Biometric authentication has emerged as a promising solution to enhance security by offering a more robust defense against cyber threats. However, hackers can increasingly develop sophisticated methods to bypass traditional security measures as technology advances. This includes forging common protections such as easily guessed PINs, passwords, or even misplacing physical keys, which were once considered reliable safeguards.
Despite being widely employed, traditional security techniques like passwords, PINs, and keys have built-in drawbacks, such as vulnerability to hacking, loss, or theft. This highlights the need for more user-friendly, safe authentication methods that adjust to changing cybersecurity threats.
Although biometric systems have become more popular as substitutes, conventional unimodal systems are susceptible to spoofing. To increase security, multimodal biometric systems integrate characteristics like iris and ECG or ear and iris, making duplication more challenging. These devices are useful in combinations like palm and finger veins, increase accuracy, reduce spoofing, and are resistant to noise.
Multimodal biometric systems provide benefits but can have drawbacks, such as more complexity, higher processing demands, and possible privacy issues. The development of authentication systems continues to face the difficulty of finding a balance between security, usability, and privacy as cybersecurity threats evolve.
To address the abovementioned issues, new research published in BioMed Research International describes a novel methodology combining feature-level and decision-level fusion to improve detection accuracy. The method consists of several key stages: preprocessing to improve data quality, segmentation and feature extraction for ECG and iris signals, a feature fusion module to combine and refine features, and decision-level fusion with a score-level model to assess the similarity between ECG and iris inputs.
The suggested methodology presents a multimodal authentication technique that enhances accuracy by utilizing iris and ECG data. The procedure uses feature extraction, fusion, and classification models to identify and categorize patterns. The extraction and analysis of biometric features are the main objectives of the separate phases that comprise the authentication process.
- Iris Feature Extraction: Data is captured under controlled lighting conditions to ensure accuracy. The iris is segmented by approximating its center and identifying inner and outer boundaries. Circular edge detection via convolution helps find these boundaries, allowing for cropping and segmentation. A combination of Gabor filtering and Scale-Invariant Feature Transform (SIFT) is applied for robust feature extraction, providing scale- and rotation-invariant descriptors.
- ECG Feature Extraction: Wavelet transform extracts features from ECG signals, followed by Principal Component Analysis (PCA) for dimensionality reduction. Peak detection identifies key features such as R, S, and T waves. The Symlet 8 wavelet function is applied due to its symmetry, with a 2-level decomposition process to analyze the ECG signal’s high- and low-frequency components.
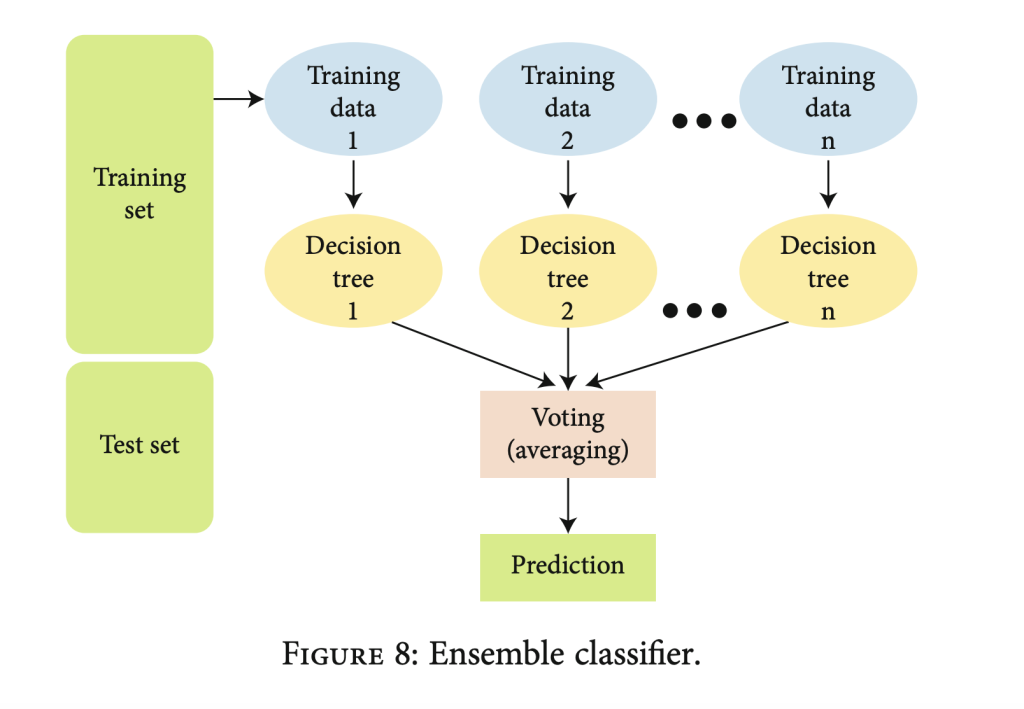
- Ensemble Classifier: The final stage involves an ensemble classifier, where decision trees are trained using the extracted multimodal features. Predictions from individual trees are combined through majority voting to make the final classification decision. This process enhances the system’s robustness and learning patterns from ECG and iris data for accurate authentication.
To evaluate this method, the research team conducted experiments using biometric data from 45 users, split into 70% for training and 30% for validation. The experiments assessed individual and combined biometric modalities, focusing on ECG and iris data.
Results showed that the proposed ensemble classifier outperformed standard methods, achieving superior accuracy (95.65%), sensitivity (96.2%), and precision (96.55%) for multimodal scenarios. The comparative analysis highlighted its effectiveness over random forest, decision tree, and bagged ensemble classifiers, with the combined multimodal approach yielding the highest performance.
In conclusion, the proposed multimodal biometric authentication system demonstrates a significant advancement in cybersecurity by addressing the vulnerabilities of traditional unimodal and password-based security methods. By integrating ECG and iris data with innovative feature-level and decision-level fusion techniques, the system achieves enhanced accuracy, robustness, and resistance to spoofing. The experiments highlight the superiority of the ensemble classifier, which consistently outperforms traditional methods, providing reliable authentication while maintaining usability.
Check out the Paper. All credit for this research goes to the researchers of this project. Also, don’t forget to follow us on Twitter and join our Telegram Channel and LinkedIn Group. Don’t Forget to join our 65k+ ML SubReddit.
 Recommend Open-Source Platform: Parlant is a framework that transforms how AI agents make decisions in customer-facing scenarios. (Promoted)
Recommend Open-Source Platform: Parlant is a framework that transforms how AI agents make decisions in customer-facing scenarios. (Promoted)
The post Beyond Passwords: A Multimodal Approach to Biometric Authentication Using ECG and Iris Data appeared first on MarkTechPost.
Source: Read MoreÂ