A critical remote code execution (RCE) vulnerability in Zimbra email servers is under active attack, and users are urged to patch immediately.
Zimbra is already a popular target for hackers – CISA’s Known Exploited Vulnerabilities catalog listed 9 Zimbra vulnerabilities before adding the new one late today, and Cyble sensors show more than 90,000 web-exposed Zimbra servers with previously reported vulnerabilities, so it’s not surprising that the latest vulnerability (CVE-2024-45519) is already finding favor with attackers. MITRE has rated the new vulnerability a 10.0 under CVSS 3.1, while NVD rated it 9.8.
Zimbra postjournal Vulnerability
Researchers were labeling the vulnerability in Zimbra’s postjournal SMTP parsing service as critical even before MITRE and NVD rated it.
A Proof of Concept (PoC) reported by ProjectDiscovery researchers demonstrated that the vulnerability could be exploited with specially crafted emails, and exploits began within a day of that.
The postjournal service is not enabled by default, but some researchers found the vulnerability nonetheless alarming.
Security researcher Will Dormann called the Zimbra flaw “an embarrassingly bad vulnerability.â€
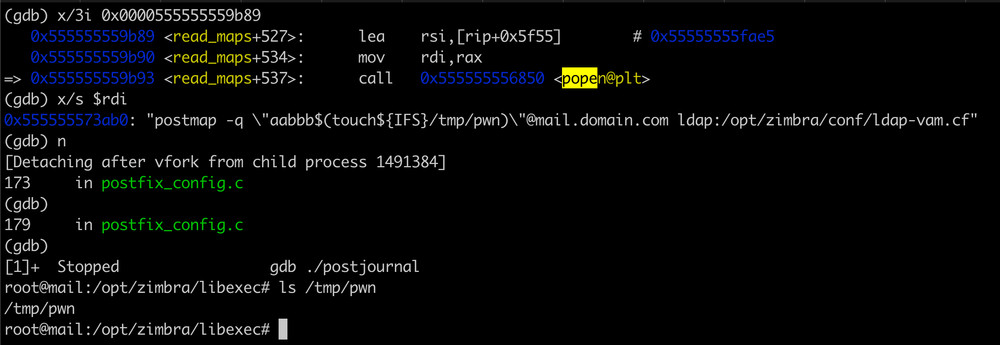
“The vulnerable code appends the attacker-provided email address to a command line and then runs it with popen() (which uses a shell),†Dormann wrote on Mastodon. “Guess what happens when the email address has a backticks, a semicolon, $(), etc? What year is this?
“Luckily the attack vector to get there (postjournal) isn’t enabled by default, as there are exploitation attempts occurring in the wild.â€
Dormann said exploitation of the vulnerability is “pretty trivial. When the mail server handles an email address with shell escape characters, the postjournal binary just shells out and runs whatever is specified.”
Malicious emails exploiting the vulnerability have been identified as coming from 79.124.49[.]86.
The Zimbra postjournal service vulnerability allows unsanitized user input to be passed to popen, enabling attackers to inject arbitrary commands. Patched versions add input sanitization and replace popen with execvp to mitigate the direct command injection vulnerability. Zimbra administrators should also check the configuration of the mynetworks parameter to prevent external exploitation.
Zimbra Vulnerability Details
The ProjectDiscovery researchers reversed the postjournal binary and found that there were no calls to execvp or the run_command function, and a direct call to popen instead went to the read_maps function, which allowed input to be passed without sanitization. The cmd argument could also be bypassed with $() syntax, allowing for exploit via port 10027. The same exploit over SMTP port 25 required the postjournal service to be enabled, which was accomplished with a Bash script:
zmlocalconfig -e postjournal_enabled=true
zmcontrol restart
To enable remote exploit, the researchers found that the mynetworks default configuration included a /20 CIDR range of their public IP address. “This means that the exploit could still be performed remotely if the postjournal service is enabled and the attacker is within the allowed network range,†they wrote.
Soon after the PoC was published, Proofpoint researchers observed the vulnerability under exploitation, with spoofing emails sent to fake addresses in CC fields to get Zimbra servers to parse and execute them as commands. The addresses contained base64 strings that were executed with the sh utility.
Some of the emails used CC addresses to build a webshell on a vulnerable Zimbra server. The full CC list was wrapped as a string, and if connected, the base64 blobs decoded to a command to write a webshell to /jetty/webapps/zimbraAdmin/public/jsp/zimbraConfig.jsp.
Base64 Zimbra email exploit (Proofpoint)Once installed, the webshell listens for inbound connections and supports command execution via exec or download over a socket connection.
Zimbra administrators are urged to:
Disable postjournal if it’s not required
Configure mynetworks to prevent unauthorized access
Apply the latest security updates directly from Zimbra
Source: Read More