Organizations demand for a scalable means to enforce security and governance controls across their database deployments without slowing down developer productivity. To address this, MongoDB introduced resource policies in public preview on February 10th, 2025. Resource policies enable organization administrators to set up automated, organization-wide ‘guardrails’ for their MongoDB Atlas deployments. At public preview, three policies were released to this end.
Today, MongoDB is announcing the general availability of resource policies in MongoDB Atlas. This release introduces seven additional policies and a new graphical user interface (GUI) for creating and managing policies. These enhancements give organizations greater control over MongoDB Atlas configurations, simplifying security and compliance automation.
How resource policies enable secure innovation
Innovation is essential for organizations to maintain competitiveness in a rapidly evolving global landscape. Companies with higher levels of innovation outperformed their peers financially, according to a Cornell University study analyzing S&P 500 companies between 1998 and 20231. One of the most effective ways to drive innovation is by equipping developers with the right tools and giving them the autonomy to put them into action2.
However, without standardized controls governing those tools, developers can inadvertently configure Atlas clusters to deviate from corporate or regulatory best practices. Manual approval processes for every new project create delays. Concurrently, platform teams struggle to enforce consistent security policies across the organization, leading to increased complexity and costs.
As cybersecurity threats evolve daily and regulations tighten, granting developers autonomy and quickly provisioning access to essential tools can introduce risks. Organizations must implement strong security measures to maintain compliance and enable secure innovation.
Resource policies empower organizations to enforce security and compliance standards across their entire Atlas environment. Instead of targeting specific user groups, these policies establish organization-wide guardrails to govern how Atlas can be configured. This reduces the risk of misconfigurations and security gaps.
With resource policies, security and compliance standards are applied automatically across all Atlas projects and clusters. This eliminates the need for manual approvals. Developers gain self-service access to the resources they need while remaining within approved organizational boundaries. Simultaneously, platform teams can centrally manage resource policies to ensure consistency and free up time for strategic initiatives.
Resource policies strengthen security, streamline operations, and help accelerate innovation by automating guardrails and simplifying governance. Organizations can scale securely while empowering developers to move faster without compromising compliance.
What resource policies are available?
| Policy Type | Description | Available Since |
|---|---|---|
| Restrict cloud provider | Ensure clusters are only deployed on approved cloud providers (AWS, Azure, or Google Cloud). This prevents accidental or unauthorized deployments in unapproved environments. This supports organizations in meeting regulatory or business requirements. | Public preview |
| Restrict cloud region | Limit cluster deployments in approved cloud providers to specific regions. This ensures data residency compliance, optimizes performance by keeping data close to users, and helps control cloud costs. | Public preview |
| Block wildcard IP | Reduce exposure to unauthorized access attempts by disabling the use of 0.0.0.0/0 (wildcard IP) in IP access lists. This enforces more restrictive network access policies, ensuring only explicitly approved IP addresses or private connectivity methods (such as VPC peering or private endpoints) are used. | Public preview |
| Enforce Atlas cluster size limits | Set minimum and maximum cluster sizes to control costs and optimize performance, preventing unexpected infrastructure expenses while ensuring efficient resource usage. | General availability |
| Restrict IP access list modifications | Restrict public access options by preventing new IP access list entries, encouraging connections through VPC peering or private endpoints. | General availability |
| Restrict VPC peering modifications | Maintain secure cross-VPC communication by preserving existing VPC peering configurations while blocking future changes. | General availability |
| Restrict private endpoint modifications | Protect private network connections by keeping existing Private Endpoint configurations intact and preventing unauthorized modifications. | General availability |
| Enforce minimum TLS version | Enforce modern TLS versions that prevent outdated encryption protocols from exposing your systems to vulnerabilities. | General availability |
| Restrict TLS cipher suites | Specify a set of TLS cipher suites to balance security, compatibility, and compliance. | General availability |
| Require maintenance windows | Implement mandatory maintenance windows for all Projects to improve operational predictability and create a structured framework for controlled system updates. | General availability |
When resource policies first launched in public preview, organizations could use them to enforce consistency in deployment configurations and strengthen access controls. These foundational policies helped teams ensure security and compliance requirements were being followed automatically:
Restrict cloud provider
Restrict cloud region
Block wildcard IP
The three inaugural policies available in public preview established a strong foundation for securing MongoDB Atlas environments while enabling self-service access for developers. With the general availability of resource policies, MongoDB is expanding its capabilities with seven additional policies designed to strengthen security, streamline compliance, and improve operational governance. These additions give organizations greater control over cluster configurations, network access, encryption standards, and maintenance schedules.
