Cyber and law enforcement agencies from the U.K., U.S., and Australia have come together to expose the Russian cybercriminal empire of Evil Corp and its affiliation with the LockBit ransomware operators. Sanctions, seizures and arrests followed in at least eight announcements from the various agencies.
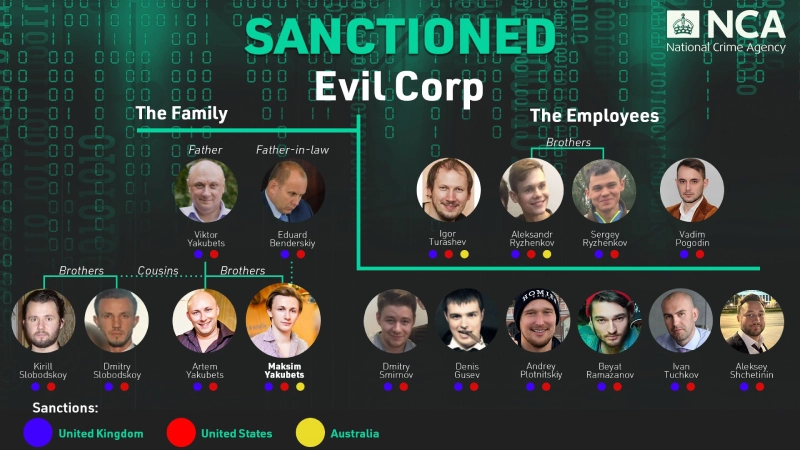
The joint international effort led to a fresh wave of sanctions against individuals associated with the notorious cybercrime group Evil Corp and exposed its affiliate ties to LockBit. Sixteen individuals have been sanctioned, including high-profile members with connections to Russian state entities and the ransomware group LockBit.
Evil Corp, long regarded as one of the most sophisticated cybercrime organizations, has seen its operations disrupted. However, the group’s criminal influence continues to reverberate across the globe, specifically through its role in developing ransomware strains like BitPaymer and its evolution to using LockBit ransomware.
A Deep-Rooted Cybercrime Legacy
Evil Corp’s history is intertwined with both financial crime and nation-state interests, according to an investigation led by the UK’s National Crime Agency (NCA). Initially a Moscow-based financial crime outfit, it later transformed into a full-fledged cybercrime syndicate, amassing over $300 million from healthcare, critical infrastructure, and government victims globally.
The group’s leader, Maksim Yakubets, and his close associate Igor Turashev, were indicted by the U.S. in 2019 for their role in orchestrating attacks using Dridex malware—a tool designed to steal banking credentials and deliver ransomware payloads.
Source: FBIThis week’s sanctions target an additional seven members – apart from the seven already indicted by the U.S. in 2019, including Yakubets’ father, Viktor Yakubets, and Aleksandr Ryzhenkov, a key figure behind LockBit ransomware.
Ryzhenkov has been identified as a pivotal operator responsible for some of the most damaging ransomware attacks facilitated by LockBit. He was also charged by the US Department of Justice for his role in deploying BitPaymer ransomware to extort American organizations.
Left to Right: Dmitriy Slobodskoy, Maksim Yakubets, Artem Yakubets, Kirill Slobodskoy (Source: NCA)Evolving Tactics Amid Sanctions
In response to the 2019 sanctions, Evil Corp adjusted its methods, adopting tighter security measures and shifting from high-volume ransomware attacks to more targeted strikes against high-revenue businesses. This evolution allowed the group to continue its operations under the radar of law enforcement. The group was forced to innovate after its original tools, like BitPaymer and Dridex, became well-known and defendable by security systems.
Source: NCALockBit’s rise has offered former Evil Corp members a lucrative alternative. Developed under the ransomware-as-a-service model, LockBit allows cybercriminals to rent the ransomware infrastructure, which helps shield the creators from direct involvement in attacks. The connection between Evil Corp and LockBit shows the shifting trend in the cyber underworld—where major ransomware groups often cooperate, despite claims of separation.
The Global Pushback
The latest phase of Operation Cronos—an international law enforcement effort—continues to erode LockBit’s capabilities. France, Spain, and the UK coordinated a series of arrests targeting LockBit affiliates, including a developer and bulletproof hosting infrastructure facilitator. Those arrests, coupled with the seizure of nine key servers used by LockBit, mark a significant setback for the group.
In the last two years, LockBit has emerged as the most active ransomware group globally, targeting sectors ranging from finance to energy. Its infrastructure and attack model have been resilient, with law enforcement facing challenges in fully disrupting its operations. However, as the NCA tightens the noose around Evil Corp and its LockBit affiliates, the frequency and intensity of ransomware incidents have started to wane.
‘No More Ransom’ Initiative Gains Momentum
The takedown of ransomware groups is only one part of the global effort to combat cyber extortion. Europol, in collaboration with Japan’s cybersecurity teams, has advanced its efforts in developing decryption tools for ransomware victims. Over 6 million users have accessed these tools via the “No More Ransom†portal, saving billions in potential damages.
Europol also continues to provide critical support in tracing cryptocurrency transactions linked to ransomware operations. Through seven dedicated technical sprints, Europol has traced key financial exchanges, helping to identify LockBit and Evil Corp actors.
Strong Message from World Leaders
UK Foreign Secretary David Lammy emphasized the impact of these sanctions on Russia’s cybercriminal ecosystem. “Putin’s corrupt regime cannot continue its malign influence through criminal networks. Today’s action sends a strong message that we will use every tool at our disposal to stop cyber attacks against our allies.â€
In Washington, the Treasury’s Office of Foreign Assets Control (OFAC) reiterated its commitment to safeguarding critical infrastructure against cyber threats. Acting Under Secretary Bradley T. Smith noted that the sanctions underscore collective international resolve to thwart ransomware actors. “Our coordinated efforts with the UK and Australia aim to dismantle the economic framework that allows these criminal groups to thrive.â€
A Critical Turning Point?
While Evil Corp’s influence has diminished since 2019, its shadow still looms large over the global ransomware landscape. Investigators believe that many of its top operators continue to collaborate with other crime syndicates, creating complex webs of cybercriminal activity. LockBit’s developers have publicly distanced themselves from Evil Corp, but the sanctions and arrests suggest otherwise.
The arrest of a LockBit developer in France, along with the seizure of servers used to facilitate ransomware attacks, are signs that the walls are closing in on these criminal networks. Still, with ransomware being a multi-billion-dollar industry, it’s unlikely that either Evil Corp or LockBit will disappear overnight. Their evolution reflects the adaptability of cybercriminal organizations—a cat-and-mouse game where the stakes grow higher with each move.
Moving Forward
As cybersecurity practitioners and law enforcement agencies collaborate across borders, ransomware attackers are increasingly finding fewer places to hide. The collaborative efforts seen in Operation Cronos offer a glimpse into the future of cyber defense—where governments, private companies, and international organizations work in unison to thwart cybercrime at every level.
For CISOs, network engineers, and security practitioners, the takeaways from this operation are clear: ransomware is not just a technological threat, but a global geopolitical weapon. Preparing for these evolving threats requires not just technical defenses, but a deep understanding of the global cyber landscape.
This story will continue to evolve, as Operation Cronos and its counterparts say the operation is still ongoing.
Source: Read More