Amazon Relational Database Service (Amazon RDS) is a fully managed database service provided by AWS, enabling you to set up, operate, and scale relational databases in the cloud. Although Amazon RDS offers seamless database management, it’s critical to stay informed about pending maintenance actions that might impact database availability. Amazon RDS regularly undergoes maintenance activities to make sure that the health and performance of your databases remains intact. These maintenance actions can range from security updates to version upgrades. These crucial activities are normally planned during maintenance windows, but they can potentially interrupt database availability during implementation. Therefore, staying informed about pending maintenance actions becomes prudent for database administrators and AWS users to take proactive measures and minimize any impact on operations. However, AWS does not provide any mechanism to proactively send notifications for pending maintenance actions of your RDS instances.
In this post, we explore how to proactively set up notifications for Amazon RDS pending maintenance actions using Amazon Simple Notification Service (Amazon SNS), Amazon EventBridge, and AWS Lambda. This solution enables you to automate a push-style notification on upcoming maintenance, rather than pulling the notification from the API or AWS Management Console directly.
Solution overview
In a production environment, effectively managing and staying ahead of pending maintenance actions is crucial for ensuring the smooth operation of your RDS instances. In this section, we discuss the architecture to set up a custom solution for notifications regarding Amazon RDS pending maintenance actions.
In this solution, we provide a customized Lambda function that gets invoked through EventBridge Scheduler and pushes messages regarding Amazon RDS pending maintenance actions through a user-configured SNS topic. We demonstrate how to identify pending maintenance actions, set up a custom Lambda function, and configure EventBridge Scheduler and Amazon SNS to get email notifications regarding these pending maintenance actions. You can use this solution to plan ahead and take care of Amazon RDS pending maintenance actions, all the while keeping availability of RDS instances in line with your business requirements.
The following are the high-level steps to set up the solution:
Check the RDS instance for any pending maintenance actions.
Create an SNS topic that will be invoked by the Lambda function and send email notifications.
Create a Lambda function, which will be invoked by the EventBridge schedule.
Create an EventBridge schedule to invoke the Lambda function.
Prerequisites
In order to set up notifications for Amazon RDS pending maintenance actions, you need to:
Create an RDS instance on which the pending maintenance will be captured and sent as an email notification.
Set up an Amazon SNS Topic which will be triggered by Lambda function and send Email Notifications.
Check the RDS instance for any pending maintenance actions
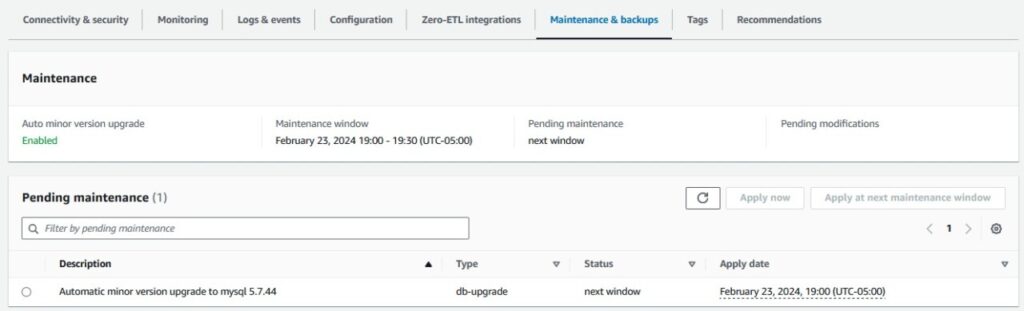
To check for any Amazon RDS pending maintenance actions, you can use the AWS Command Line Interface (AWS CLI) or the Amazon RDS console. For instructions, refer to describe-pending-maintenance-actions or Viewing pending maintenance, respectively. The following image shows the db-upgrade action type on the Pending maintenance tab on the RDS instance details page.
For this post, we find a pending maintenance action for our RDS instance and implement the solution to capture this info. If you don’t see any pending maintenance actions at the time of setting up this solution, you can still proceed with the rest of the configuration because it will automatically activate when the instance eventually has a scheduled pending action.
