
In today’s world of microservices and distributed applications, ensuring secure communication between services is essential. Unlike user authentication, which relies on interactive logins, service-to-service (S2S) authentication uses tokens or certificates to build trust between services without manual intervention. Okta, a leading identity and access management (IAM) solution, simplifies this process, providing robust tools to manage S2S authentication with ease.
This guide will walk you through setting up secure S2S authentication with Okta, using OAuth 2.0 and the Client Credentials Grant to protect your application’s data and resources effectively.
What is Okta?
Okta is a leading Identity and Access Management (IAM) platform designed to securely authenticate users and services across various devices and applications. With Okta, businesses can rely on a robust, cloud-based solution that protects access to applications, APIs, and IT infrastructure, while efficiently managing user identities.
Key Features of Okta
- Single Sign-On (SSO): Enables users to access multiple applications with a single secure login, enhancing convenience and security.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring users to verify their identity with more than just a password.
- API Access Management: Enforces granular access controls for APIs, issuing tokens to secure microservices interactions.
- Role-Based Access Control (RBAC): Grants access rights based on user or service roles, ensuring access is limited to essential functions only.
Also Learn: Auth0 by Okta RBAC with Spring Boot | Secure Access Integration Guide
Why Microservices Need Service-to-Service Authentication
In microservices architectures, where multiple services interact across networks, secure communication is vital. Without strong service-to-service (S2S) authentication, services may access one another freely, risking unauthorized data exposure. Here’s how S2S authentication benefits microservices:
- Prevents Unauthorized Access: Ensures only authorized services communicate, mitigating security risks.
- Secures Data Integrity: Protects sensitive data from unauthorized access, preserving information accuracy.
How Okta Streamlines Service-to-Service Authentication
Okta simplifies S2S authentication by managing service credentials centrally and issuing secure, scoped tokens. Here’s how Okta enables secure, efficient S2S authentication:
- Centralized Credential Management: Manages all service identities in one secure location.
- Scoped Tokens for Authentication: Issues service-specific tokens with limited lifespans to control access.
- Role-Based Access Control (RBAC): Defines roles and permissions to restrict access to authorized functions.
Steps to Implement Service-to-Service Authentication with Okta
Step 1: Register and Log into Okta Developer Account
- Create a New Okta Account: If you don’t already have a developer account, register on Okta’s website (Okta Developer).
- Log in to the Okta Dashboard: After registration, access the Okta Dashboard to begin setting up S2S authentication.
Step 2: Create a Service Application in Okta
- Create a New Application: Go to the Applications section in the Okta Dashboard, then select “Create App Integration.â€
- Select Sign-In Type: Choose from options like OIDC, SAML 2.0, SWA, or API Service.
- Choose Application Type: Specify if it’s a Web Application, Single Page Application, Native Application, etc.
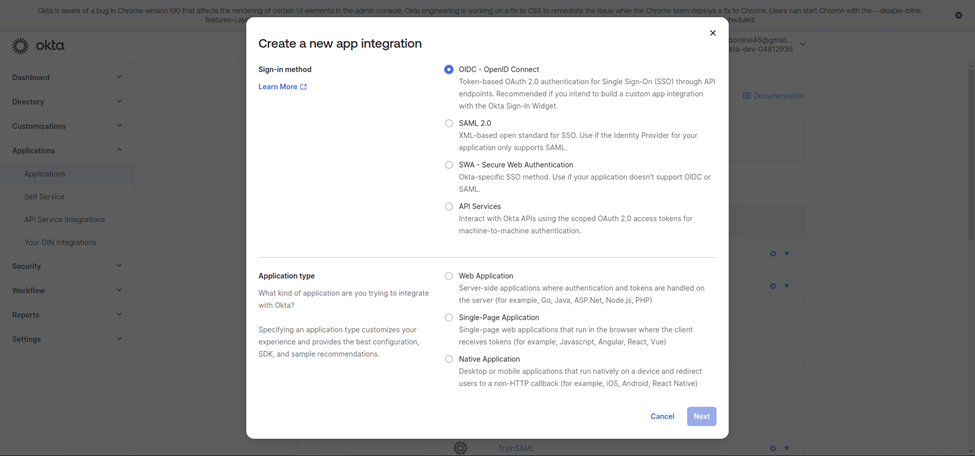
1. Name Your Application Integration
- Provide a clear, descriptive name to identify your application integration within Okta’s dashboard.