Without predefined guardrails, Atlas clusters can grow beyond manageable limits. Organizations are therefore prone to unforeseen infrastructure expenses and increased resource management complexity. To anticipate this risk, MongoDB has introduced the ‘Enforce Atlas cluster size limits’ resource policy to define and police relevant parameters.
Uncontrolled network access can expose sensitive data and increase security risks. Without guardrails, organizations may inadvertently allow overly permissive connections. This weakens security policy enforcement and puts compliance at risk. To mitigate these risks, the following resource policies have been introduced to ensure strict control over network configurations:
Restrict IP access list modifications
Restrict VPC peering modifications
Restrict private endpoint modifications
Weak or outdated encryption can leave sensitive data vulnerable to interception and compromise. Without strict enforcement of encryption standards, organizations risk non-compliance and exposure to evolving cybersecurity threats. To maintain robust data protection, MongoDB is introducing the following two resource policies to strengthen encryption controls:
Enforce minimum TLS version
Restrict TLS cipher suites
Unplanned maintenance can lead to downtime, operational disruptions, and inconsistent system updates. Without a structured approach, organizations will struggle to coordinate upgrades and minimize the impact on critical workloads. To enhance operation predictability, MongoDB has introduced the ‘Require maintenance windows’ resource policy to standardize maintenance scheduling.
Creating and managing resource policies
With the general availability of resource policies, organizations can now create and manage policies through the Atlas user interface (UI) and programmatically. This flexibility allows teams to enforce security, compliance, and operational standards in a way that aligns with their existing workflows.
For infrastructure automation, resource policies can be defined using infrastructure-as-code (IaC) tools like Terraform and CloudFormation or integrated directly via the Atlas Admin API. This enables organizations to apply policies consistently across their environments while maintaining agility.
Resource policies in Atlas are written using Cedar, an open-source policy language designed for both expressiveness and ease of use. Cedar’s concise syntax simplifies policy creation and management. This makes it easier for teams to enforce guardrails without unnecessary complexity.
To see the process of creating a resource policy through the Atlas UI in action, consider this example: A global financial services company uses MongoDB Atlas to support business-critical applications. To control costs and ensure performance consistency, the company wants to implement a resource policy restricting cluster provisioning to between M30 and M60.
To create the policy through the Atlas UI, a platform engineer would start by navigating to Organization Settings. They would then navigate to the Resource Policies page and select Create Policy to initiate the setup process.
