Embracing Diversity: The Impact of Usability and UX on Diverse User Groups In this installment of our Usability and Experience…
Development
Intro Last week, I noticed that deployments to Sitecore XM Cloud were failing on one of my projects. In this…
At Perficient, we are proud to have a diverse and talented team spanning the globe, working together to build the…
Importance of Product Data in Driving Sales When you don’t have a storefront and a salesperson to do the talking,…
In the rapidly evolving landscape of B2B commerce, achieving success hinges on strategic prowess. As a Product Owner of one…
Creating a DateTime from a Unix timestamp will be more convenient in PHP 8.4 with the new createFromTimestamp() method. It…
Discover how to effectively master Vue Router in Vue.js 3 using the powerful Composition API. Continue reading on Vue.js Feed…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a comprehensive set of advisories to secure Industrial Control Systems…
Google’s plans to deprecate third-party tracking cookies in its Chrome web browser with Privacy Sandbox has run into fresh trouble…
As anticipation builds for the upcoming Paris 2024 Summer Olympic Games, security researchers and officials have observed an uptick in…
Ukraine’s Security Service (SBU) detained two individuals accused of aiding Russian intelligence in hacking the phones of Ukrainian soldiers and…
The Cyber Express, in collaboration with Cyble Research & Intelligence Labs (CRIL), is dedicated to providing the latest and most…
Europol coordinated two separate operations this week to disrupt 13 websites used in spreading terrorist propaganda online. This action followed…
June 13, 2024 may go down as one of the tougher days in Microsoft’s long history. The day started with…
The UK, US and Canada have accused Russia of an elaborate plot to interfere in Moldova’s upcoming presidential election and…
Globe Life disclosed a recent cybersecurity incident that may have resulted in unauthorized access to its consumer and policyholder information.…
A 22-year-old British national, allegedly the leader of an organized cybercrime group that targeted nearly four dozen U.S. companies, was…
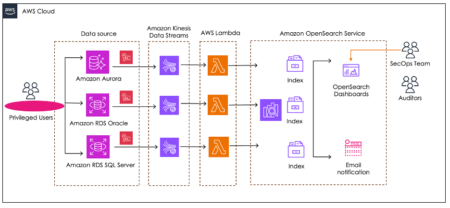
Data is any company’s most valuable asset today, and securing it is critical. Organizations in regulated industries such as healthcare…
Artificial Intelligence (AI) is revolutionizing software development by enhancing productivity, improving code quality, and automating routine tasks. Developers now have…
Developing large language models requires substantial investments in time and GPU resources, translating directly into high costs. The larger the…