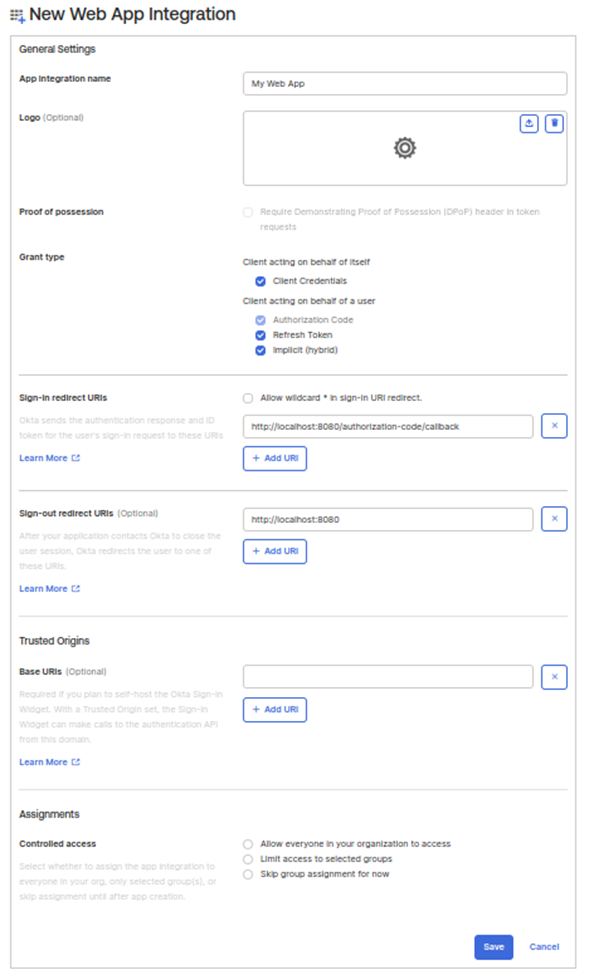
2. Select Grant Type(s)
Choose the relevant grant types based on your application needs, such as:
- Client Credentials
- Authorization Code
- Refresh Token
- Hybrid
3. Configure Redirect URIs
- Sign-In Redirect URI: Specify the URI for user redirection after a successful sign-in.
- Sign-Out Redirect URI (Optional): Define where users will be redirected after sign-out.
4. Set Up User Access Assignments
- Allow Everyone in Your Organization: Grant access across your organization.
- Limit Access to Selected Groups: Restrict access to specific groups as needed.
- Skip Group Assignment for Now: Select this option to assign group access later.
5. Save Client ID and Client Secret:
- Once setup is complete, save the Client ID and Client Secret. These credentials are critical for securely connecting and authenticating services.
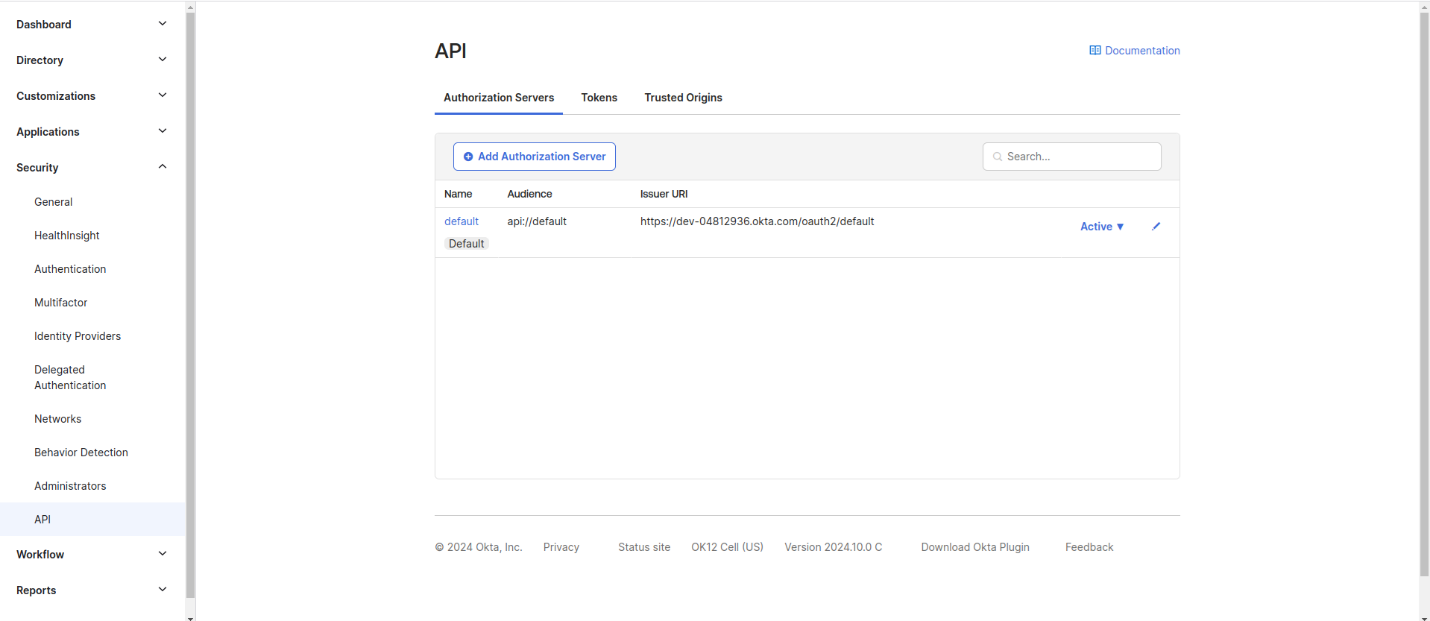
Step 3: Configure Access Policies and Assign Scopes
- Set Up Scopes for Your Application:
- Go to Security > API in your Okta dashboard.
