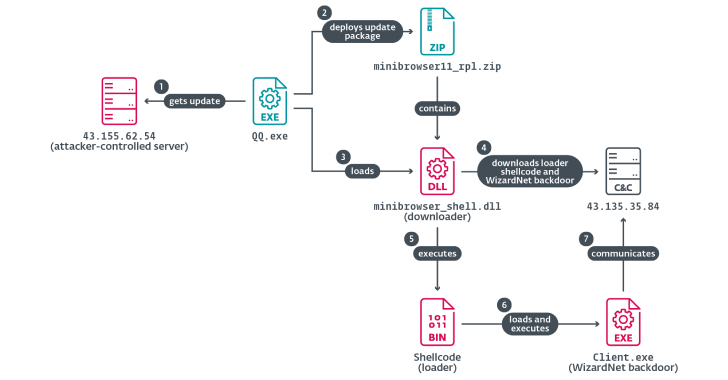
A China-aligned advanced persistent threat (APT) group called TheWizards has been linked to a lateral movement tool called Spellbinder that can facilitate adversary-in-the-middle (AitM) attacks.
“Spellbinder enables adversary-in-the-middle (AitM) attacks, through IPv6 stateless address autoconfiguration (SLAAC) spoofing, to move laterally in the compromised network, intercepting packets and
Source: Read More