Meet Acquia Source Acquia Source powered by Drupal is Acquia’s SaaS solution to streamline building, managing, and deploying websites at…
Development
In the face of economic uncertainty, shifting buyer expectations, and rapid technological change, manufacturing marketers must evolve to stay competitive.…
SonicWall said it’s actively investigating reports to determine if there is a new zero-day vulnerability following reports of a spike…
To protect digital privacy, the UAE Cybersecurity Council has issued a strict warning against the use of unofficial and unverified…
Cybersecurity researchers have lifted the veil on a widespread malicious campaign that’s targeting TikTok Shop users globally with an aim…
Why do SOC teams still drown in alerts even after spending big on security tools? False positives pile up, stealthy…
In SaaS security conversations, “misconfiguration” and “vulnerability” are often used interchangeably. But they’re not the same thing. And misunderstanding that…
Cybersecurity researchers have disclosed a high-severity security flaw in the artificial intelligence (AI)-powered code editor Cursor that could result in…
Google has released security updates to address multiple security flaws in Android, including fixes for two Qualcomm bugs that were…
In episode 62 of The AI Fix, your hosts learn how AI models smash through CAPTCHA roadblocks like they’re made…
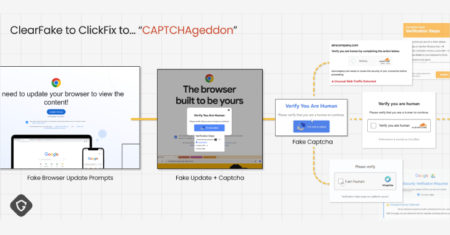
A combination of propagation methods, narrative sophistication, and evasion techniques enabled the social engineering tactic known as ClickFix to take…
In Agile software development, the demand for high-quality test data is crucial, but traditional production data often leads to bottlenecks due to privacy and compliance concerns. Synthetic test data, generated by AI, offers a secure, flexible alternative by mimicking real data without exposing sensitive information. It speeds up testing, improves coverage, and uncovers edge cases missed by traditional data. With synthetic data, teams can quickly generate tailored datasets for each test scenario, reducing waiting times and improving efficiency. Embracing synthetic test data helps businesses accelerate delivery, enhance product quality, and innovate faster.
The post Break Free from Legacy Bottlenecks – How Synthetic Test Data Fuels Agile Innovation first appeared on TestingXperts.
Imagine this familiar scene: it’s Friday evening, and your team is prepping a hot-fix release. The code passes unit tests, the sprint board is almost empty, and you’re already tasting weekend freedom. Suddenly, a support ticket pings:“Screen-reader users can’t reach the checkout button. The focus keeps looping back to the promo banner.”The clock is ticking,
The post AI in Accessibility Testing: The Future Awaits appeared first on Codoid.
Today, we’re proud to introduce NodeSource Certified Modules v3 (NCM v3): a complete rearchitecture of our module scanning and observability…
CVE ID : CVE-2025-51534
Published : Aug. 4, 2025, 5:15 p.m. | 1 day, 6 hours ago
Description : A cross-site scripting (XSS) vulnerability in Austrian Archaeological Institute (AI) OpenAtlas v8.11.0 allows attackers to execute arbitrary web scripts or HTML via injecting a crafted payload into the Name field.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-51535
Published : Aug. 4, 2025, 5:15 p.m. | 1 day, 6 hours ago
Description : Austrian Archaeological Institute (AI) OpenAtlas v8.11.0 as discovered to contain a SQL injection vulnerability.
Severity: 9.1 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-51390
Published : Aug. 4, 2025, 6:15 p.m. | 1 day, 5 hours ago
Description : TOTOLINK N600R V4.3.0cu.7647_B20210106 was discovered to contain a command injection vulnerability via the pin parameter in the setWiFiWpsConfig function.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54119
Published : Aug. 5, 2025, 1:15 a.m. | 22 hours, 26 minutes ago
Description : ADOdb is a PHP database class library that provides abstractions for performing queries and managing databases. In versions 5.22.9 and below, improper escaping of a query parameter may allow an attacker to execute arbitrary SQL statements when the code using ADOdb connects to a sqlite3 database and calls the metaColumns(), metaForeignKeys() or metaIndexes() methods with a crafted table name. This is fixed in version 5.22.10. To workaround this issue, only pass controlled data to metaColumns(), metaForeignKeys() and metaIndexes() method’s $table parameter.
Severity: 10.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54135
Published : Aug. 5, 2025, 1:15 a.m. | 22 hours, 26 minutes ago
Description : Cursor is a code editor built for programming with AI. Cursor allows writing in-workspace files with no user approval in versions below 1.3.9, If the file is a dotfile, editing it requires approval but creating a new one doesn’t. Hence, if sensitive MCP files, such as the .cursor/mcp.json file don’t already exist in the workspace, an attacker can chain a indirect prompt injection vulnerability to hijack the context to write to the settings file and trigger RCE on the victim without user approval. This is fixed in version 1.3.9.
Severity: 8.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54802
Published : Aug. 5, 2025, 1:15 a.m. | 22 hours, 26 minutes ago
Description : pyLoad is the free and open-source Download Manager written in pure Python. In versions 0.5.0b3.dev89 and below, there is an opportunity for path traversal in pyLoad-ng CNL Blueprint via package parameter, allowing Arbitrary File Write which leads to Remote Code Execution (RCE). The addcrypted endpoint in pyload-ng suffers from an unsafe path construction vulnerability, allowing unauthenticated attackers to write arbitrary files outside the designated storage directory. This can be abused to overwrite critical system files, including cron jobs and systemd services, leading to privilege escalation and remote code execution as root. This issue is fixed in version 0.5.0b3.dev90.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…