Two Rhode Island men pleaded guilty to hacking into a confidential federal law enforcement database and using the sensitive information to threaten and extort a victim.
Sagar Steven Singh, 20, and Nicholas Ceraolo, 26, were members of a hacking group called “ViLe†that collected victims’ personal data to harass, threaten or extort them in a practice known as “doxxing,†prosecutors said. Victims could pay to have their information removed from or kept off ViLe’s public website.
Breach and Abuse of Federal Law Enforcement Portal
According to the press release, on May 7, 2022, Singh used a stolen password belonging to a police officer to access a non-public, password-protected federal law enforcement portal. The portal, maintained by the U.S. Drug Enforcement Administration (DEA), holds detailed records on narcotics and currency seizures as well as law enforcement intelligence reports with respective state and local agencies.
Source:archive.orgThe next day, Singh told Ceraolo in an online chat that he shouldn’t have accessed the portal and was “no gov official.†Ceraolo then shared the stolen login credentials with others in the ViLe hacking group.
Shortly after, Singh used the database to obtain personal information on an individual. He messaged the victim, referred to in court documents as Victim-1, threatening to harm their family if they did not provide login credentials to their Instagram accounts.
To prove he had access to sensitive information, Singh included Victim-1’s Social Security number, driver’s license number and home address. He told Victim-1 that through the database portal, “i can request information on anyone in the US doesn’t matter who, nobody is safe.†Singh instructed Victim-1 to sell access to the Instagram accounts and give him the money. His messages implied he would use the information to harm Victim-1’s parents if demands were not met.
Source: dea.govWhile the court documents focus on the case of Victim-1, the duo also threatened other individuals whose information they had access to for financial gains. According to an earlier report from Vice, the portal that was used by the duo is the EPIC(El Paso Intelligence Center) Portal.
Guilty Pleas Over Actions
Singh and Ceraolo were charged in March 2023 with computer intrusion conspiracy and aggravated identity theft. Singh pleaded guilty to both counts on June 17, while Ceraolo had done so May 30, the U.S. Attorney’s Office in the Eastern District of New York announced.
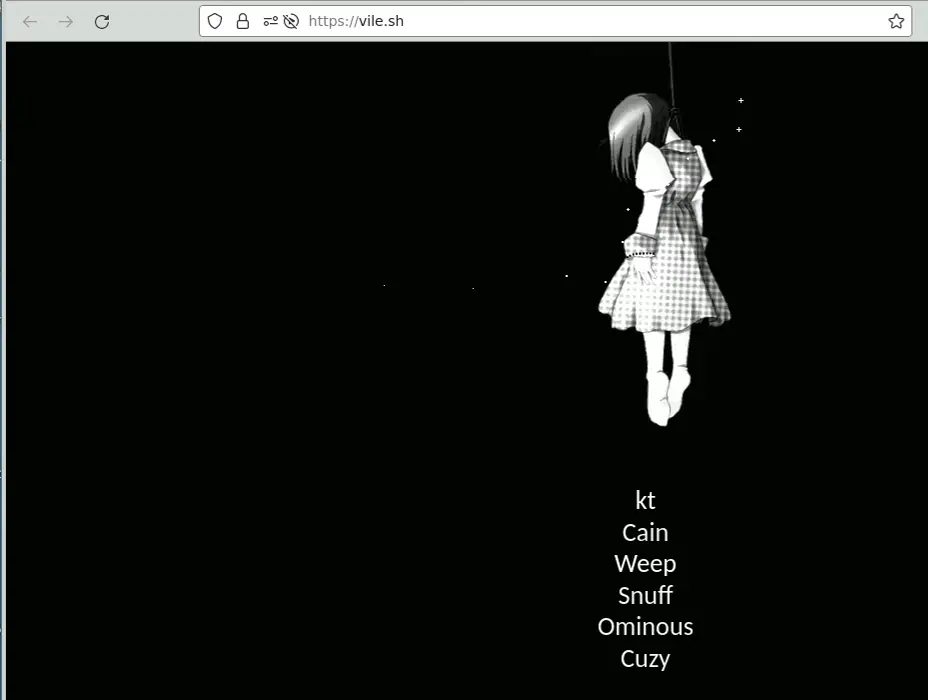
U.S. Attorney Breon Peace condemned the men’s actions as “ViLe,†a reference to the hacking group’s disturbing logo depicting a hanging girl. He stated, “They hacked into a law enforcement database and had access to sensitive personal information, then threatened to harm a victim’s family and publicly release that information unless the defendants were ultimately paid money. Our Office is relentless in protecting victims from having their sensitive information stolen and used to extort them by cybercriminals.â€
He thanked the HSI’s El Dorado Task Force, the Federal Bureau of Investigation and the New York Police Department for assistance in the case.
HSI New York Special Agent in Charge Ivan J. Arvelo stated, “The defendants, along with their co-conspirators, exploited vulnerabilities within government databases for their own personal gain. These guilty pleas send a strong message to those that would seek illicit access to protected computer systems.”
He added, “HSI New York’s El Dorado Task Force will continue to work with law enforcement partners to uncover evidence until every member of the ViLe group and similar criminal organizations are brought to justice.â€
The defendants face two to seven years in federal prison upon sentencing for the case in charges related to conspiring to commit computer intrusion and aggravated identify theft.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
Source: Read More