Threat actors are using a new attack technique that allows them to evade detection and gain full code execution of Microsoft Management Console using specially crafted management saved console (MSC) files.
Elastic Security Labs researchers uncovered the new technique after a sample was uploaded to VirusTotal on June 6 – and it has yet to trigger static detections by antivirus tools on the site. The researchers are calling the new infection technique GrimResource.
GrimResource Attack Uses Old XSS Flaw
GrimResource is a “a novel, in-the-wild code execution technique leveraging specially crafted MSC files,†the researchers wrote. “GrimResource allows attackers to execute arbitrary code in Microsoft Management Console (mmc.exe) with minimal security warnings, ideal for gaining initial access and evading defenses.â€
The key to the attack technique is an old XSS flaw present in the apds.dll library. “By adding a reference to the vulnerable APDS resource in the appropriate StringTable section of a crafted MSC file, attackers can execute arbitrary javascript in the context of mmc.exe,†they said. Attackers can combine the technique with DotNetToJScript to gain arbitrary code execution.
The sample begins with a TransformNode obfuscation technique, which was recently reported by open source tool developer Philippe Lagadec in unrelated macro samples. The obfuscation technique helps evade ActiveX security warnings and leads to an obfuscated embedded VBScript, which sets the target payload in a series of environment variables before leveraging the DotNetToJs technique to execute an embedded .NET loader. The researchers named that component PASTALOADER.
PASTALOADER retrieves the payload from environment variables set by the VBScript and “spawns a new instance of dllhost.exe and injects the payload into it. This is done in a deliberately stealthy manner using the DirtyCLR technique, function unhooking, and indirect syscalls. In this sample, the final payload is Cobalt Strike.â€
Using the DotNetToJScript technique triggers another detection looking for RWX memory allocation from .NET on behalf of a Windows Script Host (WSH) script engine. The researchers created a rule in Elastic’s Event Query Language (EQL) to detect execution via the .NET loader.
GrimResource Detection Rules Provided
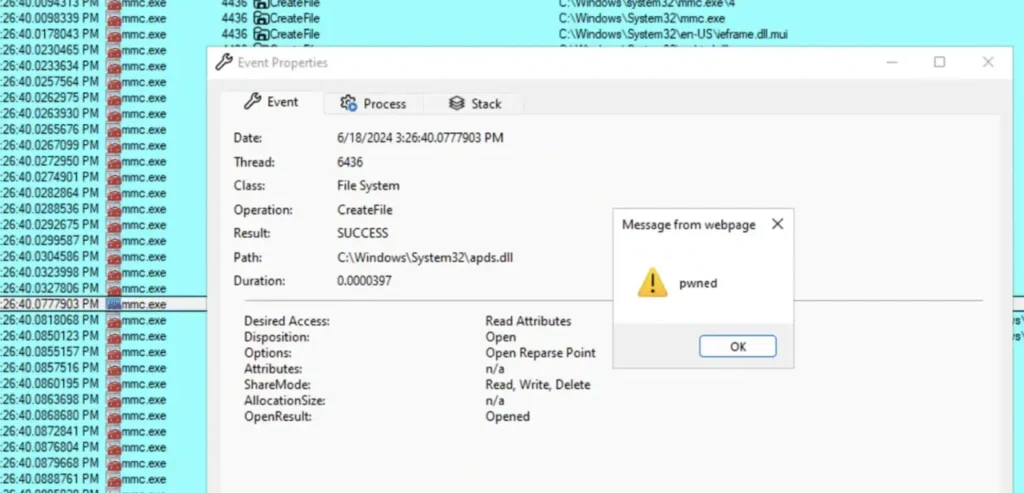
Those detections can be bypassed with stealthier methods, the researchers noted: Using apds.dll to execute Jscript via XSS, which can create detectable artifacts in the mmc.exe Procmon output as a CreateFile operation (apds.dll is not loaded as a library), and the creation of a temporary HTML file in the INetCache folder, named redirect[*] as a result of the APDS XSS redirection.
In addition to EQL rules, the researchers also provided a YARA detection rule:
GrimResource YARA detection rule (source: Elastic Security Labs)“Defenders should leverage our detection guidance to protect themselves and their customers from this technique before it proliferates into commodity threat groups,†the researchers warned.
Source: Read More