Eric Council Jr. pleaded guilty to charges related to the January 2024 hack of the US Securities and Exchange Commission’s…
Security
Threat hunters have exposed the tactics of a China-aligned threat actor called UnsolicitedBooker that targeted an unnamed international organization in…
In the newly released 2025 State of Pentesting Report, Pentera surveyed 500 CISOs from global enterprises (200 from within the…
Cybersecurity researchers have discovered risky default identity and access management (IAM) roles impacting Amazon Web Services that could open the…
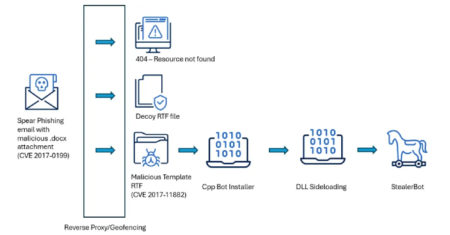
High-level government institutions in Sri Lanka, Bangladesh, and Pakistan have emerged as the target of a new campaign orchestrated by…
The logistics firm Peter Green Chilled, a key supplier to major UK supermarkets including Tesco, Sainsbury’s, and Aldi, fell victim…
CVE ID : CVE-2025-4951
Published : May 20, 2025, 9:15 a.m. | 2 hours, 52 minutes ago
Description : Editions of Rapid7 AppSpider Pro before version 7.5.018 is vulnerable to a stored cross-site scripting vulnerability in the “ScanName” field.
Despite the application preventing the inclusion of special characters within the “ScanName” field, this could be bypassed by modifying the configuration file directly.
This is fixed as of version 7.5.018
Severity: 4.6 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-37892
Published : May 20, 2025, 11:15 a.m. | 52 minutes ago
Description : In the Linux kernel, the following vulnerability has been resolved:
mtd: inftlcore: Add error check for inftl_read_oob()
In INFTL_findwriteunit(), the return value of inftl_read_oob()
need to be checked. A proper implementation can be
found in INFTL_deleteblock(). The status will be set as
SECTOR_IGNORE to break from the while-loop correctly
if the inftl_read_oob() fails.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-40633
Published : May 20, 2025, 11:15 a.m. | 52 minutes ago
Description : A Stored Cross-Site Scripting (XSS) vulnerability has been found in
Koibox for versions prior to e8cbce2. This vulnerability allows an
authenticated attacker to upload an image containing malicious
JavaScript code as profile picture in the
‘/es/dashboard/clientes/ficha/’ endpoint
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-40634
Published : May 20, 2025, 11:15 a.m. | 52 minutes ago
Description : Stack-based buffer overflow vulnerability in the ‘conn-indicator’ binary running as root on the TP-Link Archer AX50 router, in firmware versions prior to 1.0.15 build 241203 rel61480. This vulnerability allows an attacker to execute arbitrary code on the device over LAN and WAN networks.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-5878
Published : May 20, 2025, 8:15 a.m. | 20 minutes ago
Description : Multiple plugins for WordPress are vulnerable to Stored Cross-Site Scripting via the plugin’s bundled SimpleLightbox JavaScript library (version 2.1.5) in various versions due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4322
Published : May 20, 2025, 6:15 a.m. | 1 hour, 46 minutes ago
Description : The Motors theme for WordPress is vulnerable to privilege escalation via account takeover in all versions up to, and including, 5.6.67. This is due to the theme not properly validating a user’s identity prior to updating their password. This makes it possible for unauthenticated attackers to change arbitrary user passwords, including those of administrators, and leverage that to gain access to their account.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-2929
Published : May 20, 2025, 6:15 a.m. | 1 hour, 46 minutes ago
Description : The Order Delivery Date WordPress plugin before 12.4.0 does not sanitise and escape a parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
SonicWall has released patches to address three security flaws affecting SMA 100 Secure Mobile Access (SMA) appliances that could be…
A China-linked unnamed threat actor dubbed Chaya_004 has been observed exploiting a recently disclosed security flaw in SAP NetWeaver. Forescout…
Bloomin’ eck! I’m delighted to share with you that “The AI Fix” is up for an award! Source: Read More
Several ransomware actors are using a malware called Skitnet as part of their post-exploitation efforts to steal sensitive data and…
The official site for RVTools has been hacked to serve a compromised installer for the popular VMware environment reporting utility.…
More than 100 groups and individuals banded together today to oppose any changes to the EU’s landmark General Data Protection…
The UK’s National Health Service (NHS) is asking its IT suppliers to commit to better cybersecurity by signing a public…