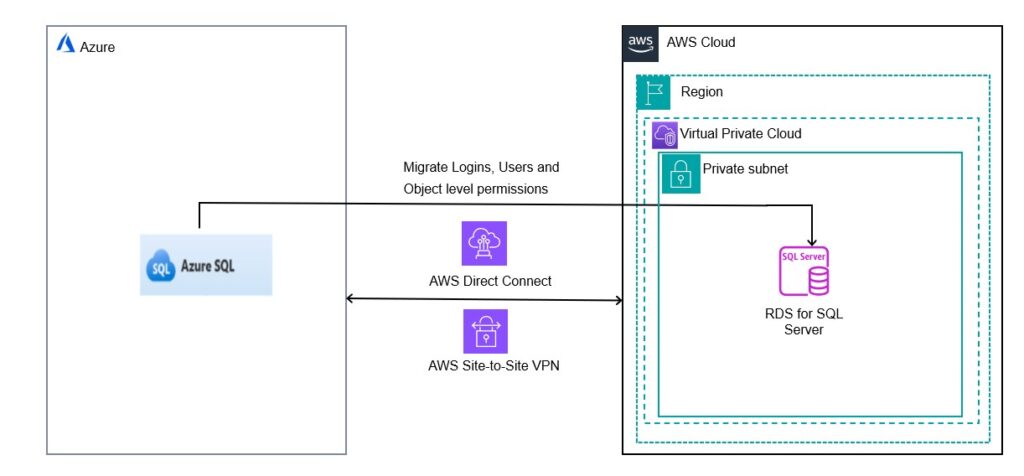
In this post, we demonstrate how to migrate SQL logins, database roles, users, and object-level permissions from Azure SQL Database to Amazon Relational Database Service (Amazon RDS) for SQL Server using T-SQL.
Within SQL Server, a SQL login acts as a security principal, allowing a user or application to connect to a SQL Server instance. It serves as a mechanism to manage access, permissions, user privileges, and monitor database activities. Migrating SQL logins is crucial during a database migration because they contain authentication information, access rights, and permissions essential for users and applications to connect and interact with databases. While native backup and restore operations are often sufficient for login migration, certain scenarios require additional steps to ensure a seamless migration, especially when migrating from Azure SQL Database and using data transfer methods SmartbulkCopy, AWS Database Migration Service (AWS DMS), or BCP to migrate data and schema separately
SQL Server security components overview
In SQL Server, a SQL login is a security principal that allows a user or application to connect to an instance. These SQL logins are associated with user accounts for the purpose of authentication. Authentication in SQL Server involves three key elements:
Principals – These are entities capable of requesting resources within SQL Server. Principal access levels are contingent on their scope. We can categorize principles into two types based on their scope: server-level principals and database-level principals.
Securables – These are server or database objects to which authentication can be granted, such as tables or endpoints. Securables are further categorized based on their scope: server scoped, database scoped, and schema scoped.
Permissions – Permissions define control of securables to the principal. Principals can run specific operations on securables based on the permissions assigned. At the server level, permissions are managed through logins and server roles, whereas at the database level, permissions are regulated using database users and roles.
The following table illustrates the SQL Server security administration differences between Azure SQL Database and Amazon RDS for SQL Server.
Activity
Amazon RDS for SQL Server
Azure SQL Database
Where you manage server-level security
Security folder in SQL Server Management Studio’s Object Explorer
master database and through the Azure portal
Windows Authentication
AWS Managed Microsoft AD
Azure Active Directory identities
Server-level security role for creating logins
securityadmin fixed server role
loginmanager database role in the master database
Commands for managing logins
CREATE LOGIN, ALTER LOGIN, DROP LOGIN
CREATE LOGIN, ALTER LOGIN, DROP LOGIN (there are some parameter limitations and you must be connected to the master database)
View that shows all logins
sys.server_principals
sys.sql_logins (you must be connected to the master database)
Server-level role for creating databases
dbcreator fixed database role
dbmanager database role in the master database
Solution overview
In scenarios where logins and user permissions are not migrated as part of the database migration process, such as when using SmartBulkCopy, AWS DMS, or BCP, we utilize the built-in generate script utility and T-SQL dynamic scripts to create the logins, roles, users, and object-level permissions for each database.
The following diagram illustrates the high-level architecture of migrating logins and database users from Azure SQL Database to Amazon RDS for SQL Server.
The following steps are involved to migrate the SQL logins and their dependent security components:
Migrate logins and validate the existence of logins and the users between Azure SQL Database to Amazon RDS for SQL Server.
Migrate server roles and server permissions and validate the permissions.
Migrate users and database roles and validate the users and the roles.
Migrate object-level permissions and validate the permissions.
