Last month’s attack on supply chain management platform Blue Yonder has been attributed to a new ransomware group known as “Termite.â€
The ransomware attack hit several downstream customers, including retail and manufacturing operations, and Blue Yonder continues to work at getting them all back online.
Cyble researchers examined the new ransomware strain in a technical blog and said it is “essentially a rebranding of the notorious Babuk ransomware.†So far the new ransomware group has claimed seven victims – two each in the U.S. and France, and one each in Oman, Germany and Canada.
Termite Ransomware Binary Analyzed
Cyble researchers examined a Termite ransomware binary that was first identified by PCrisk and determined that it was largely similar to the existing Babuk ransomware.
After executing, the ransomware invokes the SetProcessShutdownParameters(0, 0) API “to ensure that its process is one of the last to be terminated during system shutdown,†Cyble said. “This tactic is used to maximize the time available for the ransomware to complete its encryption process.â€
The ransomware then terminates services on the victim machine to prevent interruptions during the encryption process, and terminates backup processes if those are running too.
The malware’s vssadmin.exe process deletes all Shadow Copies to prevent system recovery after files have been encrypted, and the ransomware empties the recycling bin too to prevent any files there from being recovered.
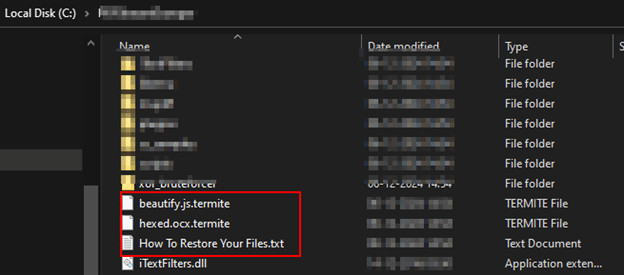
The ransom note dropped by the ransomware instructs victims to visit the onion site for additional information (image below).

After leaving the ransom note, the malware encrypts files on the victim machine and appends the “.termite” extension.
Termite ransomware can also locate network shares and retrieve information about shared resources on a server, checking for the $ADMIN share and encrypting the files. The ransomware can also identify network drives connected to the infected machine and encrypt the files.
‘A New and Growing Threat’
The Cyble researchers said Termite ransomware is “a new and growing threat in the cyber landscape, leveraging advanced tactics such as double extortion to maximize its impact on victims. … The emergence of Termite underscores the critical need for robust cybersecurity measures, proactive threat intelligence, and incident response strategies to counter the evolving tactics of ransomware groups.â€
The Blue Yonder ransomware attack also delivers a fresh reminder of the attraction of the software supply chain for threat actors, with their ability to infect or disrupt a whole lot of companies in one attack.
The full Cyble blog digs deep into Termite ransomware’s processes, including indicators of compromise (IoCs) and MITRE ATT&CK techniques.
Source: Read More