Cyble researchers have discovered a sophisticated malware attack that uses dual injection techniques to bypass Google Chrome’s App-Bound Encryption.
Chrome App-Bound Encryption was introduced last year to protect cookies from infostealer malware, so attacks that bypass that protection could potentially access user accounts and other sensitive information.
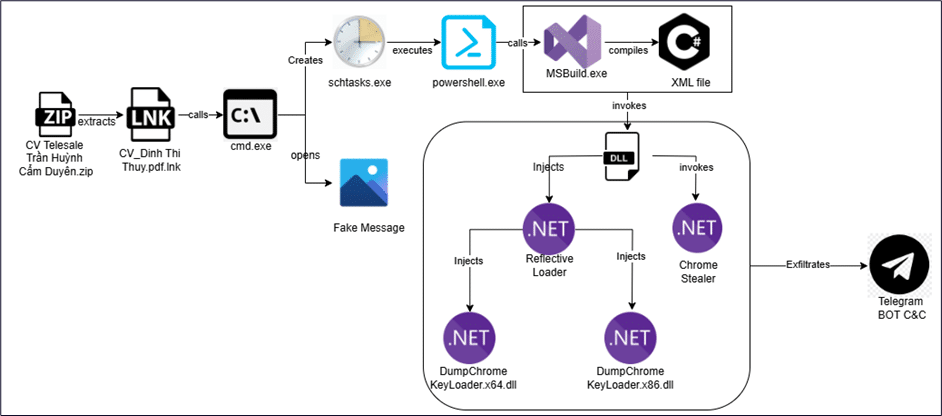
In a blog post this week, Cyble researchers detailed the sophisticated attack, which hides a malicious LNK file in a ZIP file – disguised as a PDF – and also makes a malicious XML project look like a PNG to trick users into opening it.
“This attack leverages fileless execution, scheduled task persistence, and Telegram-based communication to evade detection while stealing sensitive data,” the researchers wrote.
“By exploiting MSBuild.exe and using a double injection technique, the malware executes directly in memory, making it harder to detect. Its ability to bypass Chrome’s Application-Bound Encryption and extract credentials further strengthens its impact.”
Sophisticated Chrome App-Bound Encryption Bypass Detailed
The Cyble researchers said the file names suggest that the malware is “likely targeting organizations in Vietnam, particularly in the Telemarketing or Sales sectors.”
It’s not clear how the malware was initially delivered.
The researchers provided an in-depth analysis of the infection chain, which includes an LNK file that creates a scheduled task that runs every 15 minutes, using Microsoft Build Engine to deploy malicious C# code.
The shortcut file copies an XML project file to the Temp directory and initiates a command to create the scheduled task, which launches MSBuild.exe to execute embedded C# code from the XML file. “The malicious code operates within the MSBuild.exe process, deploying different components based on the system’s architecture,” the researchers wrote.
The double injection technique used by the malware — Process Injection and Reflective DLL Injection — allows it “to stealthily execute malicious code in memory without leaving traces on the disk, making it harder for traditional security solutions to detect.”
Telegram Web API Used for Command and Control
The malware uses the Telegram Web API to establish command and control communications with the threat actor (TA), and the malware “enables the TA to change the Telegram bot ID and chat ID as required, offering flexibility in controlling their communication channels.”
“The use of Telegram Web API for exfiltration and dynamic bot ID switching ensures continued control over infected systems,” the researchers said.
The threat actor can use that connection to issue a range of commands, such as bypassing Chrome App-Bound Encryption to steal an encryption key, deploying a custom info stealer, and exfiltrating sensitive user data from the Chrome browser, including cookies and login data.
To prevent falling victim to such attacks, Cyble recommended that organizations engage in user training, implement strict email attachment filtering and application whitelisting, and limit file execution paths and extensions, among other defensive steps.
The full Cyble blog includes in-depth analysis of the infection chain, communications and exfiltration, Indicators of Compromise (IoCs), and MITRE ATT&CK Techniques.
Source: Read More