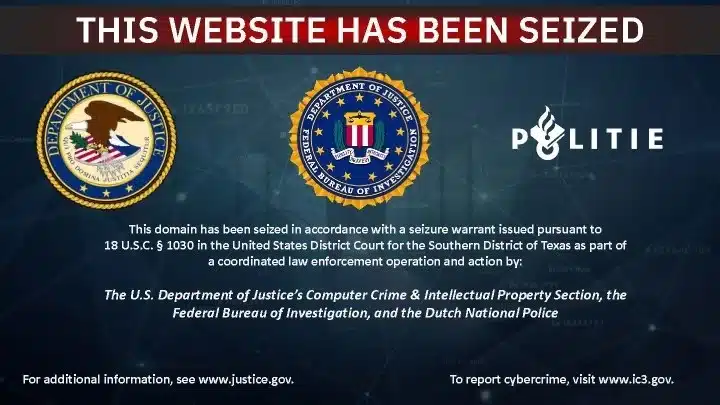
The Justice Department made a new move in disrupting an international network of cybercriminals by announcing the coordinated seizure of 39 cybercrime websites. These websites, associated with a Pakistan-based operation called the HeartSender, were used to sell hacking tools and fraud-enabling resources to transnational organized crime groups. The action was carried out in collaboration with the Dutch National Police.
The websites seized in this operation were linked to a group headed by Saim Raza, also known by the moniker HeartSender. Raza’s network has been active since at least 2020, providing malicious software and phishing toolkits that allowed cybercriminals to target victims, primarily in the United States. The group’s activities led to over $3 million in victim losses, and this seizure marks an important step in disrupting their operations.
The Cybercrime Websites and Tools Sold by the HeartSender Network
The cybercrime websites operated by Saim Raza served as marketplaces for various hacking tools, including phishing kits, scam pages, and email extractors. These resources are essential for launching and maintaining fraudulent schemes, particularly business email compromise (BEC) attacks, which have become a major source of financial losses globally. The tools offered by Raza’s network allowed cybercriminals to impersonate legitimate businesses and trick victims into transferring funds to accounts controlled by the perpetrators.

The websites not only provided the tools themselves but also offered training. Raza’s network took a unique approach by linking instructional YouTube videos, which demonstrated how to carry out various fraudulent activities using the tools. This effort made it easier for individuals with little to no technical expertise to execute complex scams. Cybercrime websites marketed these tools as “fully undetectable” by common antispam and security software, which made them highly appealing to cybercriminals looking to avoid detection.
Targeting Transnational Organized Crime Groups
The primary customers of these tools were transnational organized crime groups, who used them to facilitate a range of cybercrimes. A common scheme was business email compromise (BEC), where cybercriminals impersonate employees or vendors of a company to trick the organization into wiring large sums of money to fraudulent accounts. This type of attack often targets companies in the United States, resulting in severe financial losses.
In addition to BEC, the tools sold through these cybercrime websites were also used for identity theft, credential harvesting, and other forms of fraud. These activities have a devastating impact on victims, both financially and in terms of reputational damage. The Justice Department’s efforts to seize these domains aim to disrupt the flow of these tools and prevent further damage from being caused by Raza’s operation.
The Role of Law Enforcement in the Seizure
The successful seizure of these cybercrime websites was the result of close coordination between multiple law enforcement agencies. Supervisory Official Antoinette T. Bacon from the Justice Department’s Criminal Division, along with U.S. Attorney Nicholas J. Ganjei from the Southern District of Texas and Special Agent in Charge Douglas Williams from the FBI Houston Field Office, announced the operation. Their collective efforts underscore the importance of international collaboration in tackling cybercrime, as Raza’s network operated on a global scale.
The case is currently under investigation by the FBI Houston Field Office, with support from Dutch law enforcement agencies. The Justice Department expressed appreciation for the assistance provided by their Dutch counterparts, whose help was instrumental in executing this operation. Trial Attorney Gaelin Bernstein of the Criminal Division’s Computer Crime and Intellectual Property Section, along with Assistant U.S. Attorney Rodolfo Ramirez for the Southern District of Texas, are overseeing the prosecution of the case.
Impact and Ongoing Efforts
The seizure of 39 domains associated with HeartSender’s network is a major blow to the operation, but the Justice Department and its partners are committed to continuing their efforts to dismantle cybercrime networks. These websites were not only sources of hacking tools but also platforms for promoting and enabling widespread criminal activity. By disrupting these operations, the Justice Department aims to prevent further harm and send a clear message to those involved in cybercrime that their activities will not go unchecked.
As cybercrime continues to evolve, law enforcement agencies around the world must stay vigilant and collaborate across borders. The tools used by groups like HeartSender highlight the growing sophistication of cybercriminals, but also the growing resolve of law enforcement to combat these threats. The recent seizure is just one part of the larger effort to curb the rise of hacking tools and protect victims from cybercrime.
Source: Read More