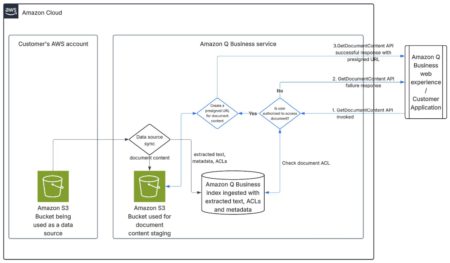
CVE ID : CVE-2025-51058
Published : Aug. 6, 2025, 9:15 p.m. | 3 hours, 47 minutes ago
Description : Bottinelli Informatical Vedo Suite 2024.17 is vulnerable to Server-side Request Forgery (SSRF) in the /api_vedo/video/preview endpoint, which allows remote authenticated attackers to trigger HTTP requests towards arbitrary remote paths via the “file” URL parameter.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…