In SaaS security conversations, “misconfiguration” and “vulnerability” are often used interchangeably. But they’re not the same thing. And misunderstanding that…
Security
Cybersecurity researchers have disclosed a high-severity security flaw in the artificial intelligence (AI)-powered code editor Cursor that could result in…
Google has released security updates to address multiple security flaws in Android, including fixes for two Qualcomm bugs that were…
In episode 62 of The AI Fix, your hosts learn how AI models smash through CAPTCHA roadblocks like they’re made…
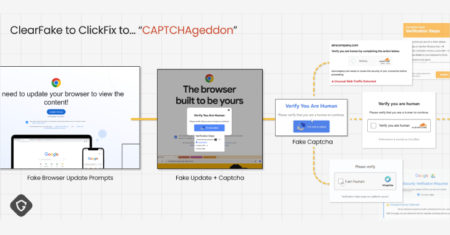
A combination of propagation methods, narrative sophistication, and evasion techniques enabled the social engineering tactic known as ClickFix to take…
CVE ID : CVE-2025-51534
Published : Aug. 4, 2025, 5:15 p.m. | 1 day, 6 hours ago
Description : A cross-site scripting (XSS) vulnerability in Austrian Archaeological Institute (AI) OpenAtlas v8.11.0 allows attackers to execute arbitrary web scripts or HTML via injecting a crafted payload into the Name field.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-51535
Published : Aug. 4, 2025, 5:15 p.m. | 1 day, 6 hours ago
Description : Austrian Archaeological Institute (AI) OpenAtlas v8.11.0 as discovered to contain a SQL injection vulnerability.
Severity: 9.1 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-51390
Published : Aug. 4, 2025, 6:15 p.m. | 1 day, 5 hours ago
Description : TOTOLINK N600R V4.3.0cu.7647_B20210106 was discovered to contain a command injection vulnerability via the pin parameter in the setWiFiWpsConfig function.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54119
Published : Aug. 5, 2025, 1:15 a.m. | 22 hours, 26 minutes ago
Description : ADOdb is a PHP database class library that provides abstractions for performing queries and managing databases. In versions 5.22.9 and below, improper escaping of a query parameter may allow an attacker to execute arbitrary SQL statements when the code using ADOdb connects to a sqlite3 database and calls the metaColumns(), metaForeignKeys() or metaIndexes() methods with a crafted table name. This is fixed in version 5.22.10. To workaround this issue, only pass controlled data to metaColumns(), metaForeignKeys() and metaIndexes() method’s $table parameter.
Severity: 10.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54135
Published : Aug. 5, 2025, 1:15 a.m. | 22 hours, 26 minutes ago
Description : Cursor is a code editor built for programming with AI. Cursor allows writing in-workspace files with no user approval in versions below 1.3.9, If the file is a dotfile, editing it requires approval but creating a new one doesn’t. Hence, if sensitive MCP files, such as the .cursor/mcp.json file don’t already exist in the workspace, an attacker can chain a indirect prompt injection vulnerability to hijack the context to write to the settings file and trigger RCE on the victim without user approval. This is fixed in version 1.3.9.
Severity: 8.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54802
Published : Aug. 5, 2025, 1:15 a.m. | 22 hours, 26 minutes ago
Description : pyLoad is the free and open-source Download Manager written in pure Python. In versions 0.5.0b3.dev89 and below, there is an opportunity for path traversal in pyLoad-ng CNL Blueprint via package parameter, allowing Arbitrary File Write which leads to Remote Code Execution (RCE). The addcrypted endpoint in pyload-ng suffers from an unsafe path construction vulnerability, allowing unauthenticated attackers to write arbitrary files outside the designated storage directory. This can be abused to overwrite critical system files, including cron jobs and systemd services, leading to privilege escalation and remote code execution as root. This issue is fixed in version 0.5.0b3.dev90.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54982
Published : Aug. 5, 2025, 6:15 a.m. | 17 hours, 26 minutes ago
Description : An improper verification of cryptographic signature in Zscaler’s SAML authentication mechanism on the server-side allowed an authentication abuse.
Severity: 9.6 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54948
Published : Aug. 5, 2025, 1:15 p.m. | 10 hours, 26 minutes ago
Description : A vulnerability in Trend Micro Apex One (on-premise) management console could allow a pre-authenticated remote attacker to upload malicious code and execute commands on affected installations.
Severity: 9.4 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54987
Published : Aug. 5, 2025, 1:15 p.m. | 10 hours, 26 minutes ago
Description : A vulnerability in Trend Micro Apex One (on-premise) management console could allow a pre-authenticated remote attacker to upload malicious code and execute commands on affected installations. This vulnerability is essentially the same as CVE-2025-54948 but targets a different CPU architecture.
Severity: 9.4 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-50706
Published : Aug. 5, 2025, 3:15 p.m. | 8 hours, 26 minutes ago
Description : An issue in thinkphp v.5.1 allows a remote attacker to execute arbitrary code via the routecheck function
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-50707
Published : Aug. 5, 2025, 3:15 p.m. | 8 hours, 26 minutes ago
Description : An issue in thinkphp3 v.3.2.5 allows a remote attacker to execute arbitrary code via the index.php component
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46658
Published : Aug. 5, 2025, 4:15 p.m. | 7 hours, 26 minutes ago
Description : An issue was discovered in ExonautWeb in 4C Strategies Exonaut 21.6. There are verbose error messages.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54253
Published : Aug. 5, 2025, 5:15 p.m. | 6 hours, 26 minutes ago
Description : Adobe Experience Manager versions 6.5.23 and earlier are affected by a Misconfiguration vulnerability that could result in arbitrary code execution. An attacker could leverage this vulnerability to bypass security mechanisms and execute code. Exploitation of this issue does not require user interaction and scope is changed.
Severity: 10.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54254
Published : Aug. 5, 2025, 5:15 p.m. | 6 hours, 26 minutes ago
Description : Adobe Experience Manager versions 6.5.23 and earlier are affected by an Improper Restriction of XML External Entity Reference (‘XXE’) vulnerability that could lead to arbitrary file system read. An attacker could exploit this vulnerability to access sensitive files on the local file system. Exploitation of this issue does not require user interaction.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2012-10024
Published : Aug. 5, 2025, 8:15 p.m. | 3 hours, 10 minutes ago
Description : XBMC version 11, including builds up to the 2012-11-04 nightly release, contains a path traversal vulnerability in its embedded HTTP server. When accessed via HTTP Basic Authentication, the server fails to properly sanitize URI input, allowing authenticated users to request files outside the intended document root. An attacker can exploit this flaw to read arbitrary files from the host filesystem, including sensitive configuration or credential files.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…