- Select Authorization to assign scopes that specify the permissions available to this application.
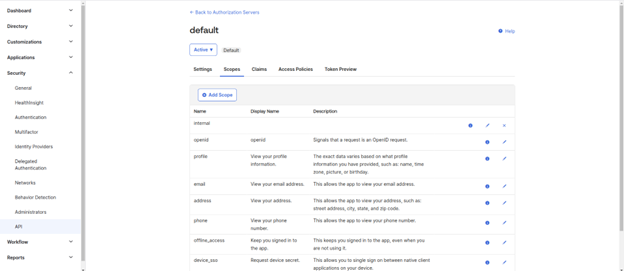
- Define Custom Scopes (If Needed):
- If your application requires specific access beyond default scopes, create and assign custom scopes tailored to your needs.
- Update Access Policies (Optional):
- Adjust access policies to further define who can access this application and under what conditions. This step is useful for organizations with detailed access requirements.
Step 4: Set Up Your Spring Boot Application for Secure Service-to-Service Authentication
To facilitate secure communication between microservices, let’s set up two essential services in Spring Boot: resource and client. Here’s a step-by-step guide to implement Okta’s authentication protocol:
1. Define Resource and Client Services:
- Create two services, namely
resource(service that provides resources) andclient(service that accesses resources).
2. Add Required Maven Dependencies:
- In your
resourceservice, include the following Maven dependencies in thepom.xmlfile:

3. Configure Okta Authentication in Application Properties:
- In both
resourceandclientservices, configure Okta in theapplication.ymlorapplication.propertiesfiles as follows:

- Replace
${CLIENT_ID},${CLIENT_SECRET}, andYOUR_OKTA_DOMAINwith the values from the Okta application you created.
4. Establish Security Configuration for the Resource Service:
- Set up a security configuration class to require authentication for every request to the
resourceservice:
- This configuration enforces JWT token validation on each request, making sure only authenticated clients can access the service.
5. Create a Controller for the Resource Service:
- Define a simple controller to handle requests in the
resourceservice:
6. Set Up Client Service to Communicate with Resource Service:
- In the
clientservice, configure a controller to authenticate and communicate with theresourceservice using Okta tokens.
7. Run and Test Both Services:
- Once both services are up and running, test the communication. Unauthorized access attempts to the
resourceservice should return a401 Unauthorizedresponse. Authorized calls via theclientservice will successfully retrieve data, showing how Okta seamlessly manages service-to-service authentication.
This setup enhances service-to-service authentication security in microservices environments using Okta’s centralized identity management, securing data, and streamlining access.
Final Steps: Running and Testing Service-to-Service Authentication
- Run Both Services: After completing the configuration, start both your
resourceandclientservices. - Verify Security Measures: If you attempt to directly access the
resourceservice API without going through theclientservice, you should receive a401 Unauthorizederror. This confirms that the resource service is protected and only accessible to authenticated requests through Okta.
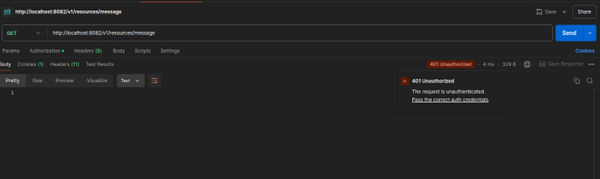
- Authenticated Access via Client Service: When you call the
clientservice API, you should receive a200 OKresponse. This happens because Okta generates an access token internally, which is then added to the request header. Upon reaching theresourceservice, Okta verifies the token automatically, allowing secure access to the endpoint.
The Bottom Line
Implementing service-to-service authentication is critical in any microservices setup, and Okta simplifies the process significantly. With features like Client Credentials Grant, scoped tokens, and centralized credential management, Okta ensures that only authorized services communicate within your architecture. By following these steps, your organization can secure service-to-service interactions, enhance data integrity, and mitigate unauthorized access risks.
If you’re looking to strengthen your microservices security, Okta’s robust IAM tools provide an excellent foundation for secure, scalable authentication. For organizations aiming to streamline their security without compromising on functionality, partnering with an experienced AI Development Company like Inexture can make all the difference.
The post Secure Service-to-Service Communication with Okta appeared first on Inexture.
Source: Read MoreÂ



