A security weakness has been disclosed in the artificial intelligence (AI)-powered code editor Cursor that could trigger code execution when…
Security
UEFI copycat of Petya/NotPetya exploiting CVE-2024-7344 discovered on VirusTotal Source: Read More
The U.S. Federal Bureau of Investigation (FBI) has issued a flash alert to release indicators of compromise (IoCs) associated with…
Over half of insider cyber incidents in UK schools are being caused by students—a trend raising alarms across education, regulation,…
The U.S. Federal Trade Commission has opened a formal inquiry into AI chatbots that act like companions—designed to mimic emotions,…
The security landscape for cloud-native applications is undergoing a profound transformation. Containers, Kubernetes, and serverless technologies are now the default…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting Dassault Systèmes DELMIA Apriso…
Cybercrime and online scams have officially overtaken traditional threats as the primary regional security concern for the Association of Southeast…
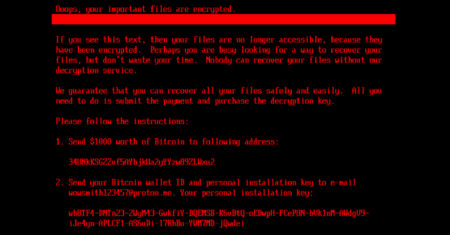
Cybersecurity researchers have discovered a new ransomware strain dubbed HybridPetya that resembles the notorious Petya/NotPetya malware, while also incorporating the…
Apple has notified users in France of a spyware campaign targeting their devices, according to the Computer Emergency Response Team…
Samsung has released its monthly security updates for Android, including a fix for a security vulnerability that it said has…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a manufacturing operations management software vulnerability to its Known Exploited…
Cybersecurity researchers have disclosed details of a new campaign that leverages ConnectWise ScreenConnect, a legitimate Remote Monitoring and Management (RMM)…
As bad actors often simply waltz through companies’ digital front doors with a key, here’s how to keep your own…
Cybersecurity researchers have disclosed two new campaigns that are serving fake browser extensions using malicious ads and fake websites to…
CISOs know their field. They understand the threat landscape. They understand how to build a strong and cost-effective security stack.…
Threat actors affiliated with the Akira ransomware group have continued to target SonicWall devices for initial access. Cybersecurity firm Rapid7…
The Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) has issued an urgent alert regarding active exploitation of a…
A fresh firestorm has erupted over Microsoft’s handling of cybersecurity risks, with U.S. Senator Ron Wyden (D-OR) calling on the…
SAP has released a new security update addressing a broad range of vulnerabilities across its product ecosystem. Among the most…