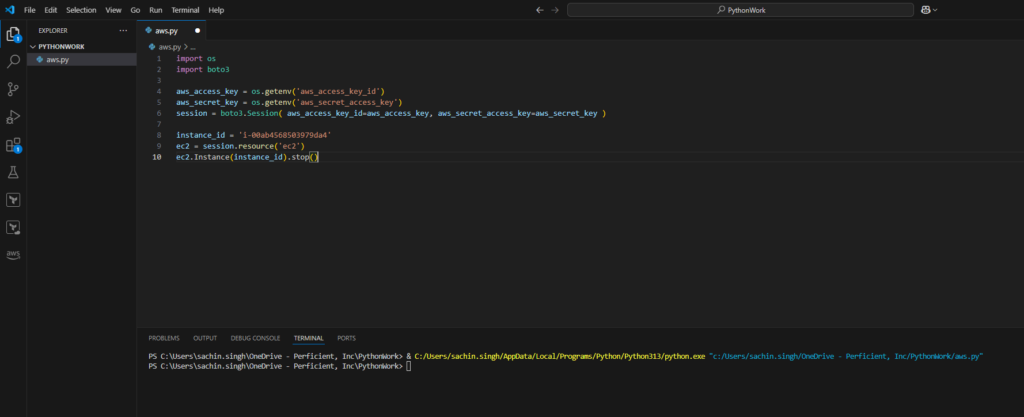
- Stopping an Instance
import os
import boto3
aws_access_key = os.getenv('aws_access_key_id')
aws_secret_key = os.getenv('aws_secret_access_key')
session = boto3.Session( aws_access_key_id=aws_access_key, aws_secret_access_key=aws_secret_key )
instance_id = 'i-00ab4568503979da4'
ec2 = session.resource('ec2')
ec2.Instance(instance_id).stop()
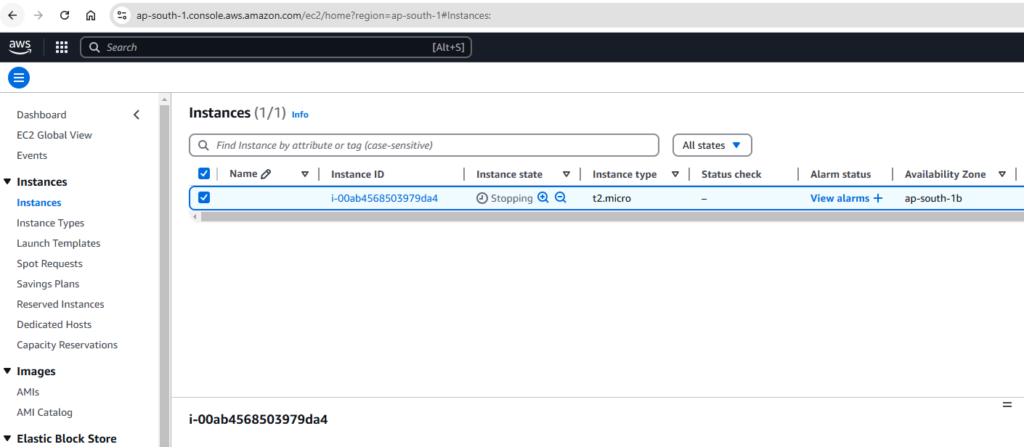
For Other Services
You can go through other services and detailed documentation here Boto3 1.35.91 documentation
Best Practices for Secure Boto3 Interactions
-
Use Least Privilege: Ensure that your IAM policies grant the minimum permissions required for your tasks.
-
Rotate Credentials Regularly: Regularly rotate your AWS credentials to reduce the risk of compromise.
-
Enable Logging and Monitoring: Use AWS CloudTrail and CloudWatch to monitor and log API calls for auditing and troubleshooting.
Interacting with AWS services using Boto3 is powerful and flexible, but security should always be a top priority. By following best practices and leveraging AWS’s security features, you can ensure that your applications remain secure and resilient.
Source: Read MoreÂ


