Cybersecurity is a fast-paced area wherein knowledge and mitigation of threats are most necessary. In this respect, the attack graph is one tool that security analysts mainly resort to for charting all possible attacker paths to the exploitation of vulnerabilities within a system. The challenge of managing vulnerabilities and threats has increased with modern systems’ enhanced complexity. Traditional methods of attack graph generation, most of which are manual and strongly reliant on expert knowledge, need revision. Given the fast-growing complexity of such systems and the threats’ dynamics, there is a natural demand for more efficient and adaptive approaches in threat modeling and attack graph generation.
One of the major problems in cybersecurity today is that the vulnerability landscape keeps changing. New vulnerabilities are continuously discovered, and attackers develop new exploitation methods. Static rules, heuristics, and manual curation shackle classic attack graph generation methods. These approaches are time-consuming and usually cannot provide the extent of coverage needed. This gap exposes systems to such emerging threats that could not be captured by those static models previously. This would, in turn, require a much more dynamic approach to keep up with the rapidly changing threat environment.
Currently, manual curation and computational algorithms are used to create attack graphs. Formal definitions and model-checking algorithms form the basis of current techniques for creating attack graphs. Still, these techniques are normally specific to a domain and inflexible when introducing new types of attacks. For instance, conventional methods involve a lot of manual input of information on the vulnerability; this could be better, considering that new vulnerabilities are being found almost daily. Often, such approaches only utilize static formal definitions of an attack, which cannot be dynamically applied to new attack vectors. All this brings out the reality that there is a need for a new approach that can adapt dynamically to new information upon its reception.
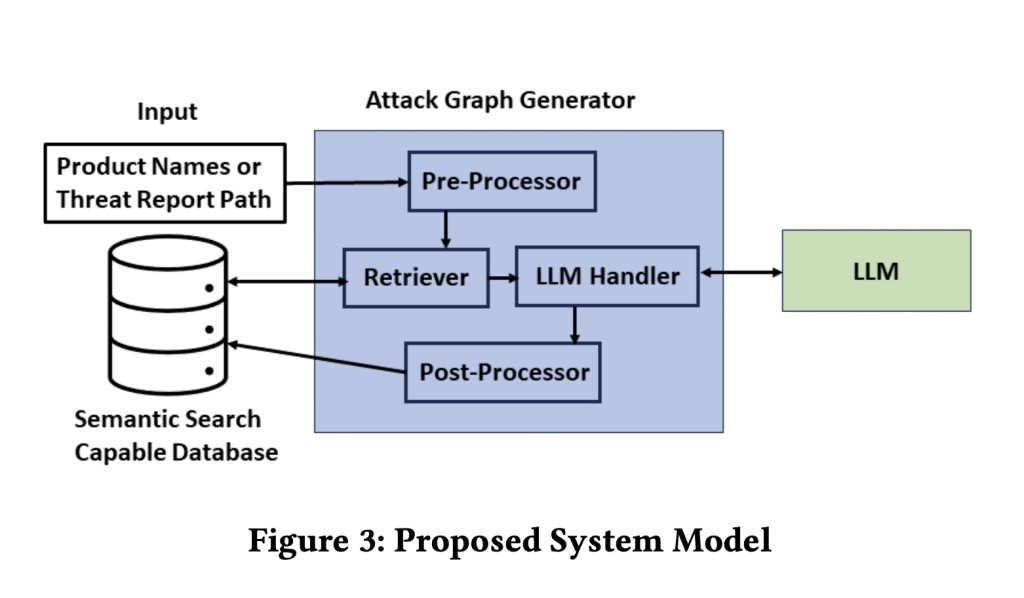
A research team from the University of California Irvine and Cisco Research has proposed another line of work in a new approach toward automated attack graph generation using retriever-augmented LLMs, namely CrystalBall, leveraging GPT-4. This approach automates chaining CVEs according to their preconditions and postconditions, supporting dynamicity and scalability in attack graph generation. It is designed to process large volumes of unstructured and structured data and fits modern cybersecurity environments. The research team has worked particularly on integrating LLMs with a retriever model that improves the accuracy and relevance of the attack graphs generated.
The underlying technology behind CrystalBall is sophisticated and effective. It applies a generation method augmented by a retriever, namely RAG, for retrieving the most relevant CVEs concerning a given set of system information supplied by the user against a large dataset. This information will be stored in a relational database supporting semantic search, enabling the system to chain vulnerabilities with a high degree of accuracy. It is applied as a black box to the LLM-based system, where the latter generates attack graphs. This approach ensures the comprehensiveness and relevance of generated graphs to the context in which they are applied for security purposes.
Rigorously, CrystalBall’s performance has been tested and compared against other methods. It has been shown that research into LLMs, especially GPT-4, increased the efficiency and accuracy of generating attack graphs. For instance, it processed threat reports and then generated attack graphs to a high degree of accuracy, covering 95% of relevant vulnerabilities and chaining them into coherent attack paths. Compared with other models, GPT-4 performed best on detail and cross-device vulnerability chaining, generating the most contextually relevant and accurate graphs. This solves a major deficiency of past techniques that often missed important contextual links between vulnerabilities.
When using large language models for cybersecurity—attack graph generation, these results are a big deal. On the other hand, CrystalBall improves the efficiency of attack graph generation and the accuracy and real-time relevance of the graphs generated. The important point is that while LLMs perform quite well in most scenarios, this approach still has limitations. Lacking domain-specific expertise, LLMs sometimes generate graphs that may further need refining or validation by a human expert. Moreover, there is an ethical concern while developing machine learning models for cybersecurity tasks because of the possibility of misuse.
In conclusion, this study concludes that the research provides a strong solution for the modern cybersecurity challenges. Further, the CrystalBall system enables the power of big Language Models like GPT-4 by providing a dynamic, scalable, and highly accurate method of generating the attack graphs. It is one of the approaches to overcome the shortcomings of previous methods in this area of research and keep up with the fast pace of change in the landscape of vulnerabilities and threats. Yet, many challenges remain open, but the potential benefits of this line of work render it a promising direction for further research and application in cybersecurity.
Check out the Paper. All credit for this research goes to the researchers of this project. Also, don’t forget to follow us on Twitter and join our Telegram Channel and LinkedIn Group. If you like our work, you will love our newsletter..
Don’t Forget to join our 48k+ ML SubReddit
Find Upcoming AI Webinars here
The post Researchers from UCI and Cisco Propose ‘CrystalBall’: A Novel AI Method for Automated Attack Graph Generation Using Retriever-Augmented Large Language Models appeared first on MarkTechPost.
Source: Read MoreÂ