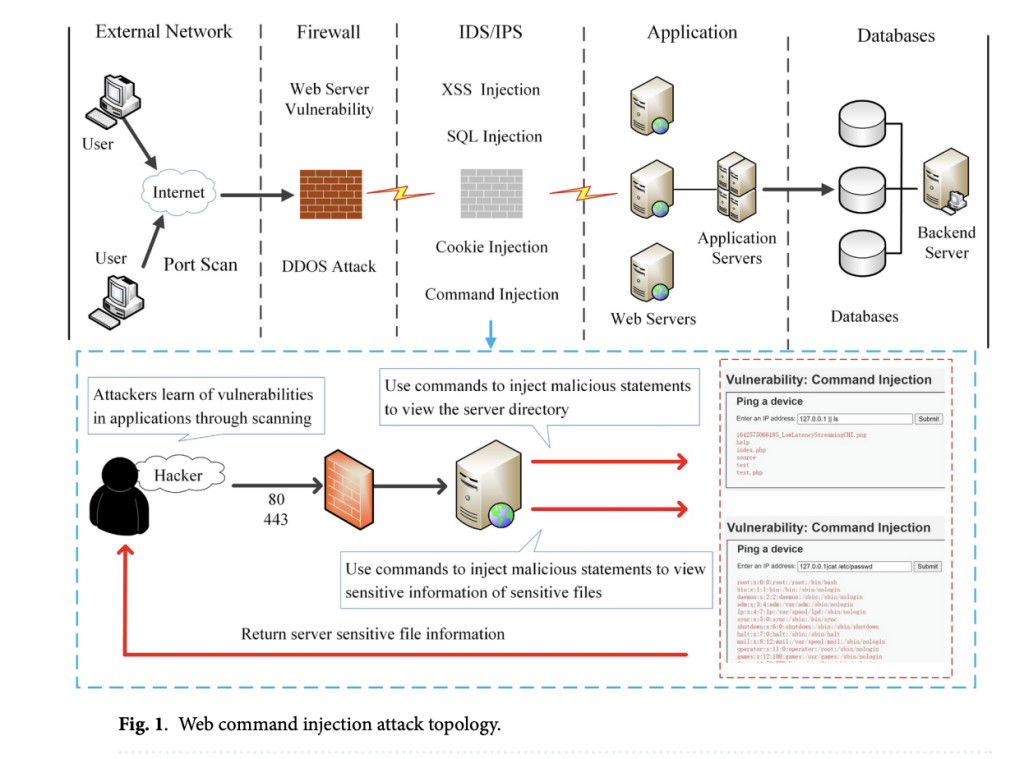
Web command injection attacks pose a critical security risk to web applications, often resulting in server information leaks or severe disruptions. As these attacks become increasingly complex and obfuscated, traditional detection methods struggle to identify malicious code and extract relevant features effectively. Recent incidents highlight the prevalence of such vulnerabilities, with attackers exploiting command injection flaws in major systems, leading to unauthorized remote access and control. Despite these attacks’ rising frequency and severity, limited research addresses their detection, particularly in web applications, underscoring the need for focused study to mitigate potential risks effectively.
Research on detecting web command injection attacks is limited, though past studies have highlighted some advances and gaps. Traditional methods, like the Commix tool, offered early detection capabilities but lacked real-time detection functions. Later studies integrated machine learning and deep learning to improve accuracy and automate feature extraction, significantly enhancing detection capabilities. For instance, models like CNN, DNN, and LSTM were explored for injection attack detection, with notable advances using BERT-based techniques. Despite improved performance, these methods often require manual feature extraction and have primarily focused on general injection attacks rather than those specific to web applications.
Researchers at Harbin University have developed the Convolutional Channel-BiLSTM Attention (CCBA) model, an advanced deep learning approach to detect web command injection attacks. The CCBA model uses dual CNN channels for thorough feature extraction, a BiLSTM network for bidirectional temporal feature analysis, and an attention mechanism to prioritize critical features. Achieving 99.3% accuracy and 98.2% recall on real-world data, the model’s robustness was further validated with high accuracy on popular cybersecurity datasets. This end-to-end approach, which eliminates the need for manual feature extraction, significantly outperforms existing methods in web command injection detection.
The method comprises preprocessing and model recognition phases. In preprocessing, the dataset is prepared and split into training and test sets, then cleaned, decoded, and segmented using special symbols to facilitate the model’s analysis. Text is embedded using Word2Vec for words and character embeddings for symbols during model recognition. Features are extracted through a dual-CNN structure with convolutional layers targeting words and symbols, producing feature vectors for classification. A BiLSTM with an attention mechanism emphasizes key elements in the data, enhancing semantic understanding. The model is optimized with Adam, with loss calculated based on sample classification accuracy.
The proposed model focuses on identifying malicious network activities, particularly web command injection attacks, within extensive network traffic data. The evaluation process involved cross-validation with diverse datasets, including samples from enterprise environments, CTF competitions, and open-access platforms. The model’s effectiveness was confirmed through comparative analysis with leading deep learning approaches and cross-domain evaluations. Ablation studies highlighted the attention mechanism’s role in boosting accuracy and convergence speed. Achieving 99.21% accuracy, this model outperformed many existing methods, with cross-domain testing yielding high effectiveness in detecting SQL injection and XSS attacks while remaining efficient for real-time deployment.
The study explores web command injection attacks, proposing a hybrid deep learning model—CCBA—to enhance detection. The CCBA model uses dual CNN channels for thorough feature extraction, a BiLSTM network for bidirectional analysis of temporal features, and an attention mechanism to prioritize critical elements, boosting detection accuracy. Tested on both real-world and public cybersecurity datasets, CCBA achieved impressive results, with 99.3% accuracy and 98.2% recall.Â
Check out the Paper. All credit for this research goes to the researchers of this project. Also, don’t forget to follow us on Twitter and join our Telegram Channel and LinkedIn Group. If you like our work, you will love our newsletter.. Don’t Forget to join our 55k+ ML SubReddit.
[Trending] LLMWare Introduces Model Depot: An Extensive Collection of Small Language Models (SLMs) for Intel PCs
The post Enhanced Detection of Web Command Injection Attacks Using a CNN-BiLSTM Attention Model for Real-Time Application Security appeared first on MarkTechPost.
Source: Read MoreÂ
![Why developers needn’t fear CSS – with the King of CSS himself Kevin Powell [Podcast #154]](https://devstacktips.com/wp-content/uploads/2024/12/15498ad9-15f9-4dc3-98cc-8d7f07cec348-fXprvk-450x253.png)