Successfully translating a Figma design into a Flutter application requires more than just placing elements on the screen. The objective…
Development
Prepare for the Google Cloud Associate Cloud Engineer (ACE) exam and pass! We just published an updated Google Cloud Associate…
Learning about time series forecasting in Python is important because it can help predict future trends. We just posted a…
On this week’s episode of the podcast, freeCodeCamp founder Quincy Larson interviews Edidiong Asikpo. Didi is a software engineer. She…
Getting the “spawn python ENOENT” error while setting up an MCP (Model Context Protocol) server on macOS can be frustrating.…
This blog continues the IoT platform setup by explaining how to install and run the Stream application, which collects incoming…
Success in cybersecurity is when nothing happens, plus other standout themes from two of the event’s keynotes Source: Read More
Who’s to blame when the AI tool managing a company’s compliance status gets it wrong? Source: Read More
A newly discovered campaign dubbed GreedyBear has leveraged over 150 malicious extensions to the Firefox marketplace that are designed to…
TeaOnHer hasn’t stopped at copying the functionality of the original Tea app (albeit skewed towards men rating women). It also…
A fresh set of 60 malicious packages has been uncovered targeting the RubyGems ecosystem by posing as seemingly innocuous automation…
When an organization’s credentials are leaked, the immediate consequences are rarely visible—but the long-term impact is far-reaching. Far from the…
The Australian Information Commissioner has launched civil penalty proceedings against telecommunications giant Optus over the massive 2022 data breach that…
Cybersecurity researchers are drawing attention to a new campaign that’s using legitimate generative artificial intelligence (AI)-powered website building tools like…
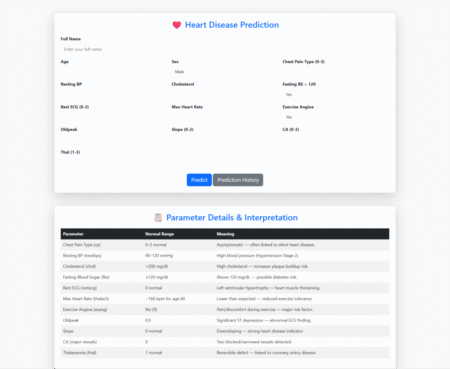
Heart Disease Prediction using Python & Machine Learning is a final-year academic project that uses medical data and ML algorithms…
#748 — August 8, 2025 Read on the Web ☀️ We’re taking next week off, so this will be the…
CVE ID : CVE-2025-50692
Published : Aug. 7, 2025, 7:15 p.m. | 1 day, 4 hours ago
Description : FoxCMS
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54886
Published : Aug. 8, 2025, 1:15 a.m. | 22 hours, 44 minutes ago
Description : skops is a Python library which helps users share and ship their scikit-learn based models. In versions 0.12.0 and below, the Card.get_model does not contain any logic to prevent arbitrary code execution. The Card.get_model function supports both joblib and skops for model loading. When loading .skops models, it uses skops’ secure loading with trusted type validation, raising errors for untrusted types unless explicitly allowed. However, when non-.zip file formats are provided, the function silently falls back to joblib without warning. Unlike skops, joblib allows arbitrary code execution during loading, bypassing security measures and potentially enabling malicious code execution. This issue is fixed in version 0.13.0.
Severity: 8.4 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54887
Published : Aug. 8, 2025, 1:15 a.m. | 22 hours, 44 minutes ago
Description : jwe is a Ruby implementation of the RFC 7516 JSON Web Encryption (JWE) standard. In versions 1.1.0 and below, authentication tags of encrypted JWEs can be brute forced, which may result in loss of confidentiality for those JWEs and provide ways to craft arbitrary JWEs. This puts users at risk because JWEs can be modified to decrypt to an arbitrary value, decrypted by observing parsing differences and the GCM internal GHASH key can be recovered. Users are affected by this vulnerability even if they do not use an AES-GCM encryption algorithm for their JWEs. As the GHASH key may have been leaked, users must rotate the encryption keys after upgrading. This issue is fixed in version 1.1.1.
Severity: 9.1 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48913
Published : Aug. 8, 2025, 10:15 a.m. | 13 hours, 44 minutes ago
Description : If untrusted users are allowed to configure JMS for Apache CXF, previously they could use RMI or LDAP URLs, potentially leading to code execution capabilities. This interface is now restricted to reject those protocols, removing this possibility.
Users are recommended to upgrade to versions 3.6.8, 4.0.9 or 4.1.3, which fix this issue.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…



![Abandoning med school to become a software engineer with Edidiong Asikpo [Podcast #182]](https://devstacktips.com/wp-content/uploads/2025/08/fb546ee8-d9fd-4ec7-895b-def935be4649-AdW2cu-450x253.png)