Cyble dark web researchers have documented a new Russia-linked threat group that has been breaching critical infrastructure environments and tampering with system controls.
The group, Z-Pentest, has only been around for two months, yet already claims at least 10 operational technology (OT) control panel hacks, including a recent unverified claim that the threat actors had disrupted a U.S. oil well system.
The Cyble blog post also looked at the activity of an older Russian threat group, the People’s Cyber Army, also known as the Cyber Army of Russia Reborn, which claims at least eight breaches of U.S. water systems this year in addition to its other activities.
The hacktivist groups often cite support for Ukraine as the reason for their cyberattacks in the U.S. and other countries, which have included Canada, Australia, France, South Korea, Taiwan, Italy, Romania, Germany and Poland.
The two groups’ exploits also highlight the alarming state of U.S. critical infrastructure, which has also been targeted by China in possible preparation for cyber warfare with the U.S.
Z-Pentest’s Dramatic Videos
The two Russian groups have a flair for the dramatic. The Cyber Army of Russia, for example, posted screen recordings of members tampering with operational controls after breaches of water systems in Texas and Delaware in late August and September (screenshot of the Texas video below).

The People’s Cyber Army generated headlines earlier this year with a January attack that caused water storage tanks to overflow in Abernathy and Muleshoe, Texas. Water and wastewater systems are considered particularly vulnerable even among generally insecure critical infrastructure sectors.
Z-Pentest may be new on the scene, appearing for the first time in October, but in the two months the Serbian group has been operating, it has claimed at least 10 breaches of process control panels, in each case posting videos of members tampering with system settings.
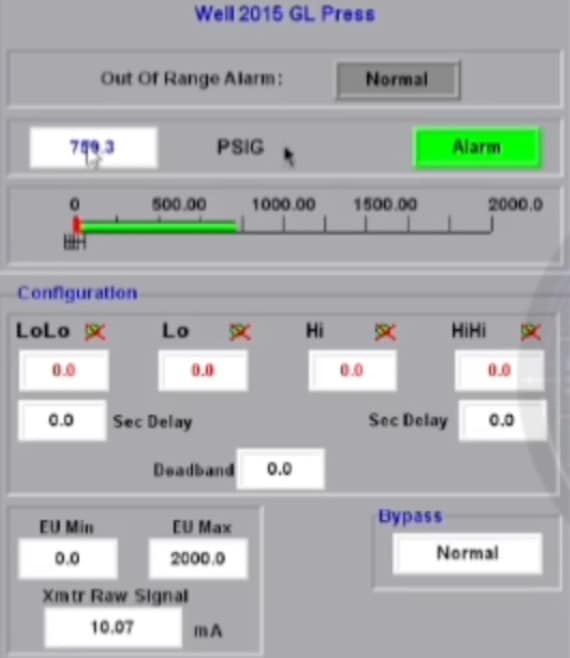
Within the last week, Z-Pentest’s claims have escalated to include claims of “disrupting critical systems at an oil well site, including systems responsible for water pumping, petroleum gas flaring, and oil collection,†according to the Cyble report.
A 6-minute screen recording captured detailed views of the facility’s control systems, showing “tank setpoints, vapor recovery metrics, and operational dashboards, allegedly accessed and changed during the breach.â€
It is not clear where that oil facility is located, but two other U.S. oil facility claims made by the group appear to correspond with known locations and companies.
How Much Critical Infrastructure Damage Can Hackers Do?
While the hackers appear to be able to access sensitive environments, Cyble noted that it’s not clear how much damage they could do. Programmable logic controllers (PLCs) “often include safety features that can prevent damaging actions from occurring, but the fact that such environments are accessible to threat actors is nonetheless concerning,†the researchers said.
Cyble also noted a general increase in threat activity targeting the energy sector in recent months. Dark web claims and ransomware attacks have increased, and network access and zero-day vulnerabilities have been offered for sale on dark web marketplaces. Cyble also noted instances “where credentials for energy network access were offered for sale on the dark web before larger breaches and attacks occurred, suggesting that monitoring for credential leaks may be an important defense for preventing larger breaches later.â€
Cyble said Z-Pentest “should be taken seriously, as the group has demonstrated an apparent ability to penetrate these environments and access – and tinker with – operational control panels.â€
The researchers also offered security recommendations for operational technology and critical infrastructure environments, noting that they often can’t afford downtime and typically have end-of-life devices that can’t be patched.
Source: Read More