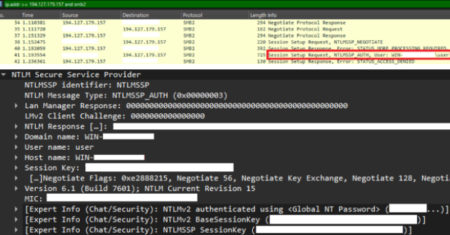
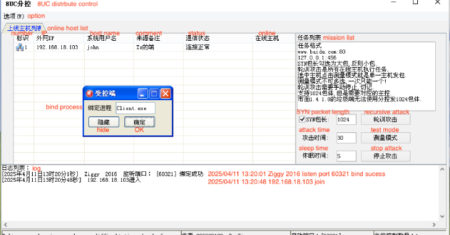
The Russian state-sponsored threat actor known as APT29 has been linked to an advanced phishing campaign that’s targeting diplomatic entities…
Security
Apple Zero-Days Under ‘Sophisticated Attack,’ but Details Lacking
dpa picture alliance / AlamyTwo Apple zero-day vulnerabilities were exploited in “extremely sophisticated attacks,” according to the technology giant, but it has provided little detail on the threats. …
Read more
Published Date:
Apr 18, 2025 (1 day, 17 hours ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-31201
CVE-2025-31200
CISA adds Microsoft and Apple vulnerabilities to KEV Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has added three newly exploited vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog, signaling active exploitation in the w …
Read more
Published Date:
Apr 18, 2025 (1 day, 16 hours ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-31201
CVE-2025-31200
CVE-2025-3608
CVE-2025-24054
Chinese hackers target Russian govt with upgraded RAT malware
Chinese-speaking IronHusky hackers are targeting Russian and Mongolian government organizations using upgraded MysterySnail remote access trojan (RAT) malware.
Security researchers at Kaspersky’s Glob …
Read more
Published Date:
Apr 18, 2025 (1 day, 16 hours ago)
Vulnerabilities has been mentioned in this article.
CVE-2021-40449
CVE-2017-11882
SonicWall SMA VPN devices targeted in attacks since January
A remote code execution vulnerability affecting SonicWall Secure Mobile Access (SMA) appliances has been under active exploitation since at least January 2025, according to cybersecurity company Arcti …
Read more
Published Date:
Apr 18, 2025 (1 day, 15 hours ago)
Vulnerabilities has been mentioned in this article.
CVE-2021-20035
CVE ID : CVE-2025-39587
Published : April 17, 2025, 4:15 p.m. | 2 days, 13 hours ago
Description : Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) vulnerability in Stylemix Cost Calculator Builder allows SQL Injection. This issue affects Cost Calculator Builder: from n/a through 3.2.65.
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3801
Published : April 19, 2025, 2:15 p.m. | 14 hours, 38 minutes ago
Description : A vulnerability was found in songquanpeng one-api up to 0.6.10. It has been classified as problematic. This affects an unknown part of the component System Setting Handler. The manipulation of the argument Homepage Content leads to cross site scripting. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 2.4 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3804
Published : April 19, 2025, 4:15 p.m. | 12 hours, 38 minutes ago
Description : A vulnerability classified as critical has been found in thautwarm vscode-diana 0.0.1. Affected is an unknown function of the file Gen.py of the component Jinja2 Template Handler. The manipulation leads to injection. Attacking locally is a requirement. The exploit has been disclosed to the public and may be used.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3805
Published : April 19, 2025, 4:15 p.m. | 12 hours, 38 minutes ago
Description : A vulnerability classified as critical was found in sarrionandia tournatrack up to 4c13a23f43da5317eea4614870a7a8510fc540ec. Affected by this vulnerability is an unknown functionality of the file check_id.py of the component Jinja2 Template Handler. The manipulation of the argument ID leads to injection. It is possible to launch the attack on the local host. The exploit has been disclosed to the public and may be used. This product does not use versioning. This is why information about affected and unaffected releases are unavailable.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Cybersecurity researchers have uncovered three malicious packages in the npm registry that masquerade as a popular Telegram bot library but…
Cybercriminals lure content creators with promises of cutting-edge AI wizardry, only to attempt to steal their data or hijack their…
Cybersecurity researchers are warning of a “widespread and ongoing” SMS phishing campaign that’s been targeting toll road users in the…
Your employees didn’t mean to expose sensitive data. They just wanted to move faster. So they used ChatGPT to summarize…
A new multi-stage attack has been observed delivering malware families like Agent Tesla variants, Remcos RAT, and XLoader. “Attackers increasingly…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a medium-severity security flaw impacting Microsoft Windows to its…
Cybersecurity researchers are warning of continued risks posed by a distributed denial-of-service (DDoS) malware known as XorDDoS, with 71.3 percent…
Here’s what to know about malware that raids email accounts, web browsers, crypto wallets, and more – all in a…
The China-linked threat actor known as Mustang Panda has been attributed to a cyber attack targeting an unspecified organization in…
Microsoft is calling attention to an ongoing malvertising campaign that makes use of Node.js to deliver malicious payloads capable of…
Blockchain is best known for its use in cryptocurrencies like Bitcoin, but it also holds significant applications for online authentication.…


![[Webinar] AI Is Already Inside Your SaaS Stack — Learn How to Prevent the Next Silent Breach](https://devstacktips.com/wp-content/uploads/2025/04/ai-cyber-szbNJA-450x235.jpg)