Qilin became the top ransomware group in April amid uncertainty over the status of RansomHub, according to a Cyble blog post published today.
RansomHub’s data leak site (DLS) went offline on April 1, and DragonForce claimed it had taken over RansomHub’s infrastructure and appealed to RansomHub affiliates to join it.
Instead, it appears that Qilin may have gained the most from the uncertainty, Cyble reported, as Qilin took over the top spot in April with 74 claimed victims (image below). DragonForce ended the month with 21 claimed victims.

Cyble said the RansomHub-DragonForce saga “highlights not only the volatility within the cybercriminal underworld but also the high-stakes competition driving rapid evolution in ransomware capabilities.”
Ransomware Attacks Declined in April
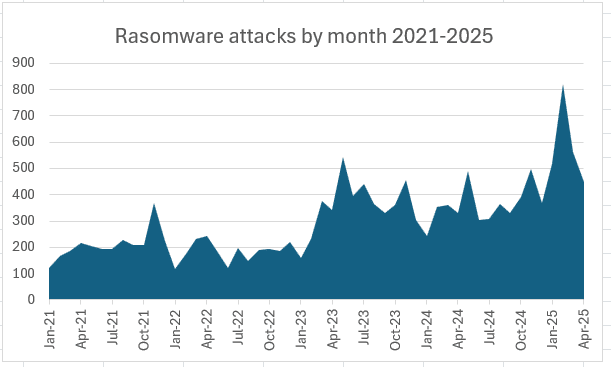
The total number of claimed ransomware attacks declined in April, Cyble said, as the uncertainty and chaos among the top groups may have had some effect.
Cyble recorded 450 claimed ransomware victims in April, down from 564 in March, but noted that “the long-term trend for ransomware attacks remains decidedly upward so April’s decline could be reversed as soon as new RaaS leaders are established.”
The U.S. led once again with 234 attacks, 52% of the global total (image below) and more than twice as many attacks as all of Europe (108).

Cyble noted some variations among the leading ransomware groups in global regions. RALord, a new group, was prominent in the META region (Middle East, Turkey and Africa), while Sarcoma claimed a number of victims in the Asia-Pacific and Australia-New Zealand regions. Play was the most active ransomware group targeting the U.S., with 42 victims.
Ransomware Attacks Threaten Software Supply Chain
Cyble recorded two new ransomware groups in April: Silent Team, which claimed two victims, a U.S.-based engineering company and a Canadian aerospace manufacturer; and Gunra, which claimed three victims – a Japan-based real estate company, a medical firm in Egypt, and a Panama-based beverage and distribution company.
Cyble noted a number of potentially serious ransomware incidents in April, some of which could result in software supply chain and downstream customer attacks.
- An IT services subsidiary of a large international conglomerate may have been victimized by the Akira ransomware group.
- The Play ransomware group claimed two U.S.-based software companies that provide critical services such as security applications, network operations center (NOC) solutions, and business consulting software, “raising concerns about potential downstream supply chain impacts.”
- Akira claimed responsibility for compromising a U.S.-based energy cooperative that supplies electricity to rural areas in ten northeast Georgia counties.
- Ransomware as a Service (RaaS) affiliate DevMan, working with DragonForce, claimed to have compromised a Chinese critical infrastructure construction company, and Qilin and DevMan claimed to compromise a Taiwan-based LCD technology company and a UAE-based IT and IT services company.
- Qilin claimed a France-based software provider serving the transportation and logistics industry as a victim. Exfiltrated data included source code, product development materials, and other sensitive data. Qilin also claimed a major South Korean industrial conglomerate as a victim.
- The Hellcat ransomware group said it compromised a China-based company specializing in display technologies and electronic solutions.
- The Rhysida ransomware group claimed as a victim a U.S.-based company involved in engineering, architecture, and critical infrastructure projects.
Cyble said the incidents highlight “the enduring importance of cybersecurity best practices for protecting against a wide range of cyber threats. Even as leading threat groups change, consistent application of good security practices is critical for building organizational resilience and limiting the impact of any cyberattacks that do occur.”
Source: Read More