- Cyber Insurance and Its Importance
- 5 Types of Cyber Insurance Coverage
- Risks Covered and Not Covered by Cyber Insurance
- Can Cyber Insurance Replace Cyber Defense?
- Summary
The number of cybercrimes is rising, and businesses are at risk of ransomware, data breaches, phishing, and other cybersecurity incidents. Statistically speaking, in 2024 Q3, an average of 1876 cyberattacks per enterprise were recorded, a 75% increase in cyber incidents compared to the 2023 Q3 and 15% more compared to the previous quarter. This period witnessed a significant rise in the intensity and volume of cyber threats businesses face, highlighting various tactics cybercriminals use to target victims and the urgency to reinforce cyber defenses. That’s where cyber insurance comes into the picture.
Although various tools and firewalls within an organization’s cybersecurity platform can protect them from breaches before they happen, they will still be held responsible in case sensitive information gets stolen. Cyber insurance helps minimize the aftermath of any cyber risk incident, especially financially.
Cyber Insurance and Its Importance

Cyber insurance, or cyber liability insurance, is a contract an organization purchases to reduce the financial risks associated with cybercrime, such as data breaches and cyberattacks. It protects businesses from internet-based threats affecting their IT infrastructure, data policy, and data governance. Traditional insurance schemes and commercial liability policies generally do not cover these aspects. Compared to well-structured insurance plans, cyber insurance policy underwriters have limited information to create risk models and curate insurance policy rates, premiums, and coverages.
Initially, cyber insurance focused only on data breaches and computer attacks. Still, as the decades passed, it now covers a broad spectrum of cybercrimes, such as cyber extortion, system failures, cybersecurity incidents causing business interruptions, etc.
Now the question is, why is it so important?
Electronic data theft would harm businesses, causing customer distrust and revenue loss. In such cases, business owners are held liable for damages caused by third-party data theft. One example that can explain the importance of cyber insurance is “The 2011 PlayStation Network outage.”
In 2011, a group of hackers hijacked Sony’s PlayStation Network, breaching and exposing 77 million PS users’ personally identifiable information (PII). The incident prevented PS console users from accessing the services for 23 days straight. Sony suffered a $171 million loss, which could have been lessened if they had a cyber insurance policy. Later, the court passed a judgment that Sony’s insurance policy only covers physical property damage, and they would have to incur the full amount of cyber damage costs.
Cyber insurance offers businesses the following benefits:
- Financial security against cyber incidents damage
- Network security coverage against cyber events
- Easy handling of complicated legal systems around cyber incidents
- Sense of security in terms of financial stability
- Improves reputation among stakeholders, partners, and customers
5 Types of Cyber Insurance Coverage
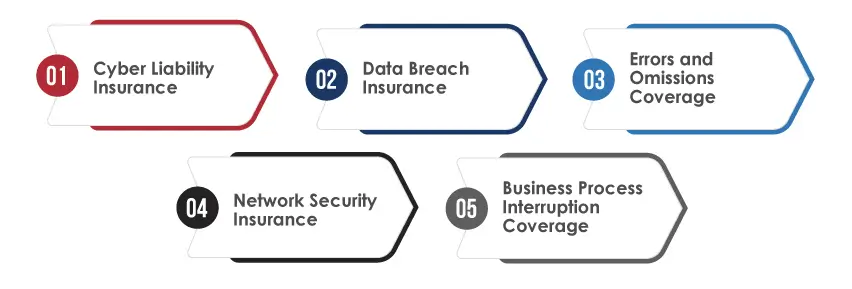
Cyber insurance offers the following coverages to protect organizations from security incidents:
Cyber Liability Insurance:
This type of insurance protects businesses from the financial costs associated with cyberattacks or data breaches. It covers regulatory fines, legal fees, and settlement amounts, protecting businesses from facing crippling expenses because of systems hacking or leakage of sensitive data.
Data Breach Insurance:
Businesses receive financial support to deal with the aftermath of data breaches. Data breach insurance covers costs associated with notifying affected parties, managing public relations, and providing credit monitoring services. It helps businesses minimize brand image damage and maintain customer trust.
Errors and Omissions Coverage:
E&O coverage secures businesses from cyber events that can affect service delivery and prevent contractual obligations from being fulfilled. This insurance coverage includes claims related to service performance failures or errors and protects against contract breach or negligence allegations.
Network Security Insurance:
This insurance coverage protects businesses from network security failure losses. It covers risks such as ransomware attacks, hacking, and malware injections. It also ensures businesses can steadily recover from cyber threats by covering the costs associated with communication, investigation, and remediation.
Business Process Interruption Coverage:
After a cyber incident disrupts an organization’s operations, business process interruption insurance helps cover lost revenue, and the expenses incurred during the recovery period. It ensures that businesses recover from downtime and continue to pay employees, infrastructure costs, and other expenses until they become stable.
Risks Covered and Not Covered by Cyber Insurance

