U.S. intelligence agencies issued a warning today about a Chinese botnet that has compromised 260,000 devices around the globe, including small office/home office (SOHO) routers, firewalls, network-attached storage (NAS) and Internet of Things (IoT) devices from some of the biggest names in IT and networking.
The FBI, National Security Agency (NSA) and the Cyber National Mission Force (CNMF) said in the advisory (PDF) that People’s Republic of China (PRC)-linked cyber actors have used the botnet to deploy distributed denial of service (DDoS) attacks and compromise targeted U.S. networks. In a separate announcement, the U.S. Justice Department said today that the botnet has been disrupted by a court-authorized law enforcement operation.
Investigators have observed a total of 66 CVEs targeted in the campaign, in products and services from organizations such as ServiceNow, Fortinet, Zyxel, Apache, QNAP, Â F5, Ivanti, Juniper, Citrix, WordPress, Ubiquiti, Confluence, Atlassian, Cisco, Netgear, IBM, D-Link, Microsoft, and even the widespread CVE-2024-4577 PHP vulnerability.
U.S. agencies were joined by the “Five Eyes” alliance partners – cybersecurity agencies from Australia, New Zealand, Canada and the UK – in the announcement.
Chinese Botnet Linked to Company, Threat Groups
Integrity Technology Group, a PRC-based company with links to the Chinese government, has controlled and managed the botnet, which has been active since mid-2021 and was identified last year by Black Lotus Labs, which dubbed the botnet “Raptor Train.”
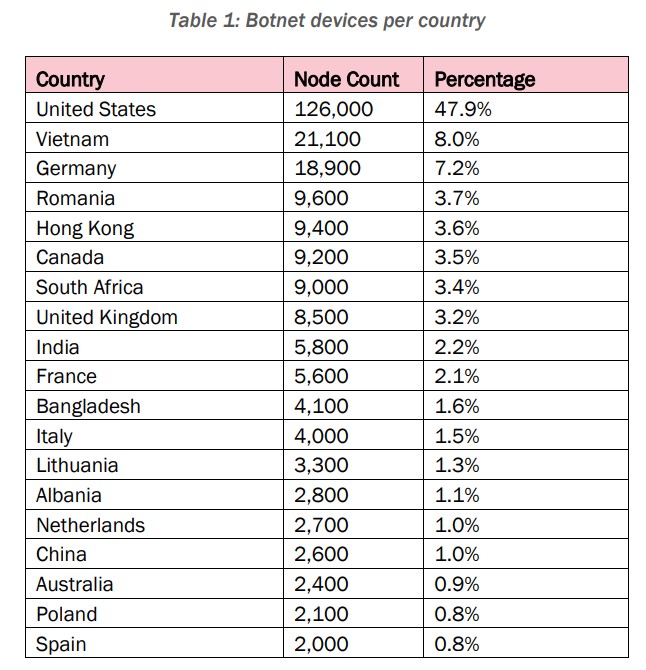
The botnet has regularly maintained “between tens to hundreds of thousands of compromised devices,†and as of June 2024, consisted of over 260,000 devices, nearly half of which are in the U.S. Victim devices have been observed in North America, South America, Europe, Africa, Southeast Asia and Australia.
“While devices aged beyond their end-of-life dates are known to be more vulnerable to intrusion, many of the compromised devices in the Integrity Tech controlled botnet are likely still supported by their respective vendors,†the advisory said.
Integrity Tech has used China Unicom Beijing Province Network IP addresses to control and manage the botnet. The same China Unicom Beijing Province Network IP addresses were also used to access other operational infrastructure used in computer intrusion activities against U.S. victims, the agencies said.
The FBI has engaged with multiple U.S. victims of these intrusions “and found activity consistent with the tactics, techniques, and infrastructure associated with the cyber threat group known publicly as Flax Typhoon, RedJuliett, and Ethereal Panda.â€
C2 Servers Use Specific Domain; Other IoCs Shared
The botnet uses the Mirai family of malware to hijack IoT devices, including webcams, DVRs, IP cameras, and routers running Linux-based operating systems. More than 50 different Linux versions have been observed in the infected devices, spanning Linux kernel versions 2.6 through 5.4.
The payload starts processes on the device to establish a connection with a command-and-control (C2) server using TLS on port 443. The malware also makes requests to “c.speedtest.net,†and over 80 subdomains of “w8510.com†were linked to the botnet’s C2 servers.
A tier of upstream management servers using TCP port 34125 manage the botnet’s C2 servers. These management servers host a MySQL database that contained over 1.2 million records of compromised devices, both previously and actively exploited.
NSA Recommendations
The NSA said it released the advisory “to help National Security Systems, Department of Defense, and Defense Industrial Base networks mitigate these cyber threats.â€
The advisory’s authors recommend the following mitigations:
Regularly apply patches and updates, using automatic updates from trusted providers when available.
Disable unused services and ports, such as automatic configuration, remote access, or file sharing protocols, which threat actors may abuse to gain initial access or to spread malware to other networked devices.
Replace default passwords with strong passwords.
Implement network segmentation with the principle of least privilege to ensure IoT devices within a larger network pose “known, limited, and tolerable risks.â€
Monitor for high network traffic volumes to detect and mitigate DDoS incidents.
Plan for device reboots to remove non-persistent malware.
Replace end-of-life equipment with supported devices.
Source: Read More
![Why developers needn’t fear CSS – with the King of CSS himself Kevin Powell [Podcast #154]](https://devstacktips.com/wp-content/uploads/2024/12/15498ad9-15f9-4dc3-98cc-8d7f07cec348-fXprvk-450x253.png)