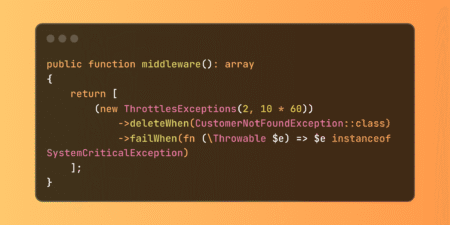
AI agents have rapidly evolved from experimental technology to essential business tools. The OWASP framework explicitly recognizes that Non-Human Identities play a key role in agentic AI security. Their analysis highlights how these autonomous software entities can make decisions, chain complex actions together, and operate continuously without human intervention. They’re no longer just tools,
Source: Read More