| Category | Covered Risks | Not Covered Risks |
| Data Breaches | Costs covered related to notifying affected individuals, data restoration, and legal fees. | Fines or penalties imposed due to non-compliance with data security regulations. |
| Business Interruption | Revenue losses due to cyberattacks, such as DDoS attacks, ransomware, etc. | Losses due to outdated systems, avoidable vulnerabilities, poor system maintenance, etc. |
| Legal Liability | Lawsuits filed by third parties impacted by data breaches or cyberattacks. | Intentional or fraudulent activities conducted by employees. |
| Ransomware Extortion | Ransomware payments and professional negotiation services. | Payments to entities sanctioned by the government regulations. |
| Forensic Investigations | Expenses to identify the root cause and extent of a cyberattack. | Costs of ongoing system improvements that are not directly linked to the incident. |
| Reputation Management | Public relations costs to manage brand reputation after a cyber incident. | Long-term brand damage or loss of market share. |
| Third-party Vendor Breaches | Liability for breaches caused by service providers, such as cloud or network service providers. | Security gaps in contracts where no liability is outlined. |
| Employee Negligence | Data breaches that are caused unintentionally by employees. | Breaches that are caused by employees ignoring defined cybersecurity protocols. |
| Regulatory Investigations | Costs related to legal defenses during regulatory investigations. | Minor damages accumulated in legal cases. |
| Hardware Replacement | Costs to replace damaged or compromised hardware due to an attack. | Wear and tear or equipment failure unrelated to cyber events. |
Can Cyber Insurance Replace Cyber Defense?
No, cyber insurance cannot replace cyber defense, as businesses always need an effective cyber risk management policy. Although companies should have cyber insurance, it’s only one of the requirements among cybersecurity measures. Cybersecurity insurance is a complementary check to manage security protocols and balance the company’s risk management plan. It is an effective cybersecurity strategy to strengthen new or already established cyber defense mechanisms instead of an alternative or complete revamp.
Areas to Consider Before Applying for Cyber Insurance

Cyber insurance companies want to demonstrate their actions to protect their infrastructure against threats. If you, as an organization, did not take appropriate measures to protect your network, you may not be considered or approved for insurance. There are a few measures you have to consider before applying for cybersecurity insurance, which are given below:
- Despite having strong access controls, you must conduct regular vulnerability assessments, have an incident response plan, conduct regular employee training, and enable multi-factor authentication, encryption, and privileged access management.
- Should have an EDR (Endpoint Detection and Response) software to continuously monitor, detect, investigate, and respond to advanced endpoint threats.
- Must securely collect and store sensitive information such as financial information, supplier/customer data, etc.
- A comprehensive incident response plan documenting your business processes and procedures when a potential threat is detected.
By collaborating with a cybersecurity expert like TestingXperts (Tx) before applying for cyber insurance, you can ensure your organization is adequately covered and negotiate better with the insurer. At Tx, we can assist you by offering the following solutions:
Security Posture Assessment:
We conduct a detailed analysis of your current cybersecurity practices, identify vulnerabilities, assess risks, and provide recommendations to optimize overall security infrastructure. It will help make your organization resilient against cyber threats and meet insurance providers’ criteria.
Security Policies/Procedures Assessments:
We evaluate and help you optimize your security policies and operational procedures. Our experts ensure the policies align with best security practices and industry standards, such as data protection laws, accessibility standards, and incident response plans.
Compliance with Cyber Insurance Benchmarks:
Our experts help align your cybersecurity strategy with insurance provider benchmarks. This includes measures like conducting regular vulnerability assessments, having advanced threat detection systems, and implementing encryption protocols, which will assist you in negotiating favorable terms with insurers.
Summary
Cyber insurance is necessary for businesses to secure themselves from cyber incidents. They can get coverage from various risks, including legal liabilities, data recovery, business disruption, etc. while getting financial support during unforeseen cyber incidents. To qualify, businesses must implement security measures like incident response plans, threat detection tools, and vulnerability assessments. Partnering with Tx will ensure you have strengthened defenses while you meet insurance benchmarks and get comprehensive protection depending on your requirements. To know how Tx can help, contact our cybersecurity experts now.
FAQs
Q1. What is cyber protection insurance, and why is it important?
Cyber protection insurance or cyber insurance helps businesses protect themselves from financial losses due to cyberattacks and other cyber incidents. It is important for businesses that use laptops, smartphones, or other computer technologies for handling their operations.
Q2. Does every business need cyber insurance?
Cyber insurance protects businesses against cybercrimes, including social engineering scams and ransomware attacks. So yes, it is important for every business to have cyber insurance.
Q3. How can businesses improve their chances of qualifying for cyber insurance?
Businesses can improve their chances of qualifying for cyber insurance by implementing robust cybersecurity measures, conducting regular risk assessments, and using 2FA or multi-factor authentication.
Q4. How can TestingXperts (Tx) assist businesses in preparing for cyber insurance?
Tx assists businesses in preparing for cyber insurance by offering services like security posture assessment, security policies/procedures assessments, and ensuring compliance with cyber insurance benchmarks.
The post Digital Defense: How Cyber Insurance Shields Modern Enterprises first appeared on TestingXperts.
Source: Read More

