The European Commission has introduced ProtectEU, a comprehensive European Internal Security Strategy aimed at strengthening the security of EU citizens.…
Security
Counterfeit versions of popular smartphone models that are sold at reduced prices have been found to be preloaded with a…
Cybersecurity researchers have disclosed details of a new vulnerability impacting Google’s Quick Share data transfer utility for Windows that could…
AI holds the promise to revolutionize all sectors of enterpriseーfrom fraud detection and content personalization to customer service and security…
The Cybersecurity and Infrastructure Security Agency (CISA) issued two crucial Industrial Control Systems (ICS) advisories, highlighting vulnerabilities that could have…
The rules have changed. Again. Artificial intelligence is bringing powerful new tools to businesses. But it’s also giving cybercriminals smarter…
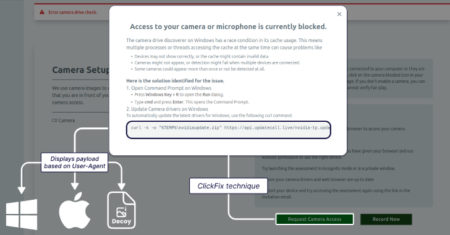
The North Korean threat actors behind Contagious Interview have adopted the increasingly popular ClickFix social engineering tactic to lure job…
The DragonForce ransomware group claims to be taking over the infrastructure of RansomHub, the largest ransomware group in the last…
Renowned cybersecurity expert Troy Hunt falls victim to a phishing attack, resulting in the exposure of thousands of subscriber details,…
Cybersecurity researchers have disclosed details of a now-patched privilege escalation vulnerability in Google Cloud Platform (GCP) Cloud Run that could…
Cybersecurity researchers have discovered an updated version of a malware loader called Hijack Loader that implements new features to evade…
The financially motivated threat actor known as FIN7 has been linked to a Python-based backdoor called Anubis (not to be…
In an effort to enhance Thailand’s cybersecurity infrastructure, the National Cyber Security Agency (NCSA) and Google Cloud have announced a…
When assessing an organization’s external attack surface, encryption-related issues (especially SSL misconfigurations) receive special attention. Why? Their widespread use, configuration…
Cybersecurity researchers have shed light on an “auto-propagating” cryptocurrency mining botnet called Outlaw (aka Dota) that’s known for targeting SSH…
Introduction As the cybersecurity landscape evolves, service providers play an increasingly vital role in safeguarding sensitive data and maintaining compliance…
Apple has released a series of critical security updates to address vulnerabilities that were actively exploited as zero-day threats. These…
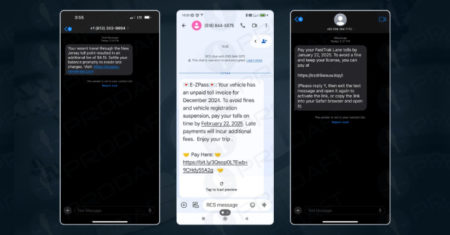
A new sophisticated phishing-as-a-service (PhaaS) platform called Lucid has targeted 169 entities in 88 countries using smishing messages propagated via…
In episode 44 of The AI Fix, ChatGPT won’t build a crystal meth lab, GPT-4o improves the show’s podcast art,…
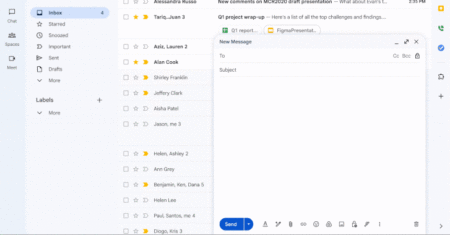
On the 21st birthday of Gmail, Google has announced a major update that allows enterprise users to send end-to-end encrypted…