Apple, in its latest App Store fraud analysis, revealed that the company prevented more than $2 billion in potentially fraudulent…
Security
Cybersecurity researchers have disclosed details of a coordinated cloud-based scanning activity that targeted 75 distinct “exposure points” earlier this month.…
Would you expect an end user to log on to a cybercriminal’s computer, open their browser, and type in their…
A financially motivated threat actor has been observed exploiting a recently disclosed remote code execution flaw affecting the Craft Content…
Stealer malware no longer just steals passwords. In 2025, it steals live sessions—and attackers are moving faster and more efficiently…
Embedded Linux-based Internet of Things (IoT) devices have become the target of a new botnet dubbed PumaBot. Written in Go,…
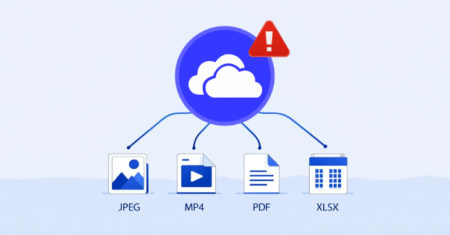
Cybersecurity researchers have discovered a security flaw in Microsoft’s OneDrive File Picker that, if successfully exploited, could allow websites to…
The Czech Republic on Wednesday formally accused a threat actor associated with the People’s Republic of China (PRC) of targeting…
An Iranian national has pleaded guilty in the U.S. over his involvement in an international ransomware and extortion scheme involving…
As estimates of the quantum computing power needed to crack current public key encryption algorithms continue to drop, a group…
Why is a cute Star Wars fan website now redirecting to the CIA? How come Cambodia has become the world’s…
Cybersecurity researchers have disclosed a critical unpatched security flaw impacting TI WooCommerce Wishlist plugin for WordPress that could be exploited…
Google on Wednesday disclosed that the Chinese state-sponsored threat actor known as APT41 leveraged a malware called TOUGHPROGRESS that uses…
The threat actors behind the DragonForce ransomware gained access to an unnamed Managed Service Provider’s (MSP) SimpleHelp remote monitoring and…
CVE ID : CVE-2025-48388
Published : May 29, 2025, 10:15 a.m. | 3 hours, 16 minutes ago
Description : FreeScout is a free self-hosted help desk and shared mailbox. Prior to version 1.8.178, the application performs insufficient validation of user-supplied data, which is used as arguments to string formatting functions. As a result, an attacker can pass a string containing special symbols (r, n, t)to the application. This issue has been patched in version 1.8.178.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48045
Published : May 29, 2025, 1:15 p.m. | 16 minutes ago
Description : An unauthenticated HTTP GET request to the /client.php endpoint will disclose the default administrator user credentials.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48046
Published : May 29, 2025, 1:15 p.m. | 16 minutes ago
Description : An authenticated user can disclose the cleartext password of a configured SMTP server via an HTTP GET request to the /config.php endpoint.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48047
Published : May 29, 2025, 1:15 p.m. | 16 minutes ago
Description : An authenticated user can perform command injection via unsanitized input to the NetFax Server’s ping functionality via the /test.php endpoint.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-52588
Published : May 29, 2025, 9:15 a.m. | 15 minutes ago
Description : Strapi is an open-source content management system. Prior to version 4.25.2, inputting a local domain into the Webhooks URL field leads to the application fetching itself, resulting in a server side request forgery (SSRF). This issue has been patched in version 4.25.2.
Severity: 4.9 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-27151
Published : May 29, 2025, 9:15 a.m. | 15 minutes ago
Description : Redis is an open source, in-memory database that persists on disk. In versions starting from 7.0.0 to before 8.0.2, a stack-based buffer overflow exists in redis-check-aof due to the use of memcpy with strlen(filepath) when copying a user-supplied file path into a fixed-size stack buffer. This allows an attacker to overflow the stack and potentially achieve code execution. This issue has been patched in version 8.0.2.
Severity: 4.7 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…