Create an SNS topic
The next step is to create an SNS topic that will be invoked by the Lambda function to send email notifications. For instructions, refer to Creating an Amazon SNS topic.
Create a Lambda function
Use the following Python script to configure the Lambda function. Replace the sns_topic_arn value with your SNS topic ARN and region with the same AWS Region in which you are deploying your solution:
The following screenshot shows the Python code on the Lambda console.
The Lambda function creation process gives you the options Create a new role with basic Lambda permissions or Use an existing role. This AWS Identity and Access Management (IAM) role requires specific permissions in its policy.
To see the IAM role that is attached to this Lambda function, navigate to the Configuration tab of the function details page and choose Permissions in the left pane. The role name is displayed under Execution role, as shown in the following screenshot.
Modify the IAM role to include Amazon RDS describe maintenance and Amazon SNS publish permissions. The following is a sample IAM policy:
You can manually invoke the Lambda function by choosing Test, as shown in the following screenshot.
If any of your RDS databases have a pending action, you will receive an email, as shown in the following screenshot.
If you experience a timeout error during the Lambda function test run, you can do the following:
On the function details page, choose the Configuration tab.
Choose General configuration in the left pane.
Choose Edit.
Increase the timeout value (the default timeout is 3 seconds).
Choose Save.
The following screenshot shows the timeout configuration on the Lambda console.
Create an EventBridge schedule
In this section, you create a schedule using EventBridge Scheduler to invoke the Lambda function. Complete the following steps:
On the EventBridge console, choose Schedules in the navigation pane.
Choose Create schedule
For Schedule name, enter a name.
For Schedule group, leave as default.
For Occurrence, select Reoccurring schedule.
For Time zone, choose your preferred time zone.
For Schedule type, select Cron-based schedule.
For Cron expression, specify how often you would like to receive notifications (for this post, we configure the schedule for every day at 5:02 PM EST) (02:17:*:*:?:*).
For Flexible time window, choose OFF.
Choose Next.
For Target API, select AWS Lambda Invoke.
For Lambda function, choose the name of the Lambda function you created.
Choose Next.
In the Settings section, under Permissions, Execution role, choose Create new role for this schedule.
Choose Next.
Review your configurations and choose Create schedule.
Now your Lambda function will be activated according to your cron expression. If it finds any pending actions, it will send an email notifying you. This solution was tested with all of the dependent services within the same Region. This solution can work with any Amazon RDS and Amazon Aurora engine. The Lambda function code can be customized for your specific business needs.
Clean up
To avoid ongoing charges, delete the resources you created with this solution:
Delete the RDS instance.
Delete the SNS topic.
Delete the EventBridge schedule.
Delete the IAM role.
Delete the Lambda function.
Conclusion
In this post, we presented a solution that uses Amazon SNS, EventBridge, and Lambda to set up custom notifications regarding Amazon RDS pending maintenance actions. By using this solution, you can automate the process of receiving timely notifications. If you have any questions or concerns, leave them in the comments section.
About the Authors
Abdul Sarker is a Cloud Support Engineer working with AWS for 2.5 years. Abdul is also a subject matter expert in AWS DMS. With a focus on providing excellent customer experiences in the AWS Cloud, he works with external customers to handle a variety of scenarios, such as troubleshooting Amazon RDS infrastructure, assisting with AWS DMS migrations, authoring and improving internal documentations, and playing a pivotal role in the improvement of internal processes.
Nirupam Datta is a Senior Cloud Support DBE at AWS. He has been with AWS for over 4 years. With over 12 years of experience in database engineering and infra-architecture, Nirupam is also a subject matter expert in the Amazon RDS core systems and Amazon RDS for SQL Server. He provides technical assistance to customers, guiding them to migrate, optimize, and navigate their journey in the AWS Cloud.
Vlad Podomatskiy is a Security and Database Engineer in AWS Support. With over 9 years of overall technical experience, he provides technical assistance to customers on database monitoring, AWS migrations, encryption, and account security. He is always curious about IT security and is pursuing a master’s in cybersecurity.
Source: Read More