Cybersecurity researchers are tracking a novel Linux malware campaign that makes use of Discord emojis for command and control (C2) communication with attackers.
The campaign’s unusual combination of Linux malware and phishing lures suggests an attack aimed at Linux desktop users, the researchers from Volexity said.
“Volexity assesses it is highly likely this campaign, and the malware used, is targeted specifically towards government entities in India, who use a custom Linux distribution named BOSS as their daily desktop,†they wrote.
Threat Actor ‘UTA0137’ Linked to Campaign
Volexity researchers connected the campaign to a Pakistan-based threat actor they call UTA0137.
The researchers said they have “high confidence that UTA0137 has espionage-related objectives and a remit to target government entities in India. Based on Volexity’s analysis, UTA0137’s campaigns appear to have been successful.â€
The researchers say they have “moderate confidence†that UTA0137 is a Pakistan-based threat actor because of the group’s targets and a few other reasons:
The Pakistani time zone was hardcoded in one malware sample.
There are weak infrastructure links to SideCopy, a known Pakistan-based threat actor.
The Punjabi language was used in the malware.
The malware used by the threat group uses a modified version of the discord-c2 GitHub project for its Discord command and control (C2) communication. The malware, dubbed DISGOMOJI by the researchers, is written in Golang and compiled for Linux systems.
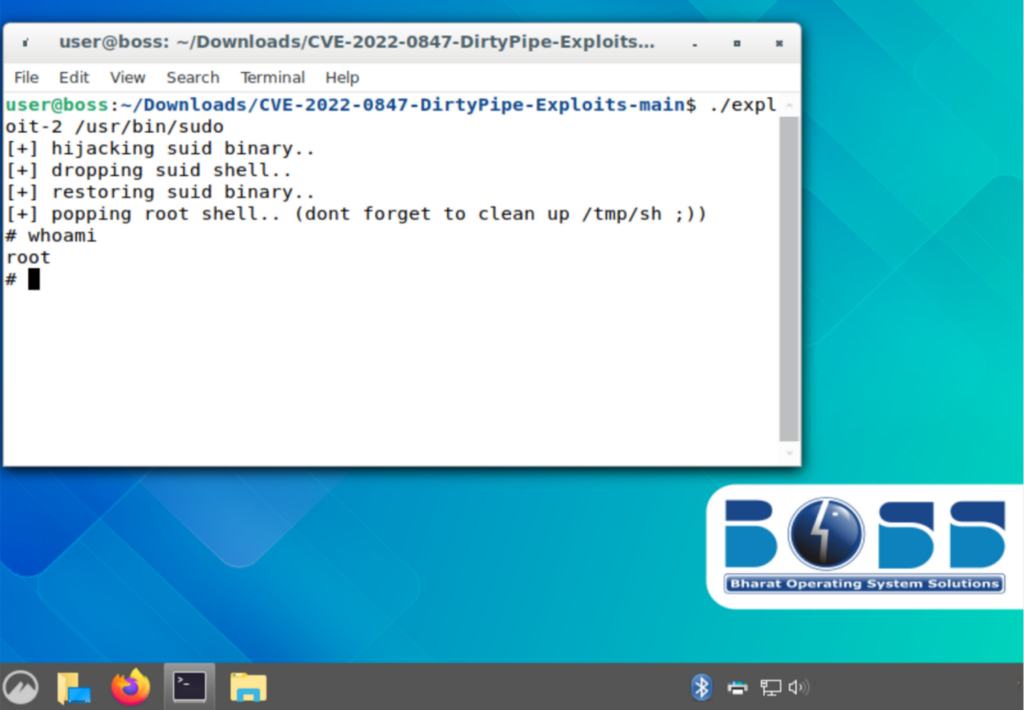
The threat actors also use the DirtyPipe (CVE-2022-0847) privilege escalation exploit against “BOSS 9†systems, which remain vulnerable to the exploit.
Attack Starts With DSOP PDF
The malware is delivered via a DSOP.pdf lure, which claims to be a beneficiary document of India’s Defence Service Officer Provident Fund (screenshot below).
The DSOP lure that downloads the malwareThe malware then downloads the next-stage payload, named vmcoreinfo, from a remote server, clawsindia[.]in. The payload is an instance of the DISGOMOJI malware and is dropped in a hidden folder named .x86_64-linux-gnu in the user’s home directory.
DISGOMOJI, a UPX-packed ELF written in Golang, uses Discord for C2. “An authentication token and server ID are hardcoded inside the ELF, which are used to access the Discord server,â€Â they wrote. “The malware creates a dedicated channel for itself in the Discord server, meaning each channel in the server represents an individual victim. The attacker can then interact with every victim individually using these channels.â€
On startup, DISGOMOJI sends a check-in message in the channel that contains information like the internal IP, the user name, host name, OS and current working directory. The malware can survive reboots through the addition of a @reboot entry to the crontab, and it also downloads a script named uevent_seqnum.sh to copy files from any attached USB devices.
Discord Emojis Used for C2 Communication
C2 communication uses an emoji-based protocol, “where the attacker sends commands to the malware by sending emojis to the command channel, with additional parameters following the emoji where applicable.â€
A Clock emoji in the command message lets the attacker know a command is being processed, while a Check Mark emoji confirms that the command was executed. The researchers summarized the emoji commands in a table:
The Discord emojis used to communicate with attackers (source: Volexity)Post-exploitation activities include use of the Zenity utility to display malicious dialog boxes to socially engineer users into giving up their passwords. Open source tools such as Nmap, Chisel and Ligolo are also used, and the DirtyPipe exploit suggests increasing sophistication of the atacker’s methods, the researchers said.
Indicators of compromise (IoCs) can be downloaded from the Volexity GitHub page:
YARA rules
Single value indicators
Source: Read More