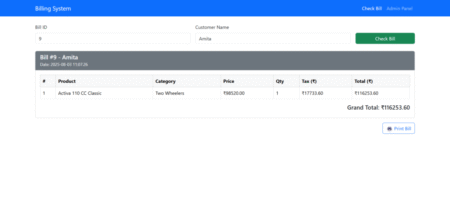
The Billing System using PHP and MySQL is a role-based application designed to streamline and automate the process of billing…
Development
Comments Source: Read MoreÂ
CVE ID : CVE-2025-6076
Published : Aug. 2, 2025, 3:15 a.m. | 2 days, 22 hours ago
Description : Partner Software’s Partner Software application and Partner Web application do not sanitize files uploaded on the “reports” tab, allowing an authenticated attacker to upload a malicious file and compromise the device. By default, the software runs as SYSTEM, heightening the severity of the vulnerability.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-20700
Published : Aug. 4, 2025, 7:15 a.m. | 18 hours, 5 minutes ago
Description : In the Airoha Bluetooth audio SDK, there is a possible permission bypass that allows access critical data of RACE protocol through Bluetooth LE GATT service. This could lead to remote escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-20701
Published : Aug. 4, 2025, 7:15 a.m. | 18 hours, 5 minutes ago
Description : In the Airoha Bluetooth audio SDK, there is a possible way to pair Bluetooth audio device without user consent. This could lead to remote escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-20702
Published : Aug. 4, 2025, 7:15 a.m. | 18 hours, 5 minutes ago
Description : In the Airoha Bluetooth audio SDK, there is a possible unauthorized access to the RACE protocol. This could lead to remote escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-41659
Published : Aug. 4, 2025, 8:15 a.m. | 17 hours, 5 minutes ago
Description : A low-privileged attacker can remotely access the PKI folder of the CODESYS Control runtime system and thus read and write certificates and its keys. This allows sensitive data to be extracted or to accept certificates as trusted. Although all services remain available, only unencrypted communication is possible if the certificates are deleted.
Severity: 8.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6204
Published : Aug. 4, 2025, 10:15 a.m. | 15 hours, 5 minutes ago
Description : An Improper Control of Generation of Code (Code Injection) vulnerability affecting DELMIA Apriso from Release 2020 through Release 2025 could allow an attacker to execute arbitrary code.
Severity: 8.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6205
Published : Aug. 4, 2025, 10:15 a.m. | 15 hours, 5 minutes ago
Description : A missing authorization vulnerability affecting DELMIA Apriso from Release 2020 through Release 2025 could allow an attacker to gain privileged access to the application.
Severity: 9.1 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44643
Published : Aug. 4, 2025, 3:15 p.m. | 10 hours, 5 minutes ago
Description : Certain Draytek products are affected by Insecure Configuration. This affects AP903 v1.4.18 and AP912C v1.4.9 and AP918R v1.4.9. The setting of the password property in the ripd.conf configuration file sets a hardcoded weak password, posing a security risk. An attacker with network access could exploit this to gain unauthorized control over the routing daemon, potentially altering network routes or intercepting traffic.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-51536
Published : Aug. 4, 2025, 3:15 p.m. | 10 hours, 5 minutes ago
Description : Austrian Archaeological Institute (AI) OpenAtlas v8.11.0 as discovered to contain a hardcoded Administrator password.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-36594
Published : Aug. 4, 2025, 3:15 p.m. | 10 hours, 5 minutes ago
Description : Dell PowerProtect Data Domain with Data Domain Operating System (DD OS) of Feature Release versions 7.7.1.0 through 8.3.0.15, LTS2024 release Versions 7.13.1.0 through 7.13.1.25, LTS 2023 release versions 7.10.1.0 through 7.10.1.60, contain an Authentication Bypass by Spoofing vulnerability. An unauthenticated attacker with remote access could potentially exploit this vulnerability, leading to Protection mechanism bypass. Remote unauthenticated user can create account that potentially expose customer info, affect system integrity and availability.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44955
Published : Aug. 4, 2025, 4:15 p.m. | 9 hours, 5 minutes ago
Description : RUCKUS Network Director (RND) before 4.5 allows jailed users to obtain root access vis a weak, hardcoded password.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44954
Published : Aug. 4, 2025, 5:15 p.m. | 8 hours, 5 minutes ago
Description : RUCKUS SmartZone (SZ) before 6.1.2p3 Refresh Build has a hardcoded SSH private key for a root-equivalent user account.
Severity: 9.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44957
Published : Aug. 4, 2025, 5:15 p.m. | 8 hours, 5 minutes ago
Description : Ruckus SmartZone (SZ) before 6.1.2p3 Refresh Build allows authentication bypass via a valid API key and crafted HTTP headers.
Severity: 8.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44960
Published : Aug. 4, 2025, 5:15 p.m. | 8 hours, 5 minutes ago
Description : RUCKUS SmartZone (SZ) before 6.1.2p3 Refresh Build allows OS command injection via a certain parameter in an API route.
Severity: 8.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44961
Published : Aug. 4, 2025, 5:15 p.m. | 8 hours, 5 minutes ago
Description : In RUCKUS SmartZone (SZ) before 6.1.2p3 Refresh Build, OS command injection can occur via an IP address field provided by an authenticated user.
Severity: 9.9 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44963
Published : Aug. 4, 2025, 5:15 p.m. | 8 hours, 5 minutes ago
Description : RUCKUS Network Director (RND) before 4.5 allows spoofing of an administrator JWT by an attacker who knows the hardcoded value of a certain secret key.
Severity: 9.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-21120
Published : Aug. 4, 2025, 7:15 p.m. | 6 hours, 5 minutes ago
Description : Dell Avamar, versions prior to 19.12 with patch 338905, excluding version 19.10SP1 with patch 338904, contains a Trusting HTTP Permission Methods on the Server-Side vulnerability in Security. A low privileged attacker with remote access could potentially exploit this vulnerability, leading to Information exposure.
Severity: 8.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-26476
Published : Aug. 4, 2025, 7:15 p.m. | 6 hours, 5 minutes ago
Description : Dell ECS versions prior to 3.8.1.5/ ObjectScale version 4.0.0.0, contain a Use of Hard-coded Cryptographic Key vulnerability. An unauthenticated attacker with local access could potentially exploit this vulnerability, leading to Unauthorized access.
Severity: 8.4 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…