Data breaches affecting customers of the cloud storage provider Snowflake have hit about 165 organizations so far, according to a Google Mandiant report published today.
While initial claims linked the Snowflake breach to the cloud provider’s own environment, Mandiant said its investigation backs up Snowflake’s assertion that the breaches came from compromised customer credentials, many of which did not have multi-factor authentication enabled.
Some of the high-profile organizations hit in the attack have included Ticketmaster, Advance Auto Parts, Santander, and more.
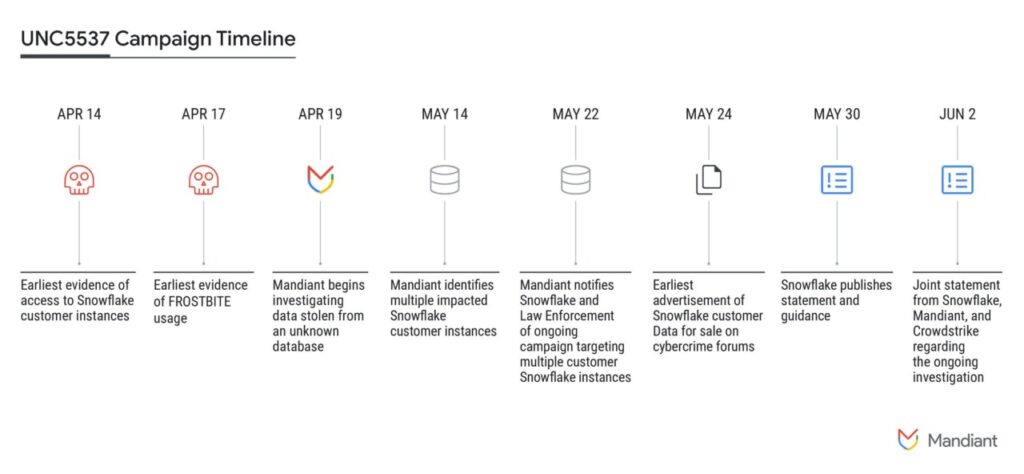
Snowflake Breach Discovered in April
Mandiant is attributing the breach to UNC5537, “a financially motivated threat actor suspected to have stolen a significant volume of records from Snowflake customer environments. UNC5537 is systematically compromising Snowflake customer instances using stolen customer credentials, advertising victim data for sale on cybercrime forums, and attempting to extort many of the victims.â€
The threat group is based in North America, with an additional member in Turkey, Mandiant said.
“Mandiant’s investigation has not found any evidence to suggest that unauthorized access to Snowflake customer accounts stemmed from a breach of Snowflake’s enterprise environment,†Mandiant researchers wrote. “Instead, every incident Mandiant responded to associated with this campaign was traced back to compromised customer credentials.â€
Mandiant first saw evidence of the Snowflake data breach campaign in April, when the company “received threat intelligence on database records that were subsequently determined to have originated from a victim’s Snowflake instance.â€
In the subsequent investigation, Mandiant found that the organization’s Snowflake instance had been compromised by a threat actor using credentials previously stolen with infostealer malware. “The threat actor used these stolen credentials to access the customer’s Snowflake instance and ultimately exfiltrate valuable data,†Mandiant said. At the time of the compromise, the account did not have multi-factor authentication (MFA) enabled.
Hackers Used Credentials from Infostealer Campaigns
Mandiant said its investigations so far into hacked Snowflake customers found that UNC5537 was able to obtain access via stolen customer credentials that were “primarily obtained from multiple infostealer malware campaigns that infected non-Snowflake owned systems.â€
Some of those infostealer infections date back as far as 2020, using infostealer malware variants such as VIDAR, RISEPRO, REDLINE, RACOON STEALER, LUMMA and METASTEALER.
Initial access to Snowflake customer instances often occurred via the native web-based UI (SnowFlake UI AKA SnowSight) or command-line interface (CLI) tool (SnowSQL) running on Windows Server 2022. Mandiant identified additional access leveraging an attacker-named utility, “rapeflake,†which Mandiant is tracking as FROSTBITE.
Snowflake breach attack path (source: Mandiant)In addition to a lack of MFA, Mandiant said some affected accounts had not updated credentials since they had been stolen, even after significant time had elapsed. The affected Snowflake instances also did not use network allow lists to only allow access from trusted locations.
A list of suspect IP addresses can be found on VirusTotal, and Snowflake has also published detailed security information, including indicators of compromise (IoCs).
Source: Read More