- The Need for Integrated Security in DevOps
- Role of Tx-DevSecOps
- Key Features of Tx-DevSecOps
- Benefits of Implementing Tx-DevSecOps
- Summary
Protecting sensitive data against cyber threats is one crucial step in the software application industry. The rising number of cybercrimes and security threats has dramatically changed how businesses operate and innovate. Traditional DevOps practices can no longer keep up with high-velocity, continuous delivery software development. One of the reasons is that a separate cybersecurity and QA team handles the security aspect in the DevOps ecosystem at the end of the SDLC. DevSecOps seeks to cover this gap by integrating security controls throughout the SDLC. Tx-DevSecOps is an accelerator that assists QA teams in utilizing its high-speed, shift-left approach for continuous security across development and testing.
The Need for Integrated Security in DevOps
The process of integrating security into DevOps is called DevSecOps. Due to the increasing sophistication and frequency of security threats, it has become crucial for modern development processes. Enterprises embed security practices throughout their DevOps pipeline to identify and address vulnerabilities as soon as they appear to reduce risk and improve security posture. This enables organizations to deliver software quickly and on a scale without degrading their IT security posture. Here’s why integrating security with DevOps is essential:
• DevSecOps facilitates early identification of vulnerabilities and provides quicker and cost-effective remediation measures.
• With proactive vulnerability mitigation, enterprises can reduce the risk of data breaches and reputational damage.
• By integrating security in the development pipeline early, organizations reduce the cost of fixing issues post-deployment.
• Automated security tools and practices enable faster software releases without degrading security.
Role of Tx-DevSecOps
Tx-DevSecOps is an advanced security automation accelerator and an extension of Tx-DevOps, a DevOps framework by Txs’ DevOps Center of Excellence (DCoE). Although Tx-DevOps helps teams improve the time-to-market ratio by streamlining development and operations through DevOps Consulting, IaC, CI/CD implementation, and test automation, it still requires transformative processes, organizational culture, and technology shifts.
Tx-DevSecOps addresses the growing demand for secure development practices by seamlessly integrating security into every stage of the SDLC. By leveraging the shift-left approach and latest automation tools, Tx-DevSecOps supports early vulnerability detection, robust application security, and continuous compliance.
Key Features of Tx-DevSecOps
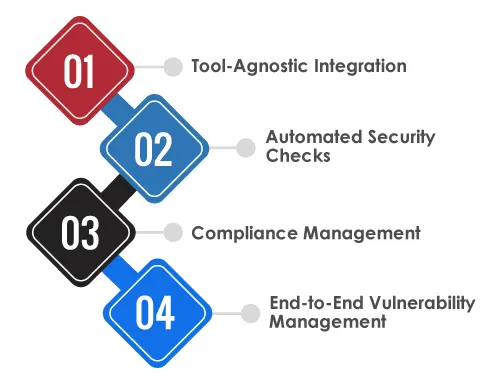
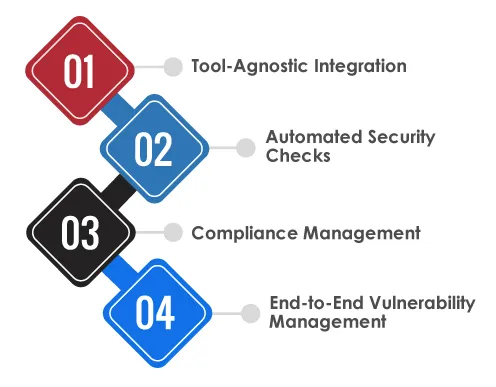
Tool-Agnostic Integration:
Tx-DevSecOps is designed to integrate seamlessly with any continuous integration (CI) pipeline. It enables enterprises to embed security into their development workflows without disrupting deployment processes. Its flexible, tool-agnostic approach ensures compatibility across diverse technology stacks.
Automated Security Checks:
Security is automated throughout the DevOps lifecycle using Software Composition Analysis (SCA), Static Application Security Testing (SAST), and Dynamic Application Security Testing (DAST). These automated validations help identify vulnerabilities in code, dependencies, and runtime behavior, ensuring secure application development from start to finish.
Compliance Management:
Tx-DevSecOps enables organizations to meet international regulatory standards through built-in Compliance as Code (CaC) and Infrastructure as Code (IaC) policies. It supports frameworks such as GDPR, PCI-DSS, OWASP, and SOC 2, enabling continuous compliance and reducing the risk of audit failures or penalties.
End-to-End Vulnerability Management:
With full lifecycle visibility, Tx-DevSecOps facilitates proactive identification, tracking, and remediation of vulnerabilities. It uses the Common Vulnerability Scoring System (CVSS) to prioritize risks effectively and eliminate duplicates, streamlining the remediation process and helping teams focus on priority tasks.