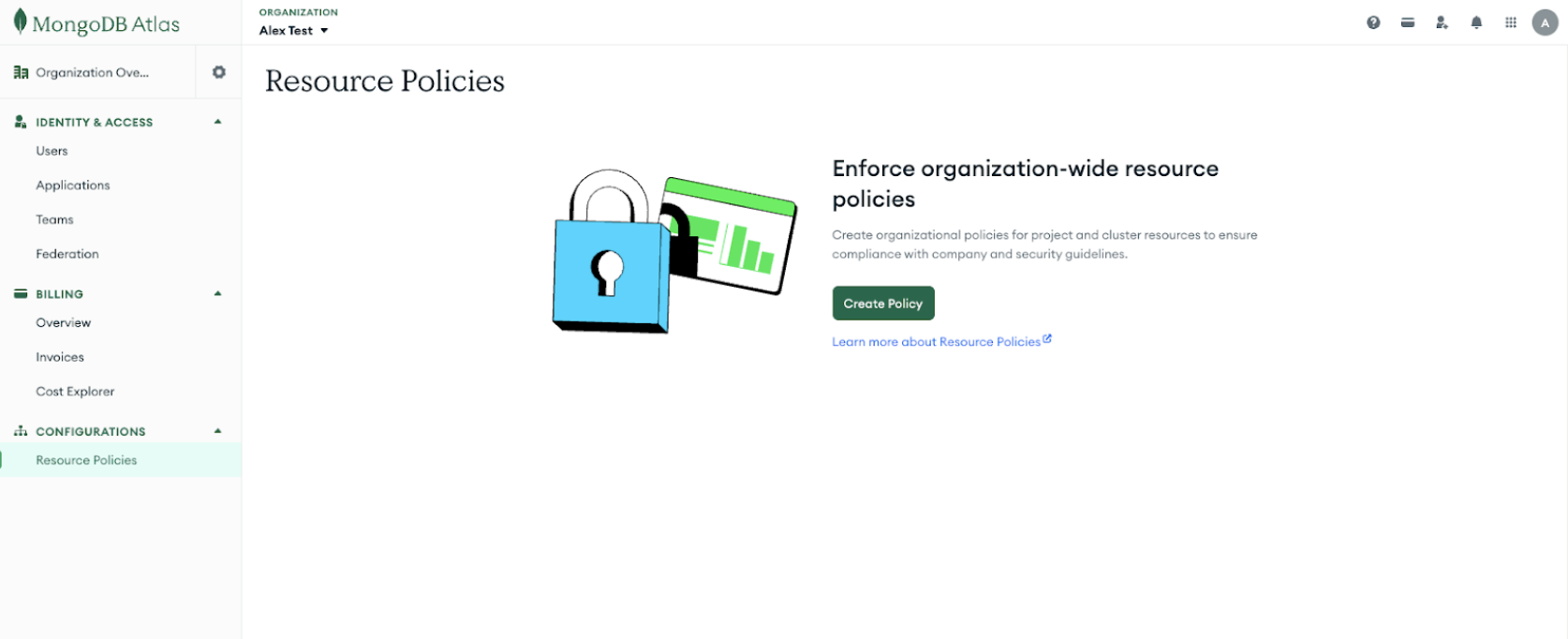
Next, the platform engineer would name the policy and provide a description. In this example, the policy is named “Restrict Cluster Tier,” with the description: “Restrict Atlas from provisioning or scaling clusters to less than M30 or greater than M60.”
