The Amazon rainforest hummed with a thousand unseen lives as Rohan, Diya, Sameer, and Priya set up their summer camp.…
Development
The old house groaned around them, a symphony of settling bones. But it wasn’t the creaks or the shadows that…
The first time I saw the red car, I was walking home from Maya’s house, cutting through the old cemetery…
My scream died in my throat, choked by the impossible sight of my own monstrous, green hands. The Red Car…
Chandru, a man who loved the sharp crack of a leather ball on a willow bat more than most things,…
In this tutorial, we dive deep into the advanced capabilities of OpenBB to perform comprehensive portfolio analysis and market intelligence.…
Table of contents Cloud & API Providers DeepSeek Official API Amazon Bedrock (AWS) Together AI Novita AI Fireworks AI Other…
China continues to set the pace in open-source large-language-model innovation, especially for agentic architectures and deep reasoning. Here is a…
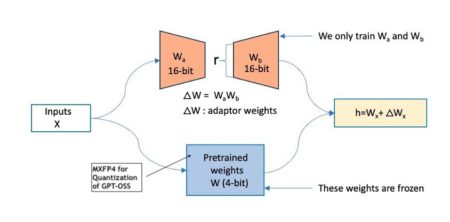
Released on August 5, 2025, OpenAI’s GPT-OSS models, gpt-oss-20b and gpt-oss-120b, are now available on AWS through Amazon SageMaker AI…
“How much will it cost to run our chatbot on Amazon Bedrock?” This is one of the most frequent questions…
Embodied AI agents that can perceive, think, and act in the real world mark a key step toward the future…
NuMind AI has officially released NuMarkdown-8B-Thinking, an open-source (MIT License) reasoning OCR Vision-Language Model (VLM) that redefines how complex documents…
In this tutorial, we walk through building a compact but fully functional Cipher-based workflow. We start by securely capturing our…
Corpus Aware Training (CAT) leverages valuable corpus metadata during training by injecting corpus information into each training example, and has…
Discover some of the interesting features that have landed in stable and beta web browsers during July 2025. Source: web.dev:…
Read about various happenings with Baseline during July 2025. Source: web.dev: BlogÂ
Baseline information is now available for CSS properties in the Elements panel of Chrome DevTools! Source: web.dev: BlogÂ
For most of people, JavaScript still conjures images of simple web interactions like toggling menus, validating forms, or animating buttons.…
Introduction: The Evolution from Automation to Intelligence Imagine a world where your software tools don’t just do what you tell…
In earlier blogs – Why AI-Led Experiences Are the Future — And How Sitecore Stream Delivers Them and Creating a…