While Microsoft’s forthcoming Recall feature has already sparked security and privacy concerns, the tech giant attempted to downplay those reactions by stating that collected data would remain on the user’s device.
Despite this reassurance, concerns remain, as researchers – including the developer of a new tool dubbed “TotalRecall” – have observed various inherent vulnerabilities in the local database maintained by Recall, lending credibility to critics of Microsoft’s implementation of the AI tool.
TotalRecall Tool Demonstrates Recall’s Inherent Vulnerabilities
Recall is a new Windows AI tool planned for Copilot+ PCs that captures screenshots from user devices every five seconds, then storing the data in a local database. The tool’s announcement, however, led many to fear that this process would make sensitive information on devices susceptible to unauthorized access.
TotalRecall, a new tool developed by Alex Hagenah and named after the 1990 sci-fi film, highlights the potential compromise of this stored information. Hagenah states that the the local database is unencrypted and stores data in plain text format. The researcher likened Recall to spyware, calling it a “Trojan 2.0.”
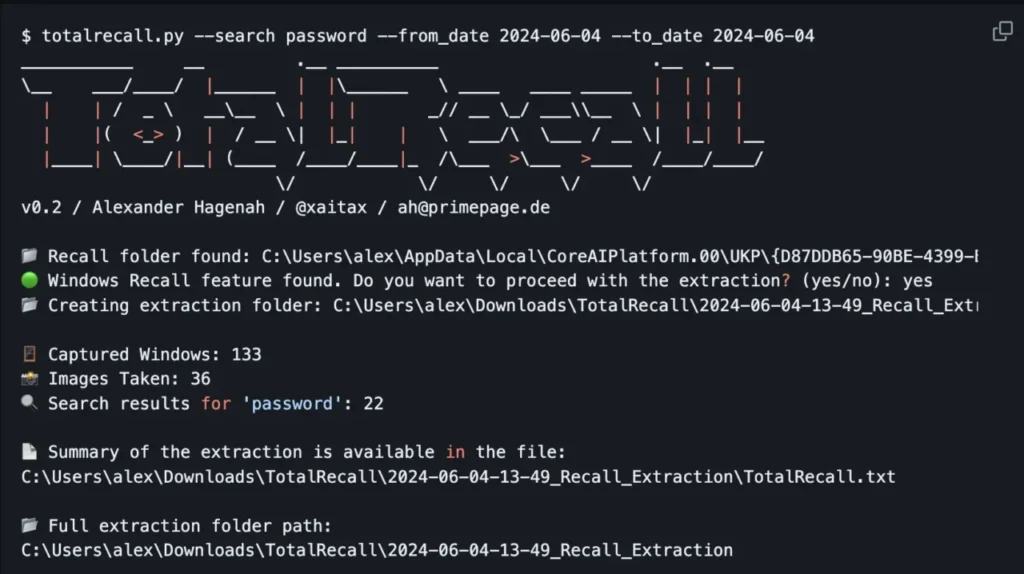
TotalRecall was designed to extract and display all the information stored in the Recall database, pulling out screenshots, text data, and other sensitive information, highlighting the potential for abuse by criminal hackers or domestic abusers who may gain physical access to a device. Hagenah’s concerns are echoed by others in the cybersecurity community, who have also compared Recall to spyware or stalkerware.
Recall captures screenshots of everything displayed on a user’s desktop, including messages from encrypted apps like Signal and WhatsApp, websites visited, and all text shown on the PC. TotalRecall can locate and copy the Recall database, parse its data, and generate summaries of the captured information, with features for date range filtering and term searches.
Hagenah stated that by releasing the tool on GitHub, he aims to push Microsoft to fully address these security issues before Recall’s launch on June 18.
Microsoft Recall Privacy and Security Concerns
Cybersecurity researcher Kevin Beaumont has also developed a website for searching Recall databases, though he has withheld its release to give Microsoft time to make changes.
Microsoft‘s privacy documentation for Recall mentions the ability to disable screenshot saving, pause Recall on the system, filter out applications, and delete data. Nonetheless, the company acknowledges that Recall does not moderate the captured content, which could include sensitive information like passwords, financial details and more.
The risks extend beyond individual users, as employees under “bring your own device” policies could leave with significant amounts of company data saved on their laptops. The UK’s data protection regulator has requested more information from Microsoft regarding Recall and its privacy implications.
Amid criticism over recent hacks affecting US government data, Microsoft CEO Satya Nadella has emphasized its need to prioritize security. However, the issues surrounding Recall demonstrate that security concerns were not given sufficient attention, and necessitate inspection of its data collection practices before its official release.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
Source: Read More