Benefits of Implementing Tx-DevSecOps
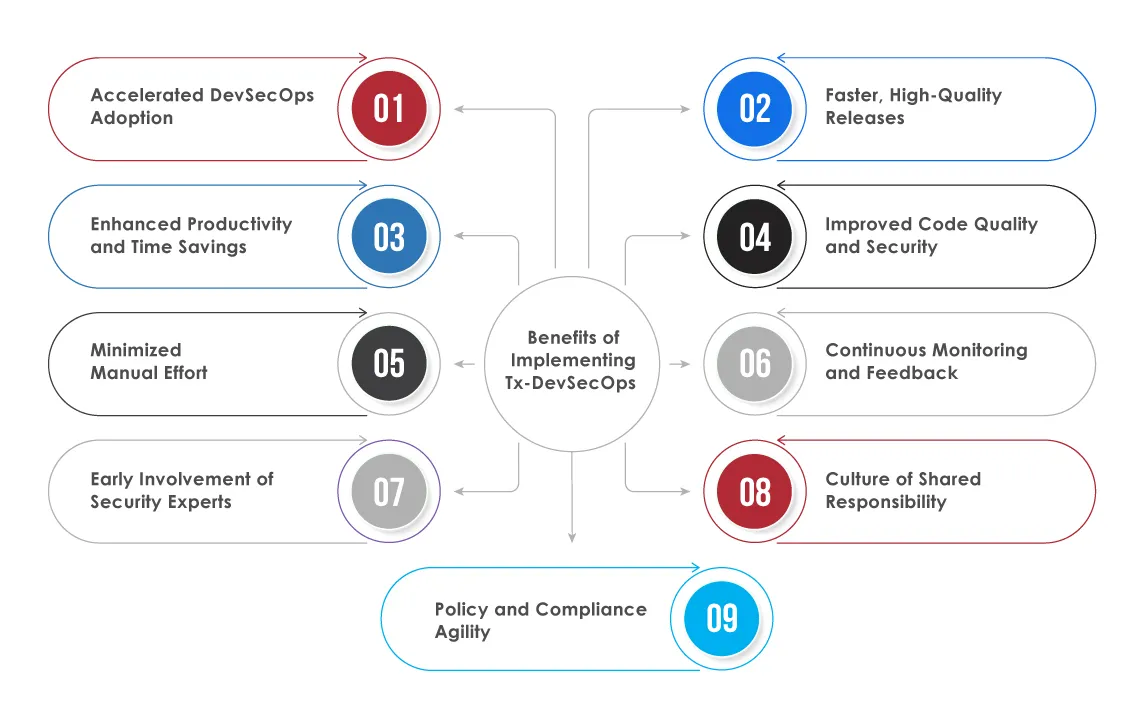
Accelerated DevSecOps Adoption:
Tx-DevSecOps helps businesses align their secure DevOps initiatives by providing a pre-built, scalable framework that integrates seamlessly into existing DevOps workflows.
Faster, High-Quality Releases:
By automating security checks and aligning DevSecOps best practices across the SDLC, Tx-DevSecOps ensures faster and more frequent releases without compromising quality. It supports effective CI/CD implementation, enabling rapid feature delivery and significantly reducing time to market.
Enhanced Productivity and Time Savings:
Organizations can save up to 25–30% of their time by leveraging the process visibility, automation, and streamlined workflows that Tx-DevSecOps enables. This leads to more efficient project execution and quicker decision-making.
Improved Code Quality and Security:
Tx-DevSecOps incorporates automated testing and security validations, improving code quality and reducing vulnerabilities. With comprehensive metrics and monitoring, teams can continuously enhance their security posture and application stability.
Minimized Manual Effort:
Automating security and compliance tasks across all development pipelines reduces the need for manual intervention. This allows teams to focus more on innovation and delivery while handling routine validations efficiently.
Continuous Monitoring and Feedback:
With real-time monitoring and integrated feedback loops, Tx-DevSecOps provides visibility into build, deployment, and runtime performance. This helps teams quickly detect and resolve issues, optimize reliability, and maintain consistent system health.
Early Involvement of Security Experts:
Security is embedded from the planning phase onward, ensuring that potential risks are identified and mitigated early in the cycle. This proactive approach reduces costly rework and enhances long-term software resilience.
Culture of Shared Responsibility:
Tx-DevSecOps supports collaboration by aligning development, operations, testing, and security teams. With shared goals and responsibilities, teams can deliver reliable, secure software faster and more consistently.
Policy and Compliance Agility:
Customizable pipelines and easy tool integrations simplify enforcing up-to-date security and compliance policies. Organizations stay aligned with evolving standards and regulations such as GDPR, OWASP, and PCI-DSS.
Summary
Tx-DevSecOps is a security automation accelerator designed to integrate robust security practices into the DevOps lifecycle without slowing development. As an extension of Txs’ Tx-DevOps framework, it addresses rising cyber threats by embedding security early using a shift-left approach. Tx-DevSecOps offers tool-agnostic integration, automated SCA, SAST, DAST checks, and compliance management to meet global standards. It enhances productivity, accelerates release cycles, and minimizes manual effort through continuous monitoring and feedback. By enabling collaboration and early risk mitigation, Tx-DevSecOps assists businesses in delivering secure, high-quality software quickly while maintaining a strong security posture and regulatory compliance.
The post Tx-DevSecOps – Bridging the Gap Between Security and Speed in DevOps first appeared on TestingXperts.
Source: Read More