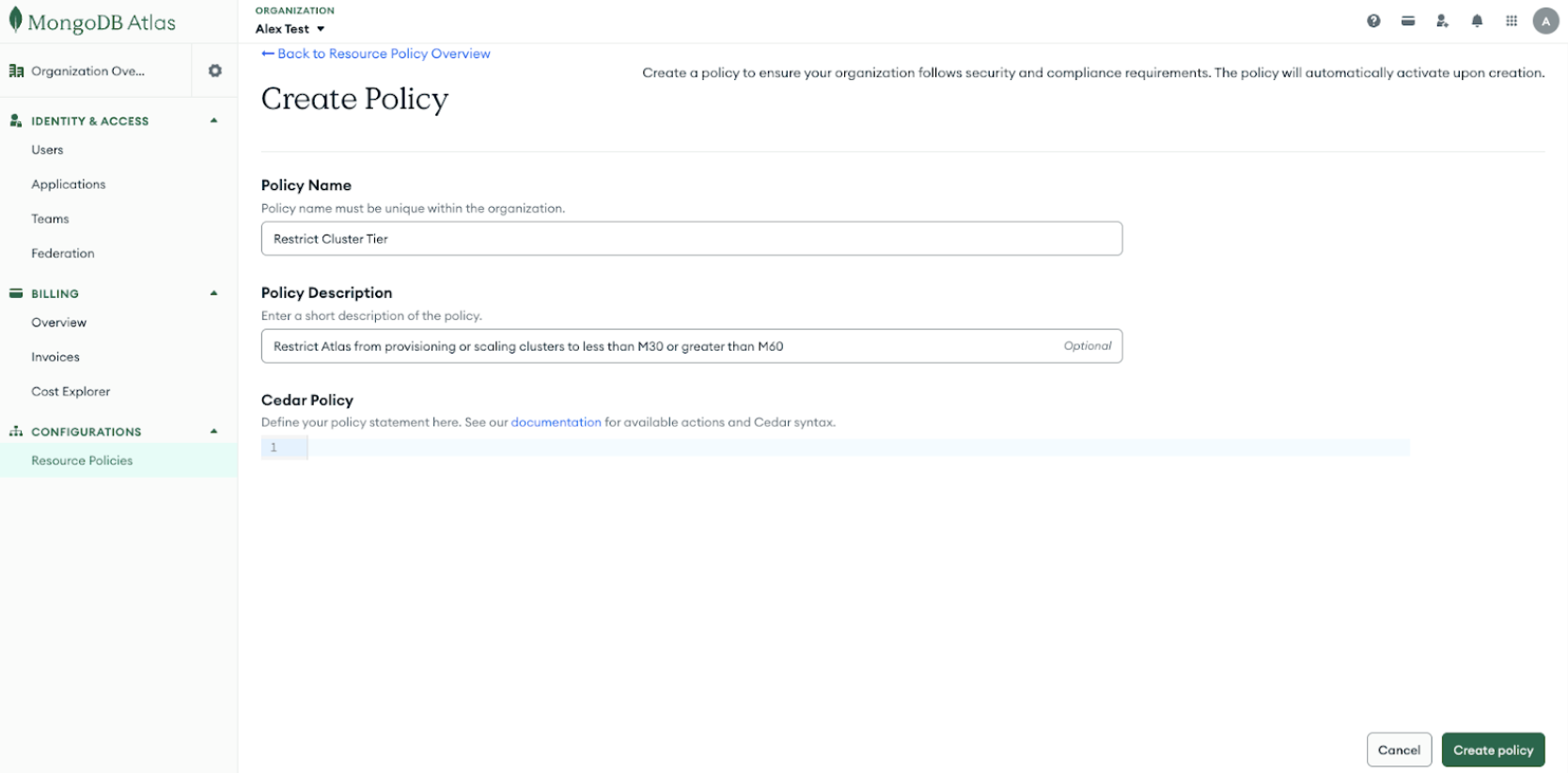
After naming the policy and providing a description, the next step is to define the policy using Cedar. In this case, the policy includes a when clause that restricts Atlas from provisioning or scaling clusters to less than M30 or greater than M60.
