A flaw has been discovered in OpenPGP.js, a widely used JavaScript library for OpenPGP encryption. Tracked as CVE-2025-47934, the vulnerability…
Security
A sprawling operation undertaken by global law enforcement agencies and a consortium of private sector firms has disrupted the online…
Crypto fraud meets cuddly toys! US authorities have charged a group accused of stealing $263 million in cryptocurrency – and…
Google’s quiet rollout of its AI-powered Gemini chatbot to children under the age of 13 has sparked intense debate or…
Cellcom, a regional wireless provider based in Wisconsin, is continuing efforts to restore full service following a cybersecurity incident that…
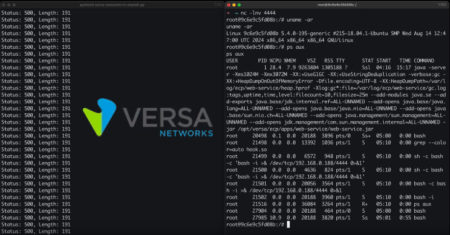
Cybersecurity researchers have uncovered multiple critical security vulnerabilities impacting the Versa Concerto network security and SD-WAN orchestration platform that could…
For many organizations, identity security appears to be under control. On paper, everything checks out. But new research from Cerby,…
It’s not enough to be secure. In today’s legal climate, you need to prove it. Whether you’re protecting a small…
A recently patched pair of security flaws affecting Ivanti Endpoint Manager Mobile (EPMM) software has been exploited by a China-nexus…
A privilege escalation flaw has been demonstrated in Windows Server 2025 that makes it possible for attackers to compromise any…
A Chinese-speaking threat actor tracked as UAT-6382 has been linked to the exploitation of a now-patched remote-code-execution vulnerability in Trimble…
CVE ID : CVE-2025-4642
Published : May 22, 2025, 11:15 p.m. | 1 hour, 35 minutes ago
Description : Rejected reason: This CVE ID has been rejected or withdrawn by its CVE Numbering Authority.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48371
Published : May 22, 2025, 11:15 p.m. | 1 hour, 35 minutes ago
Description : OpenFGA is an authorization/permission engine. OpenFGA versions 1.8.0 through 1.8.12 (corresponding to Helm chart openfga-0.2.16 through openfga-0.2.30 and docker 1.8.0 through 1.8.12) are vulnerable to authorization bypass when certain Check and ListObject calls are executed. Users are affected under four specific conditions: First, calling Check API or ListObjects with an authorization model that has a relationship directly assignable by both type bound public access and userset; second, there are check or list object queries with contextual tuples for the relationship that can be directly assignable by both type bound public access and userset; third, those contextual tuples’s user field is an userset; and finally, type bound public access tuples are not assigned to the relationship. Users should upgrade to version 1.8.13 to receive a patch. The upgrade is backwards compatible.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4338
Published : May 22, 2025, 11:15 p.m. | 1 hour, 35 minutes ago
Description : Lantronix Device installer is vulnerable to XML external entity (XXE) attacks in configuration files read from the network device. An attacker could obtain credentials, access these network devices, and modify their configurations. An attacker may also gain access to the host running the Device Installer software or the password hash of the user running the application.
Severity: 6.8 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4562
Published : May 22, 2025, 11:15 p.m. | 1 hour, 35 minutes ago
Description : Rejected reason: This CVE ID has been rejected or withdrawn by its CVE Numbering Authority.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4692
Published : May 23, 2025, 12:15 a.m. | 35 minutes ago
Description : Actors can use a maliciously crafted JavaScript object notation (JSON) web token (JWT) to perform privilege escalation by submitting the malicious JWT to a vulnerable method exposed on the cloud platform. If the exploit is successful, the user can escalate privileges to access any device managed by the
ABUP Cloud Update Platform.
Severity: 6.8 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48372
Published : May 22, 2025, 9:15 p.m. | 1 hour, 36 minutes ago
Description : Schule is open-source school management system software. The generateOTP() function generates a 4-digit numeric One-Time Password (OTP). Prior to version 1.0.1, even if a secure random number generator is used, the short length and limited range (1000–9999) results in only 9000 possible combinations. This small keyspace makes the OTP highly vulnerable to brute-force attacks, especially in the absence of strong rate-limiting or lockout mechanisms. Version 1.0.1 fixes the issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48373
Published : May 22, 2025, 9:15 p.m. | 1 hour, 36 minutes ago
Description : Schule is open-source school management system software. The application relies on client-side JavaScript (index.js) to redirect users to different panels based on their role. Prior to version 1.0.1, this implementation poses a serious security risk because it assumes that the value of data.role is trustworthy on the client side. Attackers can manipulate JavaScript in the browser (e.g., via browser dev tools or intercepting API responses) and set data.role to any arbitrary value (e.g., “admin”), gaining unauthorized access to restricted areas of the application.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48374
Published : May 22, 2025, 9:15 p.m. | 1 hour, 36 minutes ago
Description : zot is ancontainer image/artifact registry based on the Open Container Initiative Distribution Specification. Prior to version 2.1.3 (corresponding to pseudoversion 1.4.4-0.20250522160828-8a99a3ed231f), when using Keycloak as an oidc provider, the clientsecret gets printed into the container stdout logs for an example at container startup. Version 2.1.3 (corresponding to pseudoversion 1.4.4-0.20250522160828-8a99a3ed231f) fixes the issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47181
Published : May 22, 2025, 10:15 p.m. | 36 minutes ago
Description : Improper link resolution before file access (‘link following’) in Microsoft Edge (Chromium-based) allows an authorized attacker to elevate privileges locally.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…