Prerequisites
To get started, you need to have the following:
An Azure SQL database as a source
An RDS for SQL Server DB instance (Single-AZ or Multi-AZ) as a target
Connectivity between Azure SQL Database to Amazon RDS for SQL Server
A target RDS for SQL Server database with required user-defined objects (tables, views, functions, and stored procedures) and a user with the db_owner fixed database role to create objects in the SQL Server database
An Azure login with minimum permissions to master to fetch login and user info like loginmanager, and more roles to make sure that the primary login name of Azure SQL Database is different from RDS for SQL Server
Migrate logins
You can access Azure SQL Database using a SQL Server authentication account, Microsoft Entra server principals, or a managed identity. Identify the Microsoft Entra server principals and managed identity by fetching the login information from sys.logins and migrate them manually. Ensure to create EXTERNAL_USERS as db_owner in Amazon RDS for SQL Server. Due to Amazon RDS for SQL Server’s permission restrictions, you cannot grant sysadmin privileges to users at the target
To migrate SQL logins from Azure SQL Database to Amazon RDS for SQL Server, you can script out the create login scripts with a hashed password and SID. However, when using Azure SQL Database as the source, the generated SID and hashed password may cause conversion issues, and certain functions like SUSER_SID() are not supported.
In this section, we explain how to generate the create a login script from a source SQL Server instance and migrate it to the target RDS for SQL Server instance.
Connect to your source Azure SQL from SQL Server Manager Studio (SSMS) with the primary user or a user that has security admin fixed role permissions to script logins.
In the SSMS query editor, choose the Results to Grid (press Ctrl+D) option.
Run the following script from the new query window to generate the create logins script:
The output of the query provides the logins creation script.
Copy the logins creation script and run it using the Amazon RDS primary user or a login with the “Alter any login†server-level securable that is part of a processadmin and setupadmin fixed server roles in the RDS for SQL Server instance.
Check for any errors and fix them accordingly.
Validate the number of logins created on the Azure SQL database and RDS for SQL Server database. To test the login if working properly, connect to RDS for SQL Server with any of the logins migrated with the password used to connect at the Azure SQL Database end.
After the successful migration of logins, you can continue with the server role membership migration.
You should be responsible and cautious while copying the output and pasting it at the target database because it contains sensitive data.
Migrate server roles and server permissions
In Amazon RDS for SQL Server, you don’t have superuser or sysadmin privileges. The primary user is the highest privilege user. Users cannot be created in the master database. User creation happens at the database level. The primary user is specified during RDS instance creation with a user name and password. The primary user has the maximum privileges allowed within RDS, but not full sysadmin privileges. Only setupadmin and processadmin fixed server roles can be granted to logins by the primary user. Refer to the fixed server roles in the RDS for SQL Server instance for more details.
In Azure SQL Database, you can use the built-in server-level roles to manage permissions at the logical server level rather than granting permissions directly at that level. Refer to Azure SQL Database server roles for permission management for more details.
The key steps to migrate server-level roles and permissions from Azure SQL Database to an RDS for SQL Server instance are as follows:
For each login, identify the server-level roles they are a member of using the following script:
After the logins are created in Amazon RDS for SQL Server, you can recreate the server roles for setupadmin and processadmin on the RDS instance, because other roles are not possible. Refer Azure SQL Database server roles for permission management and Microsoft Entra server principals for AD users. You can add the login as a member to the processadmin and setupadmin fixed server roles on RDS using the following statements:
Refer to the permissions for the processadmin and setupadmin fixed server roles before manually adding logins to these roles on Amazon RDS.
Migrate users and database roles
To migrate your users and database roles, complete the following steps:
Connect to your source Azure SQL from SSMS with the primary user or user that has security admin fixed role permissions.
Choose (right-click) the database and choose Generate Scripts.
Choose Next.
Select Select specific database objects, then select Users.
Choose Next.
Select Save as script file.
Enter a location to save the file.
Choose Next.
A script will be generated in the provided location.
Run the copied script on the target RDS for SQL Server database.
Validate the number of users, roles, and permissions on the Azure SQL database and match them with the RDS for SQL Server database by querying and joining the system tables sys.database_principals, database_role_members, database_role_members, and sys.database_permissions.
Migrate object-level permissions
Complete the following steps to migrate object-level permissions:
Connect to your source Azure SQL from SSMS with the primary user or user that has security admin fixed role permissions to script logins.
In the SSMS query editor, choose the Results to Grid (press Ctrl+D) option.
Run the following script from the new query window to generate the object-level permissions create script:
Run the created object-level permissions script on the target RDS for SQL Server database and validate.
Connect to the target Amazon RDS for SQL Server using SSMS and copy the output scripts generated in Step 4.
Validate the script output for any errors.
Clean up
To avoid future charges, remove all of the components you created while testing this use case by completing the following steps:
On the Amazon RDS console, choose Databases in the navigation pane.
Select the databases you set up and on the Actions menu, choose Delete.
Enter delete me to confirm deletion.
For more information about deleting an instance, refer to Deleting a DB instance.
Conclusion
In this post, we described how to migrate logins, database roles, users, and object-level permissions to Amazon RDS for SQL Server using T-SQL. If you have any questions or suggestions, leave a comment.
About the Authors
InduTeja Aligeti is a Senior Lead Database Consultant at AWS. She has over 18 years of experience working with Microsoft technologies with a specialization in SQL Server. She focuses on helping customers build highly available, cost-effective database solutions and migrate their large-scale SQL Server databases to AWS.
Jitendra Kumar is a Lead Database Migration Consultant with AWS Professional Services. He helps customers migrate and modernize workloads in the AWS Cloud, with a special focus on modern application architectures and development best practices.
Ramesh Babu Donti is a Lead Database Consultant with AWS Professional Services based out of Hyderabad, India. He focuses on helping customers build highly available, cost-effective database solutions and migrate their large-scale databases to AWS.
Source: Read More