The North Korean threat actors behind the ongoing Contagious Interview campaign are spreading their tentacles on the npm ecosystem by…
Security
Cybersecurity researchers have uncovered malicious libraries in the Python Package Index (PyPI) repository that are designed to steal sensitive information.…
A maximum severity security vulnerability has been disclosed in Apache Parquet’s Java Library that, if successfully exploited, could allow a…
The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that no less than three cyber attacks were recorded against…
A novice cybercrime actor has been observed leveraging the services of a Russian bulletproof hosting (BPH) provider called Proton66 to…
Ivanti has disclosed details of a now-patched critical security vulnerability impacting its Connect Secure that has come under active exploitation…
A series of cyberattack have impacted some of Australia’s largest superannuation funds, likely compromising over 20,000 member accounts. The authorities…
There’s a virtuous cycle in technology that pushes the boundaries of what’s being built and how it’s being used. A…
The cascading supply chain attack that initially targeted Coinbase before becoming more widespread to single out users of the “tj-actions/changed-files”…
Microsoft is warning of several phishing campaigns that are leveraging tax-related themes to deploy malware and steal credentials. “These campaigns…
HellCat – the ransomware gang that has been known to demand payment… in baguettes! Are they rolling in the dough?…
In one of the largest coordinated law enforcement operations, authorities have dismantled Kidflix, a streaming platform that offered child sexual…
Threat hunters are warning of a sophisticated web skimmer campaign that leverages a legacy application programming interface (API) from payment…
The European Commission has introduced ProtectEU, a comprehensive European Internal Security Strategy aimed at strengthening the security of EU citizens.…
Counterfeit versions of popular smartphone models that are sold at reduced prices have been found to be preloaded with a…
Cybersecurity researchers have disclosed details of a new vulnerability impacting Google’s Quick Share data transfer utility for Windows that could…
AI holds the promise to revolutionize all sectors of enterpriseーfrom fraud detection and content personalization to customer service and security…
The Cybersecurity and Infrastructure Security Agency (CISA) issued two crucial Industrial Control Systems (ICS) advisories, highlighting vulnerabilities that could have…
The rules have changed. Again. Artificial intelligence is bringing powerful new tools to businesses. But it’s also giving cybercriminals smarter…
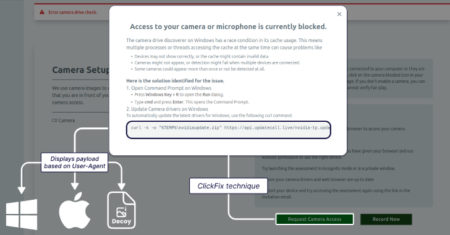
The North Korean threat actors behind Contagious Interview have adopted the increasingly popular ClickFix social engineering tactic to lure job…