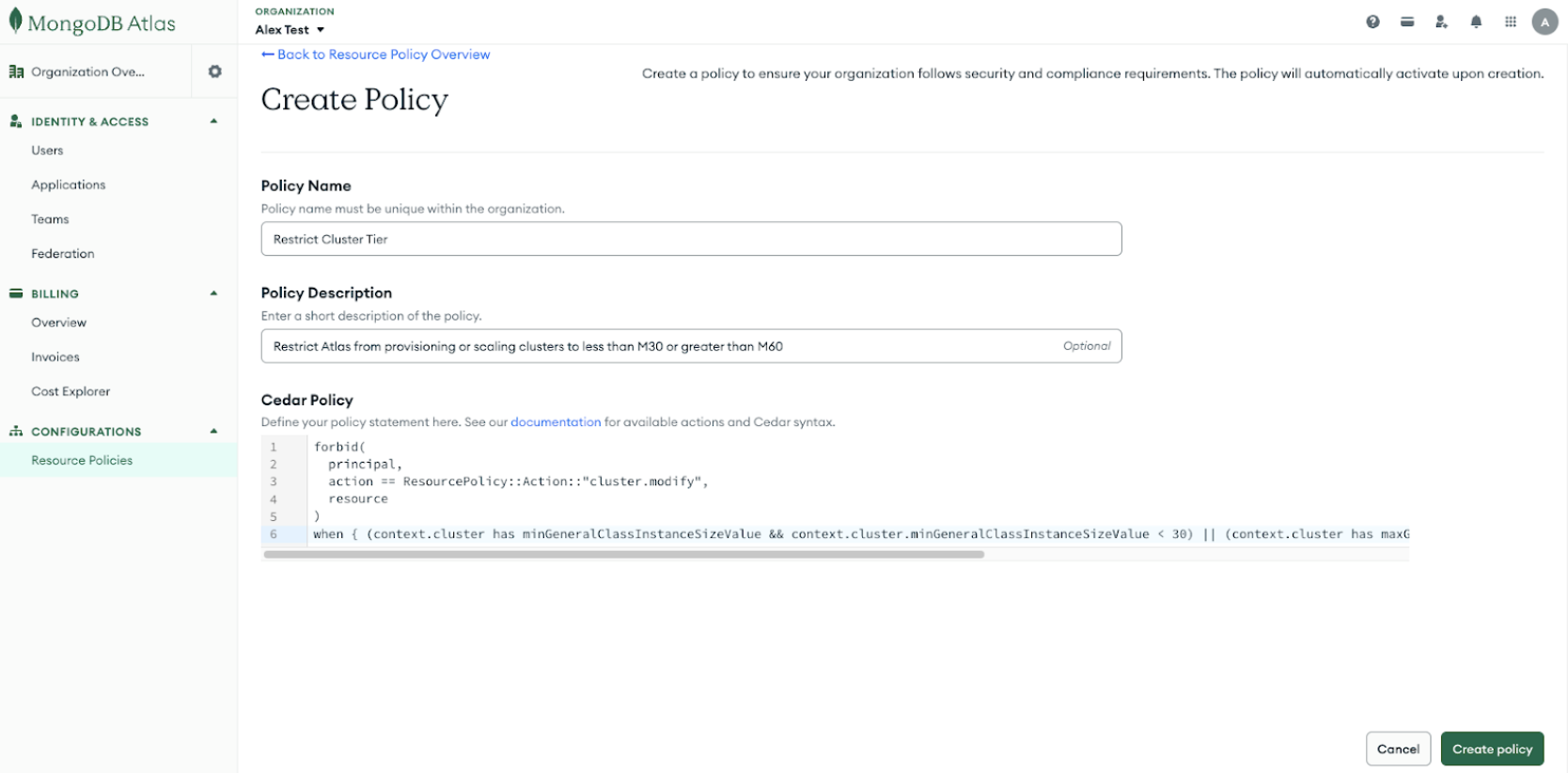
Finally, the policy is created and activated by clicking Create Policy. Once completed, the platform engineer can view an overview of the newly created policy.
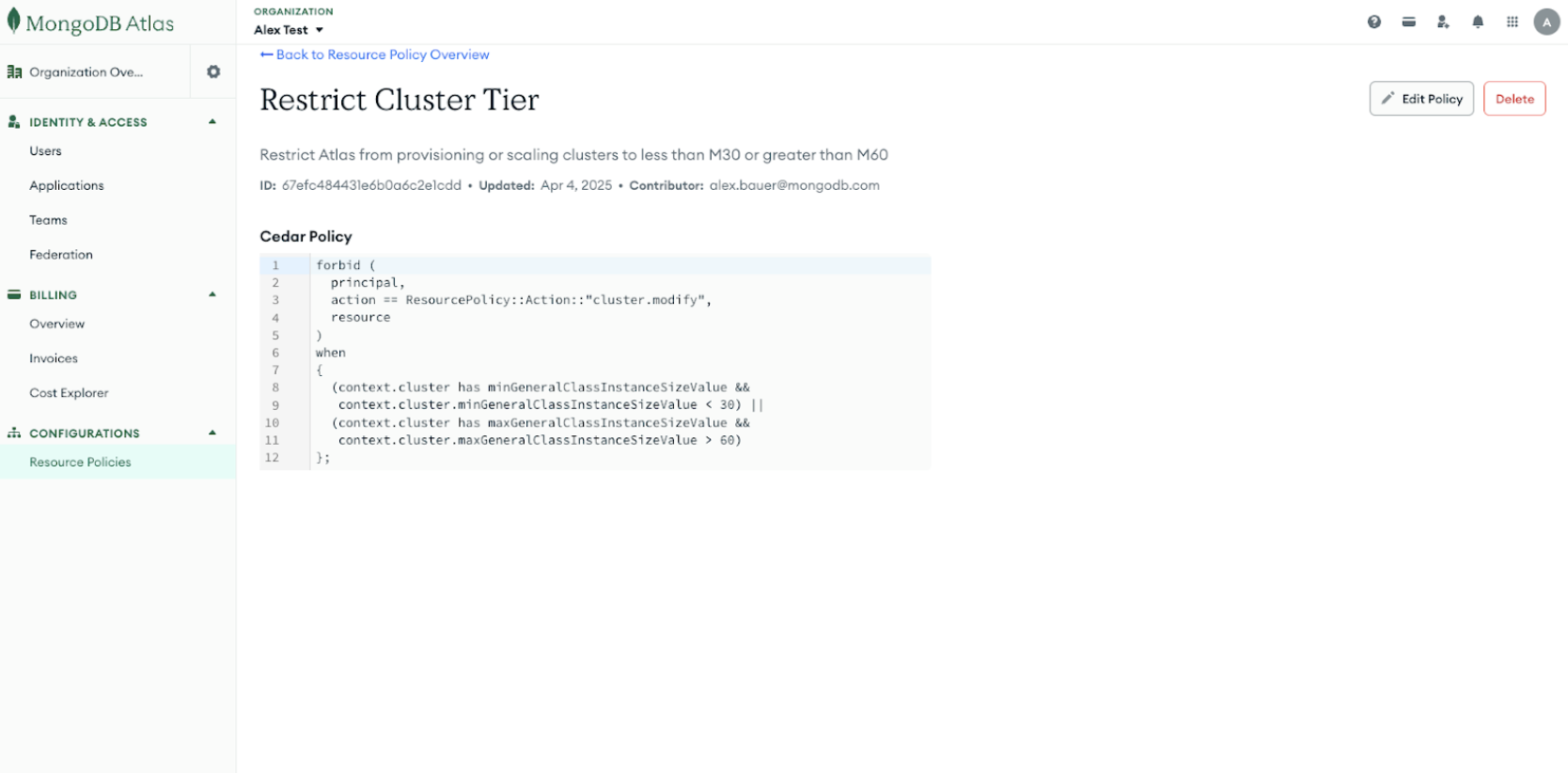
This resource policy now applies to all newly provisioned Atlas projects and clusters. For existing clusters that exceed or fall below the policy’s limits, Atlas only allows modifications that adjust them to comply with the policy. By implementing this policy, the financial services company prevents overspending. Concurrently, they ensure that production workloads run on appropriately sized clusters. Additionally, non-critical environments are prevented from consuming excessive resources.
Getting started with resource policies
Resource policies are now generally available in MongoDB Atlas. Get started creating and managing resource policies through the Atlas user interface or programmatically using infrastructure-as-code tools like Terraform or CloudFormation. Alternatively, integrate directly with the Atlas Admin API. Use the resources below to learn more about resource policies.
Source: Read More